
Getty Images
Cryptocurrency theft leaves Beanstalk Farms' future in doubt
Beanstalk Farms' founders confirmed they found many aspects of activity during the attack 'strange' but saw no reason for concern. Now, the company's future is uncertain.
Beanstalk Farms is struggling to recover from an attack that not only highlighted simple flaws in its system but also drained all protocol assets.
On Sunday, blockchain analytics company PeckShield alerted the decentralized finance (DeFi) platform to an Etherscan showing suspicious transaction activity. Beanstalk then confirmed the attack on Twitter Sunday and stated an investigation into the nearly $80 million loss of "non-beanstalk user assets" was ongoing. Through a series of social media posts, public statements and conference calls this week, Beanstalk's founders have revealed just how damaging the attack was.
It forced the formerly anonymous owners to reveal their identities, to offer an ethical hacker bounty to the attacker and to pause the entire DeFi system without a restart date in sight. The revelations about the attack also raised questions about the design of BeanStalk's platform, its security posture and who is in charge of the company.
During a sprawling, three-plus hour "Beanstalk Exploit Town Hall" on Discord Sunday evening, the founders, who previously operated under the alias "Publius," revealed their identities as Benjamin Weintraub, Brendan Sanderson and Michael Montoya. The trio attended the University of Chicago together prior to founding the Ethereum-based DeFi protocol.
To kick off the town hall meeting on Sunday, Weintraub said the founders revealed their identities to dispense any notion that they were involved in the attack. He reiterated that sentiment many times, in addition to stating their commitment for Beanstalk to "not have a head in any capacity" and essentially run on its own.
"It's important to acknowledge that we aren't in charge and have never positioned ourselves as in charge of Beanstalk," Weintraub said.
Regardless of Beanstalk's management structure, the platform remains down with no immediate plan to resume. Weintraub chalked that up to an "economics problem" given that there is no money in the liquidity pools. Just days earlier, the company boasted on Twitter that it had $130 million in liquidity and a $95 million market cap.

While Weintraub said the founders contacted the FBI's Internet Crime Center following the attack, they have not heard back.
Flash loan failure
Beanstalk, along with blockchain security vendors Omniscia and CertiK, provided insight into how the attacker made off with all the beans. While a vulnerability made the attack possible, there were flaws in the stablecoin protocol that led to its success.
In a blog post Tuesday, Beanstalk said "the perpetrator used a flash loan to exploit the protocol's governance mechanism and send the funds to a wallet they controlled."
Flash loans are transactions that allow DeFi members to borrow and return funds in an instant without any collateral. "The term 'flash loan' refers to a loan, usually of significant proportion, that is repaid in the same execution flow it is acquired," Omniscia CEO Yvan Nasr told SearchSecurity in an email. "As a result, the loan in traditional terms is opened and closed at the same second, hence the term 'flash.' This is possible because multiple actions in an Ethereum based blockchain can be bundled into the same transaction."
Monier Jalal, vice president of marketing at CertiK, said flash loans are a new invention in the DeFi market that were first introduced in January of 2020 and "can be used for both honest and malicious reasons."
While unsecured loans with no collateral may sound like a recipe for disaster, flash loans on DeFi platforms are designed to ensure the loan is repaid in the same transaction as the initial borrow. In practice, a flash loan will be canceled if it is not repaid instantaneously.
"However, due to the lack of anti-flash loan mechanisms in the Beanstalk protocol, the attackers could borrow numerous tokens that are supported by the protocol and vote for malicious proposals," Jalal said in an email to SearchSecurity.
In other words, the attacker used the flash loan to abuse the Beanstalk protocol's governance system, which is a feature of many DeFi platforms that allows users to submit and vote on proposed policies and changes to the protocol. In the Beanstalk attack, the attacker accrued a substantial amount of voting power through the flash loan and altered the platform in a way that enabled them drain approximately $180 million from the platform.
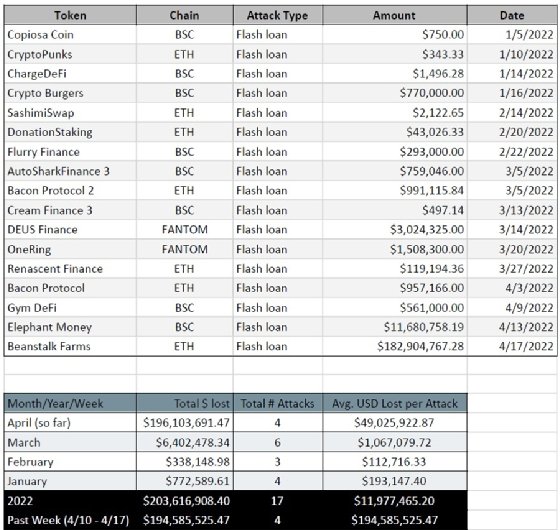
Beanstalk isn't alone in falling victim to flash loan attacks; according to data from CertiK, there have been 17 such attacks on DeFi platforms so far this year, though Beanstalk's loss is by far the largest amount.
Nasr said a vulnerability permitted the attacker to execute malicious code on Beanstalk, though it appears it was avoidable.
"Foremost, these attacks should be nullified at the design level and should not be possible at all in well designed systems," he said in an email to SearchSecurity.
While Omnisicia had previously audited Beanstalk's system, the company emphasized in a post-mortem report that the code exploited in the attack was "was introduced beyond our initial audits of the system." Nasr explained how the attacker was able to do so much damage within the confines of Beanstalk's own governance system.
"A unique trait to highlight here is that the Beanstalk system uses what is known as the Diamond pattern, an upgradeability system that is completely modular and allows new proposals to execute new code as well as make it available in the system as if the project itself is carrying out the actions," he said. "This design trait permitted the attacker to execute transactions on behalf of the Beanstalk system and was ultimately used to siphon all assets held by it."
During the town hall meeting Sunday, Weintraub addressed prevention of such abuse and whether there needs to be a flash loan resistance built into the governance. His answer echoed Nasr's statement regarding a design flaw.
"It's brutal because it's not technically hard to fix, it just wasn't part of the protocol," he said.
A criminal hack or a legitimate transaction?
During the Sunday town hall, an important question came up: Were the attacker's actions illegal, or did the attacker simply use the governance structure to their benefit? After a long pause, Weintraub said there was "no doubt this is a crime" and that "a lot of money was stolen from a lot of people."
Despite actions taken to pause the platform and burn remaining beans from the attacker's contract, approximately $80 million was drained from the protocol's liquidity pool. According to PeckShield, the attacker moved much of the funds to Tornado Cash, a cryptocurrency mixer used by threat actors to hide illicit funds.
The Beanstalk owners expanded on the attack steps during the Sunday town hall meeting, including some of the red flags that were missed. According to Weintraub, an unknown Ethereum address deposited a massive amount of funds into a silo, which enabled the owner to acquire enough voting power to propose two Beanstalk-Improvement-Proposals (BIPs).
"They proposed BIPs 18 and 19 on chain yesterday and there was a lot of uncertainty as to what BIPs 18 and 19 were. It was the first time there was a BIP that Beanstalk was unaware of at the time they proposed," Weintraub said during the meeting. "It was a definitely a weird circumstance."
In one of the more unusual moves, the attacker donated 250,000 Beanstalk tokens, known as "Beans," to Ukraine during the attack. Though the hacker took additional steps between the suspicious donations and draining the liquidity pools, Weintraub said that the activity didn't raise any flags.
"It seemed a little bit weird it was trying to donate beans to the Ukraine and frankly we didn't think much of it. We designed the governance structure to be secure against any arbitrary attack and we thought it was secure. And it was not secure," he said during the town hall meeting.
Additionally, Weintraub confirmed they were notified about the flash loan attack and examined it but did not "think there was anything to be scared of."
While the massive transaction may have appeared to be legitimate, Jalal said the attacker did exploit a vulnerability in the Beanstalk governance system that allowed the attacker to execute malicious code on the platform and obtain funds that should not have been accessible.
Resuming operations
In the immediate aftermath of the attack on Sunday, Beanstalk founders painted a grim picture for the company. In the Beanstalk Discord, the founders' "Publius" account admitted the attacker was able to "drain Beanstalk entirely" and that it was highly unlikely any bailout would occur since the platform was started without venture capital funding.
"We are f---ed," Publius wrote.
The founders offered a more optimistic view in later statements on social media and town hall meetings, but they acknowledge there are an array of obstacles preventing the return of Beanstalk, most importantly a lack of Beans.
One problem Weintraub highlighted during the Sunday town hall meeting was the amount of Beanstalk assets that were liquid in the liquidity pools as a percentage of the total assets. One solution he suggested was essentially a fundraiser backed by users.
However, the goal, he said, is to evaluate collectively and come up with a set of three or four different viable options to resume operations.
"We don't want to pursue launching anything from scratch until we pursue if there's anything else we can do," Weintraub said. "We're not in charge, so it's hard to say 'Oh, this is what's going to happen'."
On Monday, the company made a direct appeal to the attacker on Twitter and took the unusual step of allowing them to keep 10% of stolen funds as part of a "white hat bounty."
If you will return 90% of the withdrawn funds to the Beanstalk Farms multi-sig wallet 0x21DE18B6A8f78eDe6D16C50A167f6B222DC08DF7, Beanstalk will treat the remaining 10% as a Whitehat bounty properly payable to you.
— Beanstalk Farms (@BeanstalkFarms) April 18, 2022
Questions arose on what the resurgence of Beanstalk may look like. How will it be governed? What will be done to minimize the potential of exploits? Will it use systems that are already simulated and audited? The answers, however, were more than unclear.
"Great point. Those are questions everyone will be considering once we evaluate," Weintraub said.
Weintraub also addressed the chances of fund recovery, and it was dim. While he did say a blockchain analysis firm is "trying to look into it," he appeared to rely heavily on Beanstalk's tweet for help from the community.
"But it's prudent to precede as if funds are not recoverable," Weintraub said during the Sunday meeting.
In a separate town hall meeting Tuesday, one user voiced concerns of what happens to those users who purchased Beans after the hack. It appears new users were not sufficiently warned of Sunday's attack. Weintraub said it is very tricky and they are still deciding which way to move forward.
Moving forward may be tricky in general.
When asked if they'd change the model in the way things are sold, Weintraub held strong in supporting the fundamentals of the Beanstalk structure.
"This structure generally has been the main driver of Beanstalk's success thus far, so we aren't inclined to run away from it, but play into very much so."
On Wednesday, Beanstalk announced an event called "Barn Raise," a public 10-day fundraiser aimed at restoring the platform's liquidity. The company also announced several security measures, including plans to launch a formal bug bounty program as well as an end-to-end audit in June by infosec consultancy TrailofBits.
SearchSecurity contacted Beanstalk Farms for comment. "The Beanstalk Team is currently in the process of gathering community's feedback on the said plan, and the Beanstalk DAO will vote on a final version in the next day or two," a company spokesperson said, declining further comment.







