
Getty Images
Ransomware tied to attacks on critical infrastructure last year
While recent law enforcement action may be altering the ransomware landscape, BlackBerry researchers observed high-profile attacks on critical infrastructure last year.
Ransomware played a key role in attacks on critical infrastructure throughout 2021, according to a new report by BlackBerry.
The 2022 Threat report, released Tuesday, highlighted top ransomware players that contributed to a year filled with dangerous attacks that impacted critical industries. BlackBerry's report broke down the tactics and targets of particularly active groups and offered security recommendations for organizations.
While the report did attribute recent law enforcement action to the shutdown of some ransomware groups in the latter half of the year and the beginning of 2022, the damage to critical infrastructure had already been done.
REvil, which Russian authorities claim to have shut down last month, was behind the significant attack on JBS Foods USA in June. The subsidiary of the world's largest beef producers paid an $11 million ransom. Another hefty ransom was paid, with a portion seized by the FBI, after DarkSide attacked the Colonial Pipeline Co. in May, which impacted U.S. oil.
Critical infrastructure companies weren't the only large enterprises affected by massive ransomware attacks last year. Additionally, Hive hit big with software vendor Altus Group, where operators subsequently leaked data. BlackBerry researchers observed Conti attacks against manufacturing and healthcare service providers across Japan, Europe and the U.S. this year.
One commonality occurred mid-year, when REvil and Conti increasingly targeted banks.
Eric Milam, vice president of research and intelligence at BlackBerry, attributed it to two possible factors: easy money and perhaps a sense of morality.
"In my opinion, things like banks are easy targets. Money's usually insured and things like that. You hit a hospital and people die. There's a real backlash there," he said.
As far as why Conti and REvil targeted banks more frequently than other groups did during that time, Milam can't be exactly sure. One reason may come down to sophistication, he said, and another to access.
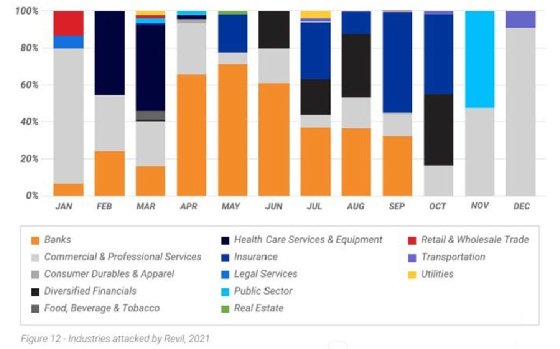
"Their access is being sold nonstop. I spent many years as [a red team] attacker, and in 15 minutes I had access to billions of dollars. It wasn't super difficult, so that might be it -- they had an abundance of access to it at that time," he said.
Varying tactics, same goal
The most notable takeaway from this year's report, Milam said, is how easy these attacks have become to continually execute. The bar of entry to leverage ransomware as a service (RaaS) and exploit toolkits for someone who isn't even knowledgeable is decreasing, he said, and it may only require $120.
"You don't have to set up your infrastructure; you don't have to hide. You don't have to do anything," he said. "You can just ride on the back of something else that's already built. It's like a one-stop shop."
Lately, Milam said the way ransomware groups operate mimics the corporate world. However, each one employed an array of tactics.
REvil utilized phishing campaigns, brute-force attacks and software vulnerabilities, according to the report, while DarkSide targeted machines running both Windows and Linux. Though many ransomware groups use double extortion techniques to pressure victims into paying, Avaddon also subjected victims to a "distributed denial of service attack until the ransom is paid."
The Conti variant, which is provided a "saleable service," was even more risky because it "can be altered from one infection to another."
"Many analysts regard Conti as the ransomware that replaced Ryuk and consider it to be one of the most troubling ransomware threats in the wild," the report said.
Another tactic widely employed in ransomware attacks is the use of stolen Cobalt Strike penetration testing tools. One issue Milam pointed out is that only pen testers can buy it, not researchers, which he said puts them at a disservice to better understand the software. It's been successful in attacks against enterprises, he said, because it's well done.
"A lot of the stuff executes in memory so when you look at it, if you don't have a really good map defense or multiple layers within memory detection, it's able to execute; and it's not just that, you execute Powershell from memory [too]," he said. "I think we as defenders need to continue to make that more robust."
Additionally, Milam said the RaaS business model is making it harder and harder to attribute attacks. Now, he said, nation-states may be continually outsourcing different things, with an increase in contracting independent ransomware operators.
"The mission of most threat actors today is to exfiltrate data and launch ransomware for profit," the report said.
Protecting critical infrastructure
The report cited several factors that make protecting critical infrastructure, like gas, power and water, increasingly more difficult. For one, they are high-value targets. They are also "older and inherently vulnerable," with legacy operating systems that may not have been designed to receive security updates through the internet.
"Since these environments can be difficult and expensive to modernize, they typically run older and usually unsupported operating systems," the report said.
Critical infrastructure organizations not only have to protect against old threats, but upcoming ones as well. According to the report, "an entire field known as adversarial learning has emerged as a threat to all products employing predictive algorithms."
While Milam said BlackBerry has not observed attacks in the wild yet, there probably are attacks that they haven't heard about yet.
When it comes to security, "anything less than around-the-clock monitoring is not sufficient," according to the report, but "prevention is key."
"The ability to recover from backups does not address the double extortion tactic derived from attackers threatening to sell stolen data," the report said.
While it is a challenging environment to secure, the situation is not hopeless, according to the report.
One positive highlighted is recent law enforcement action, which BlackBerry said has had some effect on the ransomware landscape.
"Law enforcement efforts to track down malware operators visibly increased after the attack on Colonial Pipeline, which likewise prompted DarkSide to shut down operations," the report said.






