
Ransomware gangs increasingly exploiting vulnerabilities
New research from Cisco Talos highlighted three of the most popular known vulnerabilities that were exploited by ransomware gangs for initial access during 2023 and 2024.
Listen to this article. This audio was generated by AI.
Ransomware groups have increasingly exploited known and zero-day vulnerabilities to gain initial access to victim organizations over the past year, according to new research from Cisco Talos.
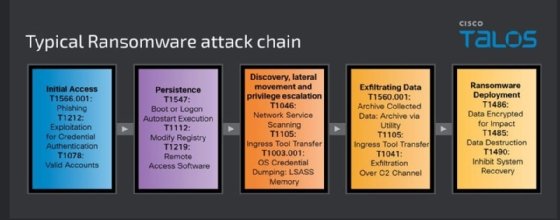
In a blog post on Wednesday, James Nutland, Cisco Talos threat intelligence analyst, detailed the tactics, techniques and procedures (TTP) of the 14 most prominent ransomware groups on the threat landscape between 2023 and 2024. Nutland found that LockBit was the most active group during that span, despite multiple recent law enforcement efforts. In addition, Cisco Talos research showed that vulnerability exploitation is the preferred tactic for ransomware actors to gain initial access to a victim environment.
Nutland outlined common ransomware attack chains and provided examples of exploited vulnerabilities, including one known as ZeroLogon that was disclosed and patched in 2020. Ransomware groups went back even further and exploited an old Fortinet FortiOS SSL VPN vulnerability, tracked as CVE-2018-13379, as well.
He emphasized that the timing of the blog coincides with significant attacks, including one against CDK Global last month.
"Talos' studies indicate that the most prolific ransomware actors prioritize gaining initial access to targeted networks, with valid accounts being the most common mechanism. Phishing for credentials often precedes these attacks, a trend observed across all incident response engagements, consistent with our 2023 Year in Review report," Nutland wrote in the blog. "Over the past year, many groups have increasingly exploited known and zero-day vulnerabilities in public-facing applications, making this a prevalent initial access vector."
Nutland stressed that during the research period for this blog, Talos' incident response team was "responding to a considerable number of ransomware attacks heavily targeting the United States." Affected sectors included manufacturing, which other vendors reported as the topmost targeted sector as well. Nutland said that the attacks resulted in "significant levels of financial losses" and operation disruptions for victim organizations.
To gain initial access to those targets, Cisco observed ransomware actors repeatedly exploited three vulnerabilities. The first is an elevation of privilege vulnerability in Microsoft's Netlogon Remote Protocol, tracked as CVE-2020-1472 and otherwise known as Zerologon. Nutland warned that exploitation could allow an attacker to bypass authentication requirements and change passwords through Windows Active Directory.
"Ransomware actors leverage this vulnerability to gain initial access to networks without requiring authentication, quickly escalating privileges to domain administrator levels. This access enables them to manipulate security policies, and potentially disable security defenses, facilitating unobstructed lateral movement and attack progression," Nutland wrote.
The second vulnerability Nutland highlighted was a path traversal flaw in Fortinet's FortiOS SSL VPN, tracked as CVE-2018-13379. He warned that ransomware groups exploit it to obtain sensitive information, including VPN session tokens, that can then be used to gain unauthorized network access.
Following exploitation, Cisco observed the actors move laterally through the victim's network and exploit more vulnerabilities or weak configurations prior to ransomware deployment and data exfiltration.
Lastly, ransomware actors repeatedly exploited a critical flaw in Fortra's GoAnywhere managed file transfer software, tracked as CVE-2023-0669. The Clop ransomware gang initially exploited it as a zero-day vulnerability in January of 2023, and significant fallout mounted as more victims came to light.
"This critical vulnerability enables actors to deploy ransomware payloads directly to servers or use the compromised server as a pivot for further internal reconnaissance and lateral movement. The ability to execute arbitrary code enables attackers to manipulate systems, create backdoors and disable security controls," the blog read.
Exploiting vulnerabilities in publicly facing applications to gain initial access has become a common practice for many threat actors, not just ransomware gangs. A recent joint government advisory warned that the Chinese-state sponsored threat group known as APT40 also prioritizes vulnerability exploitation as an initial access vector.
Data theft only attacks
While LockBit remains in the lead for having the most activity observed on a public data leak site, Nutland noted that the Alphv and Rhysdia ransomware gangs also stood out among the many ransomware gangs. Cisco Talos found that Alphv and Rhysdia, a newer group that emerged in 2023, portrayed the broadest range of TTPs.
"Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology," he wrote. "The diversification highlights a shift toward more boutique-targeted cybercriminal activities as groups such as Hunters International, Cactus and Akira carve out specific niches, focusing on distinct operational goals and stylistic choices to differentiate themselves."
On the other hand, Clop ransomware actors embraced data theft-only attacks as opposed to traditional ransomware with encryption. Nutland noted that Clop is one of the only groups to exploit zero-day vulnerabilities.
Nutland told TechTarget Editorial that while Clop has historically engaged in traditional double extortion attacks where threat actors encrypt and exfiltrate data, the group is known for frequently updating their malware toolset. He highlighted the recent attacks against Progress Software's MoveIt Transfer file product where Clop actors claimed thousands of victims by exploiting one zero-day vulnerability.
"Cl0P leveraged the MOVEit managed file transfer vulnerability to attack organizations on a significant scale, foregoing their previous double extortion tactics throughout the campaign and instead choosing to steal the data and hold it for ransom, without encryption. We have observed a decrease in Cl0p activity this year, but it's typical to see actors come and go in this dynamic threat space," Nutland said.
Nutland added that traditional ransomware attacks are still highly prevalent compared to data theft-only attacks. He said pure data theft only attacks, where no encryption occurs, are less common but still present. For a period last year, it appeared as though data theft-only attacks were going to increase as threat actors employed more brazen extortion tactics, he said, but now that doesn't appear to be true.
"We saw more of these types of attacks last year, but so far in 2024, it seems that double extortion operations are back on the rise, with lots of new ransomware variants being observed in the wild."
Defense evasion
In addition to the top TTPs for initial access, Cisco Talos also observed effective evasion techniques to increase dwell time in victim organizations networks. Cisco IR engagements revealed that ransomware actors disabled and modified antivirus programs, endpoint detection and response (EDR) tools and security features protecting the operating system. In addition, Nutland said attackers modified system registries to disable security alerts and block recovery options for users.
Separately, SentinelOne also observed ransomware actors increasingly adapting to EDR tools.
Nutland stressed the increasing need for organizations to employ appropriate security controls and regular patch management. Additional mitigations include MFA, network segmentation and implementing the principle of least privilege.
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.





