
Cring ransomware attacking vulnerable Fortigate VPNs
A vulnerability impacting Fortinet's Fortigate VPN, first disclosed and patched in 2019, is being exploited by Cring ransomware operators to extort bitcoin from enterprises.
A vulnerability in Fortinet's Fortigate VPN is being exploited by Cring ransomware threat actors, according to a report published days after a Cybersecurity and Infrastructure Security Agency advisory warned that several FortiOS flaws were being utilized in cyber attacks.
Kaspersky Lab's ICS CERT, a project dedicated to industrial cybersecurity threats, released a report Wednesday showing that the prolifically exploited CVE-2018-13379, a path traversal vulnerability in FortiOS first disclosed in the spring of 2019, was being used in Cring ransomware attacks. The vulnerability has been previously exploited by other threat actors, including suspected nation-state adversaries in the fall of 2019.
According to the report, the victims of these latest attacks include European industrial enterprises, and in at least one case, a victim experienced "a temporary shutdown of the industrial process due to servers used to control the industrial process becoming encrypted."
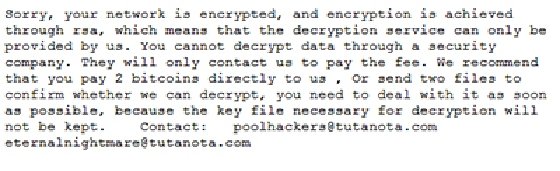
Cring was first reported in January, with its earliest known activity dating back to December 2020. Kaspersky Lab noted in its report that the ransomware used MimiKatz and Cobalt Strike -- two hacking tools used for penetration testing -- for lateral movement within a victim's network. Threat actors have demanded two bitcoin in Cring ransom notes, which is currently the equivalent to approximately $115,000.
The report further mentioned that when the attackers ran a command script dubbed "kaspersky" to launch the ransomware. "The attackers used this technique to mask the traces of the malware activity and disguise the operation of the malware as that of security solutions," the report said.
CVE-2018-13379, which received a 9.8 CVSS score, was originally discovered in 2018 by Meh Chang and anonymous researcher "Orange Tsai" of DevCore, an infosec consultancy in Taiwan. Although the flaw was patched in May 2019, unpatched VPNs have been attacked on several occasions. Kaspersky's report called attention to a dark web forum post from the fall of 2020 claiming to provide a database of vulnerable devices.
Vyacheslav Kopeytsev, senior security researcher at Kaspersky ICS CERT, told SearchSecurity in an email that the database included 50,000 devices, but could not confirm the database's authenticity.
A joint cybersecurity advisory published last Friday by the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI warned that APTs were exploiting multiple Fortinet vulnerabilities including CVE-2018-13379. However, the advisory made no mention of actual attacks -- only scanning for unpatched devices.
Kopeytsev said that while Fortinet has "done a good job of fixing the vulnerability and informing users about the threat," not all users have updated their software, as the report shows.
"It is common for industrial enterprises to have issues with installing updates. In most cases, the reason is that before being installed, an update must be extensively tested. Sometimes installation is only possible during maintenance," he said. "However, in this case, a VPN server was affected, which was not part of the industrial process. This could mean that the failure to install updates might have to do with insufficient attention to information security."
Fortinet declined to comment on the Cring ransomware attacks, or the number of customers who hadn't patched CVE-2018-13379. A company spokesperson responded with a similar statement to one given to SearchSecurity earlier this week, which outlined the steps Fortinet has taken to address the vulnerability and encouraged customers to immediately patch and mitigate the flaw.
"The security of our customers is our first priority. For example, CVE-2018-13379 is an old vulnerability resolved in May 2019. Fortinet immediately issued a PSIRT advisory and communicated directly with customers and via corporate blog posts on multiple occasions in August 2019, July 2020, and again in April 2021 strongly recommending an upgrade. Upon resolution we have consistently communicated with customers as recently as April 2021. To get more information, please visit our blog and immediately refer to the May 2019 advisory. If customers have not done so, we urge them to immediately implement the upgrade and mitigations," the statement read.
Alexander Culafi is a writer, journalist and podcaster based in Boston.





