
Getty Images
Cryptomining campaign abused free GitHub account trials
Cloud security vendor Sysdig uncovered the largest cryptomining operation it's ever seen as threat actors used free account trials to shift the costs to service providers.
Threat actors are abusing free account trials offered by cloud service providers in a sophisticated cryptomining campaign with a massive scale, according to new research.
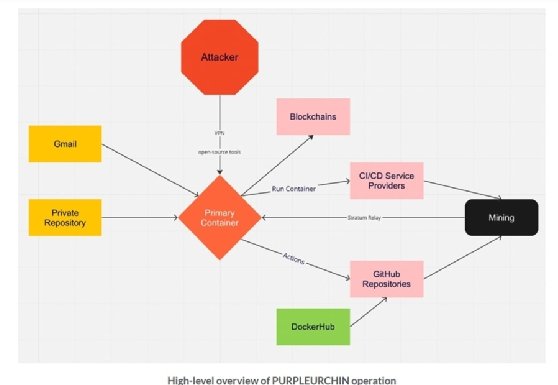
The Sysdig Threat Research Team discovered the massive operation, which it has named Purpleurchin, while analyzing publicly shared containers and suspicious activity stemming from a Docker Hub account. Further analysis revealed an integration of open source tools and a connection to GitHub Actions, a continuous integration/continuous delivery (CI/CD) platform, to run mining operations.
While cryptomining attacks have increased rapidly over the past few years as the value of various digital currencies has risen, the immense scale of this particular operation came to light when Sysdig researchers uncovered that threat actors were targeting several platforms at once.
That included more than 30 GitHub accounts, 2,000 Heroku accounts and 900 Buddy accounts, as well as 130 Docker Hub images. Even more noteworthy was the high level of automation and amount of effort required, which Sysdig called "abnormal."
In a blog post Tuesday, Crystal Morin, Sysdig threat research engineer, detailed how Purpleurchin used a technique called freejacking, which abuses computing resources allocated for free trial accounts on CI/CD platforms.
While threat actors have abused free accounts in the past, and open source software such as Docker has been a target for cryptomining, Sysdig had not seen the technique deployed at this scale.
"PURPLEURCHIN is one such actor who is actively evolving their freejacking operation in order to abuse a large number of free accounts with as little human effort as possible," Morin wrote in the blog.
Morin told TechTarget Editorial that Sysdig does not know how long this has been happening or whether other actors are taking advantage of the technique. It's the first time the cloud security vendor has observed this kind of activity, she added.
Automated abuse
The primary factor in Purpleurchin's success so far, according to Morin, is automation, which has enabled threat actors to continuously create these free accounts to keep the mining operation moving forward.
"There was a lot behind what they did to automate and build this operation," Morin said. "It wasn't just clicking buttons. I think there was a lot of effort put into the back end of this to be able to reap the benefits of the automation once it all started working correctly, and at large scale."
One reason she gave for the cryptomining operation's substantial growth while staying under the radar is that it's not affecting anyone directly or compromising user accounts. Rather, she said, threat actors are simply taking advantage of free opportunities. The blog noted that GitHub offers 2,000 free Action minutes per month.
However, Michael Clark, director of threat research at Sysdig, said that while most legitimate users wouldn't be affected by this threat activity directly, they could be affected in the long run.
"It's going to come back around when [CI/CD service providers] start charging, taking away their free tiers or charging more for their services," Clark said.
Sysdig broke down the potential costs to CI/CD service providers in the blog post, which estimated that every free GitHub account costs the cloud service $15 per month. Free trials at the other companies such as Heroku and Buddy can cost providers between $7 and $10 per month.
"At these rates, it would cost a provider more than $100,000 for a threat actor to mine one Monero," Morin wrote in the blog.
Evasion efforts
Though Monero is a popular cryptocurrency among cybercriminals and particularly ransomware groups, Morin noted in the blog that Purpleurchin mines for other digital currencies, including Tidecoin, Onyx and Bitweb. Sysdig said this move might be calculated because law enforcement agencies watch Monero more closely.
The threat actors behind Purpleurchin also opted for a different mining algorithm than the one most cybercriminals use, which could be a factor for why its activity hadn't been reported until now.
"This is notable because cryptojackers will usually just use XMRig downloaded straight from GitHub, the de facto CPU miner for Monero, whereas Purpleurchin is opting for a CPU miner that gets called via nodejs," Morin wrote. "Our theory here is that the threat actor is choosing these coins based on the yespower algorithm because the mining process can be spawned from said nodejs parent, aiding in evading detection."
Clark said the threat actors have made additional efforts to go undetected by using proxy servers for their cryptomining, moving those servers around and randomizing a lot of names. To make it difficult to connect the free trial accounts to one another, threat actors used OpenVPN software along with the Namecheap VPN network.
For Clark, one major takeaway from the cryptomining campaign was how it highlights the dual use of containers, which benefit legitimate users as well as threat actors. In the case of Purpleurchin, threat actors were using containers for command-and-control infrastructure. "They're really using it as much as everybody else," he said.
Sysdig noted a variety of possible motives behind the operation other than shifting the costs of running cryptominers to the service providers. For example, the threat actors might be preparing to attack the underlying blockchains of certain cryptocurrencies, which have been increasingly targeted recently. In August, threats to cryptocurrency exchanges and decentralized finance platforms became so dire that it warranted a government alert.
Lastly, Morin said the Purpleurchin campaign could be a decoy for other malicious activity, noting that a threat group known as APT32 used cryptomining attacks in conjunction with a cyberespionage campaign in 2020.
While companies including GitHub and Namecheap have tried to curb such abuse with measures such as requiring CAPTCHA when creating an account, she said, threat actors have found tools to get around those obstacles.
Clark added that platforms such as GitHub are in a tough spot because they want to make it frictionless for people to use the site and sign up, and free trials are a big part of that.
"They have to find a balance between too hard and too easy, but it also benefits the attacker because as long as it's not too hard, they'll be able to pull this off," Clark said.
TechTarget Editorial contacted GitHub for comment, but the company had not responded at press time.







