
Steve Young - Fotolia
Information security certification guide: Specialized certifications
This information security certification guide looks at vendor-neutral certifications in specialized areas such as risk management, security auditing and secure programming.
Information security professionals are often expected to be experts in a broad range of areas. After all, the International Information Systems Security Certification Consortium defines eight different domains in its Common Body of Knowledge, the subjects relevant to information security work. However, there are always specialties, like information security auditing, fraud investigation, risk management and even secure programming.
This report comprehensively reviews the current state of specialized information security certifications, highlighting which are best for achieving goals specific to specialist information security career paths.
This report is the last in a series on information security certifications. This series is a companion to three other articles that cover the vendor-specific information security certification landscape, vendor-neutral certification career paths and cloud security certifications in detail.
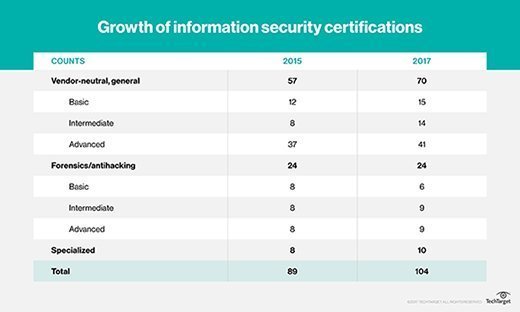
Several changes have been made for this updated survey of information security certifications. The following table shows the number of certifications in the 2015 edition, as well as this 2018 edition. The overall numbers for vendor-neutral information security certifications have increased by about 14%. Several certifications have been discontinued, and 19 credentials have been added. Some certifications have been moved to new categories to more accurately categorize them.
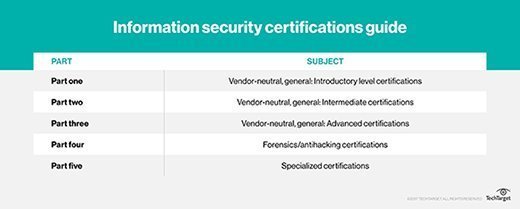
Part one of the information security certification guide series covers certifications suitable for newcomers to the industry, part two covers intermediate certifications and part three includes advanced information security certifications. Part four covers information security certifications relevant to forensics practitioners.
Editor's note: The credentials are listed in alphabetical order.
The Institute of Internal Auditors Certification in Control Self-Assessment
The Certification in Control Self-Assessment (CCSA) recognizes individuals with knowledge of internal control self-assessment procedures, and it is primarily focused on financial and records controls. This information security certification is of primary interest to those professionals who must evaluate IT infrastructures for possible threats to financial integrity, legal requirements for confidentiality and regulatory requirements for privacy.
Candidates are expected to have a four-year college degree, a two-year college degree with five years of verified experience or seven years of internal auditing experience. In addition to passing an examination, candidates must also have at least one year of verified work experience in control areas, such as control self-assessment, auditing, quality assurance, risk management or environmental auditing.
In addition, CCSA candidates must obtain seven hours of acceptable facilitation experience or at least 14 hours of acceptable facilitation training and must submit a character reference.
Source: The Institute of Internal Auditors Certification in Control Self-Assessment
Association of Certified Fraud Examiners Certified Fraud Examiner
The Certified Fraud Examiner (CFE) certification recognizes individuals who demonstrate the skills necessary to detect financial fraud and other white-collar crimes. This certification is of primary interest to full-time security professionals in law, law enforcement or those who work in organizations with legal mandates to audit for possible fraudulent or illegal transactions and activities, such as banking, securities trading or classified operations.
CFE candidates must obtain membership in the Association of Certified Fraud Examiners in addition to passing a single exam. Candidates must also have a bachelor's degree or equivalent and at least two years of applicable professional experience.
Source: Association of Certified Fraud Examiners Certified Fraud Examiner
The Institute of Internal Auditors Certified Financial Services Auditor
The Certified Financial Services Auditor (CFSA) certification recognizes professional auditors with a thorough knowledge of auditing principles and practices in the banking, insurance and securities financial services industries.
Candidates for the CFSA certification must pass an examination and have one of a four-year college degree, a two-year college degree with five years of verified experience or seven years of internal auditing experience. In addition, candidates must show proof of at least two years of appropriate auditing experience -- must be in a financial services environment -- and submit a character reference.
Source: The Institute of Internal Auditors Certified Financial Services Auditor
The Institute of Internal Auditors Certified Government Auditing Professional
The Certified Government Auditing Professional (CGAP) certification recognizes public sector internal auditors who focus on fund accounting, grants, legislative oversight and confidentiality rights, among other facets of internal auditing.
Candidates for the CGAP must pass an examination and have one of an appropriate four-year college degree, a two-year college degree with five years of verified experience or seven years of internal auditing experience. In addition, candidates must show proof of at least two years of direct government auditing experience and submit a character reference.
Source: The Institute of Internal Auditors Certified Government Auditing Professional
The Institute of Internal Auditors Certified Internal Auditor
The Certified Internal Auditor (CIA) certificate is granted to professionals who demonstrate knowledge of professional financial auditing practices. This credential is of primary interest to financial professionals responsible for auditing IT practices and procedures, as well as standard accounting practices and procedures, to ensure the integrity and correctness of financial records, transaction logs and other records relevant to commercial activities.
Candidates must have a bachelor's degree, a two-year degree with five years of internal auditing experience or seven years of internal auditing experience -- approval required. In addition, candidates for the CIA certification must show proof of at least two years of direct government auditing experience -- candidates with a master's degree are only required to submit proof of one year of work experience -- and must submit a character reference. To obtain this certification, candidates must pass a three-part exam.
Source: The Institute of Internal Auditors Certified Internal Auditor
ISACA Certified Information Systems Auditor
The Certified Information Systems Auditor (CISA) credential certifies that the holder has demonstrated audit experience, skills and knowledge of information systems auditing for control and security purposes. This certificate is of primary interest to IT security professionals responsible for auditing IT systems, practices and procedures to make sure organizational security policies meet governmental and regulatory requirements, conform to best security practices and principles, and meet or exceed requirements stated in an organization's security policy.
To obtain the CISA certification, candidates must pass one exam and submit an application for certification that demonstrates a minimum of five years of relevant experience. Certificants must also adhere to the ISACA Code of Professional Ethics.
Source: ISACA Certified Information Systems Auditor
Mile2 Certified Information Systems Risk Manager
The Certified Information Systems Risk Manager (CISRM) certificate from Mile2 recognizes risk managers, information system security officers and system managers working in private industries, as well as local, state and U.S. government agencies.
Candidates for the CISRM certification are expected to demonstrate their knowledge of risk identification, assessment and response; how to monitor risk; and security control design and implementation. Candidates must pass an examination and have at least one year of experience working with information systems.
The course is National Security Agency Committee of National Security Systems 4011-4016 accredited and is on the FBI Cyber Security Certification Requirement approved list.
Source: Mile2 Certified Information Systems Risk Manager
ISACA Certified in Risk and Information Systems Control
The Certified in Risk and Information Systems Control (CRISC) credential recognizes IT professionals who have hands-on experience with risk identification, assessment evaluation, response and information systems control design, implementation, monitoring, and maintenance.
Candidates must have at least three years of related work experience in at least two of the four CRISC domains, with at least one year of experience focused on domain 1 or 2. Candidates must also pass one exam.
Source: ISACA Certified in Risk and Information Systems Control
EC-Council Certified Secure Programmer
The EC-Council Certified Secure Programmer (ECSP) certificate is designed to recognize programmers who can design and build relatively bug-free, stable Windows- and web-based applications with either the .NET or Java Framework, greatly reducing exploitation by hackers and the incorporation of malicious code.
Candidates for the ECSP certification must pass a single exam.
Source: EC-Council Certified Secure Programmer
Project Management Institute Risk Management Professional
The Project Management Institute Risk Management Professional (PMI-RMP) certification recognizes professionals who assess, manage and report on risk in complex projects.
Candidates must either have a high school diploma; associate's degree or equivalent, at least 4,500 hours of project risk experience and 40 hours of project risk management education; or a four-year degree or equivalent, 3,000 hours of project risk management work experience and 30 hours of project risk management education. Candidates for the PMI-RMP certification must also pass one exam and earn 30 professional development units every three years to maintain the credential.
Source: Project Management Institute Risk Management Professional







