- Share this item with your network:
- Download
Information Security
- Editor's letterFresh thinking on cybersecurity threats for 2020
- Cover storyThreat intelligence offers promise, but limitations remain
- InfographicData breach costs hit hard; where are you most vulnerable?
- FeatureCISOs face a range of cybersecurity challenges in 2020
- ColumnCisco CISO says today's enterprise must take chances
- Column2 components of detection and threat intelligence platforms

Vlad Chorniy/stock.adobe.com
Fresh thinking on cybersecurity threats for 2020
It's a good time to take a clear-eyed view of the likely security threats facing your organization. But then what? Experts suggest getting creative with your threat responses.
Metaphors may be cheesy, but often they make total sense, especially when it comes to cybersecurity. For example, when eye doctors say someone has 20/20 vision, the person's vision isn't perfect, but it's enough to see an object from a distance of 20 feet. A cybersecurity program doesn't need to be perfect either. It needs to be sufficient enough to protect an organization's unique data and assets from cybersecurity threats.
Not that cyberthreats are anything to be glib about. A 2019 research study by the Ponemon Institute, sponsored by IBM Security, estimated the average cost of a security incident at $3.92 million globally, and more than double that -- $8.19 million -- in the United States. (See "Data breach costs hit hard; where are you most vulnerable?" in this issue, for more.) But the same study also found incident costs can be significantly reduced through quick identification and containment. Visibility is everything -- to drag the eye doctor metaphor out even more.
It's wise to keep an eye (sorry) on new vendor offerings, and it's tempting to look to the latest tech for the answer to cybersecurity threats. But a lack of tools is not the problem. Organizations already have threat intelligence services and network monitoring products, web vulnerability scanners, packet sniffers and antivirus software. Automation, AI and machine learning features are quickly making these tools smarter and faster. As security expert Kevin Beaver so succinctly puts it, "We don't need more of anything."
Keeping the C-suite focused on cybersecurity is essential, of course. Executives may finally be paying attention, because funding for cybersecurity is growing. RSA reported, for instance, that from 2018 to 2019, approximately 75% of organizations increased their cybersecurity investments. Gartner estimated that global spending on security products and services will grow to $133.7 billion in the next two years.
So how do we make security defenses sufficient in the 2020s? Many experts now advise more creative use of what security teams already have at their disposal to determine which cybersecurity threats are the most likely and how to best use staff, products and services to root those threats out. But while imagination and fresh thinking can be powerful, don't overlook common sense.
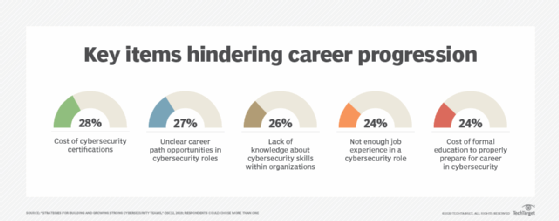
First, keep your current skills sharp and reinforce new knowledge. (To that end, try the quiz based on the information in this issue.) The 2019 workforce study by (ISC)2 shows the top two obstacles to building a strong team is the cost of certifications -- often borne by the individual -- and unclear career paths. In other words, while there are ways to get creative about plugging gaps in staff and uncovering talent, sometimes simple fixes like companies footing the bill for employees willing to earn certifications and holding regular information sessions on cybersecurity career opportunities can go a long way too.
Related Resources
- Kaspersky Container Security –Kaspersky
- 7 cybersecurity trends for 2026 –SHI International
- Reimagining Security for the AI Era –Cisco
- Risk-Based IT Compliance: The Case for Business-Driven Cyber Risk Quantification –Talk
Dig Deeper on Threats and vulnerabilities
-
![]()
Patch ToolShell SharePoint zero-day immediately, says Microsoft
By: Alex Scroxton
-
![]()
Microsoft SharePoint attacks target on-premises servers
By: Shane Snider
-
![]()
What is the Cybersecurity Information Sharing Act (CISA)?
By: Katie Terrell Hanna
-
![]()
2024: Putting Cyber Resilience into Social, Political, Business and Budget context.
By: Philip Virgo




















