Comparing top identity and access management certifications
Holding an identity and access management certification demonstrates knowledge of security fundamentals, plus it can yield rewarding career and networking opportunities.
A rigorous identity and access management program diminishes the likelihood of a successful cyberattack. IAM also enhances an organization's ability to demonstrate compliance with cybersecurity standards and regulations. It's an essential security function for organizations of all types and sizes.
Despite its importance, IAM is not on equal footing with other cybersecurity disciplines when it comes to certifications. In fact, the security industry does not have a vendor-neutral certification specifically for identity. And, while the number and quality of industry trainings are improving, it's not always clear to IT workers how to embark on an IAM career.
To pursue identity-related certifications, it is useful to know which ones might be most relevant and how to pursue one or more of them.
Benefits and limitations of the top IAM certifications
Certifications demonstrate various levels of competency and experience, achieved through completing standardized examinations. Taking an exam -- or retaking the exam to renew certification or improve scores -- can quickly become expensive, so candidates should consider whether the upfront cost will be worth the investment.
Individuals who complete certification programs could enjoy benefits such as better employment opportunities, job retention and professional credibility. Certifications might also help workers achieve personal goals or corporate requirements. However, they should never assume that obtaining an IAM certification will automatically yield better prospects or land them an interview for an IAM job.
Knowledge of IAM fundamentals is an important reason for getting certified. Core IAM skills can be sharpened and demonstrated in the process of becoming certified -- even if the curriculum is focused on broader cybersecurity issues such as zero trust and is not limited to IAM.
Studying popular standards, such as Security Assertion Markup Language, OpenID Connect (OIDC) and Open Authorization (OAuth), is a practical way to better understand IAM intricacies and prepare for future tech environments. Access to such information is important when choosing a specific certification.
Networking opportunities might also present themselves as a result of certification. Many IAM certifications are completed through nonprofit organizations, such as ISC2. Because membership is often a prerequisite, candidates can take advantage of peer resources. Memberships come with additional costs, however, which may deter some individuals from the certification process. But cultivating relationships can help establish professional mentorships and distribute further expertise among certified members.
Ultimately, IAM professionals' decision on whether to get certified -- and which of the available IAM certifications to pursue -- will depend on their career path, their job responsibilities and the specific vendor tools they use in their work.
Important IAM certifications
The following section lists certifications that either directly or indirectly align with IAM issues and requirements. Candidates should aim for certifications that are well-known and acknowledged by industry professionals. They must determine if they can qualify for the certification and pass exams that might be needed. Certification organizations, vendors and other third parties offer training (e.g., training manuals, seminars, boot camps) in preparation for taking a specific certification exam and might be worth considering, despite the potential cost.
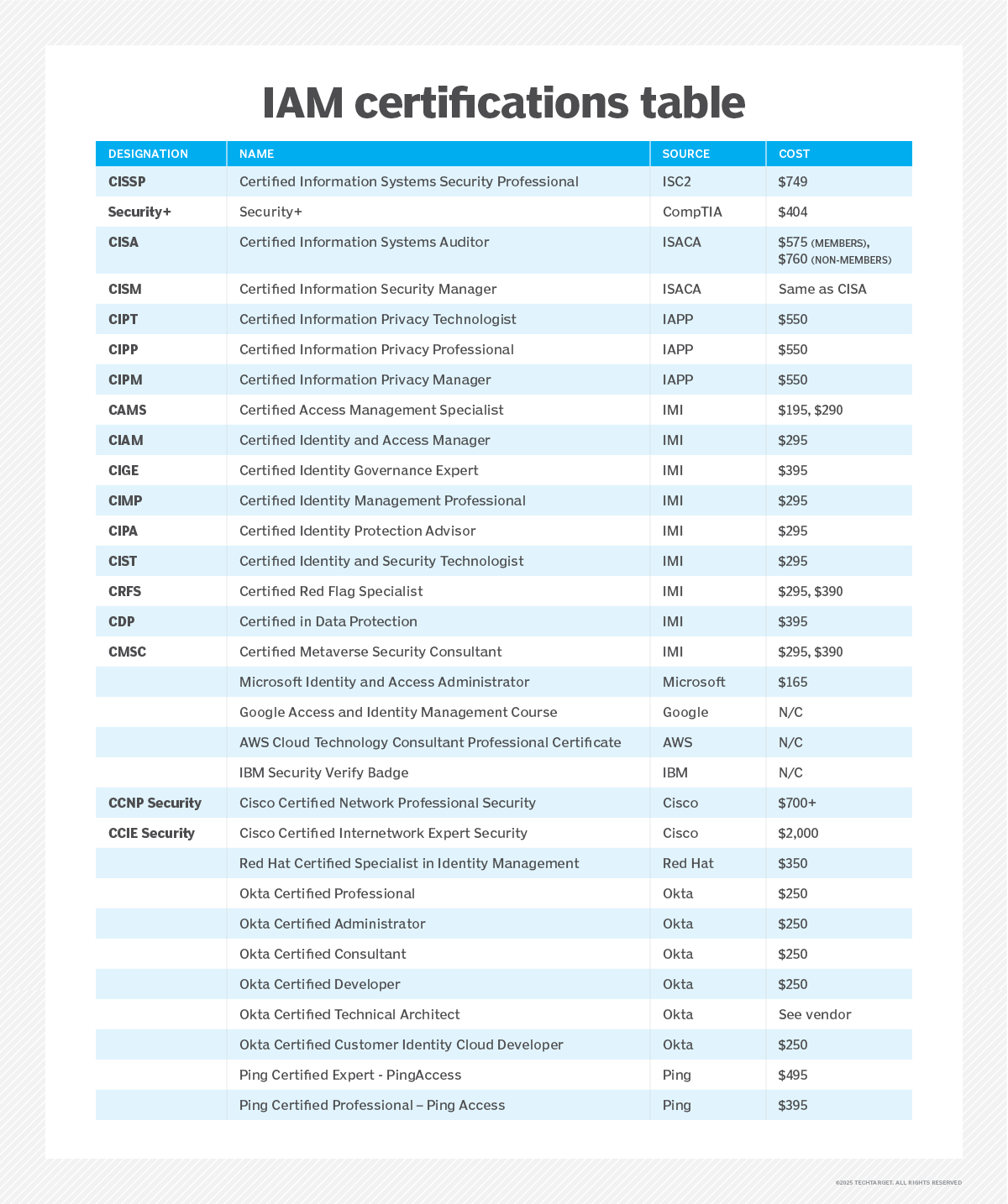
Certified Information Systems Security Professional (CISSP)
Offered by ISC2, CISSP is often considered one of the most valuable certifications for individuals who wish to demonstrate their competency on a wide array of cybersecurity principles and practices -- especially those focusing on IAM.
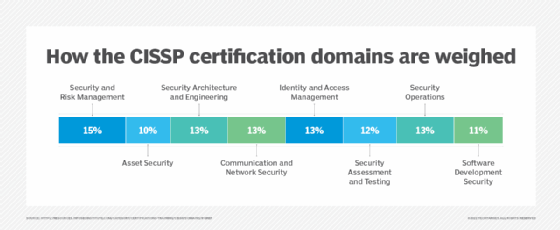
CISSP candidates must prove their comprehension of IAM skills, as well as how to successfully design, implement and manage a cybersecurity program. The CISSP Common Body of Knowledge encompasses 10 core subject domains, one of which -- Domain 5 -- covers IAM.
The CISSP is vendor-neutral, requires at least five years of relevant work experience and is awarded after achieving a passing score of 700 on the exam, which costs $749.
CompTIA Security+
CompTIA's Security+ certification demonstrates a person's competency with core knowledge required of any infosec role, including IAM. Security practitioners commonly pursue this certification prior to CISSP. The CompTIA Security+ credential counts as one year toward the five years' experience prerequisite of CISSP.
Candidates will gain hands-on troubleshooting experience and security problem-solving skills, as well as knowledge of IAM. The exam costs $404 and must be renewed every three years.
Certified Information Systems Auditor (CISA)
The Information Systems Audit and Control Association (ISACA) CISA certification demonstrates an individual's comprehension of infosec and IT auditing expertise, but it is not limited to auditing practitioners. The exam includes five job practice domains, including "Governance and Management of Information Technology" and "Protection of Information Assets."
Candidates for the CISA certification study how to perform an audit, in addition to ethics, standards and complex vocabulary. They must also have a minimum of five years of relevant work experience. Understanding how to audit and secure information systems -- skills necessary to pass the CISA exam -- can also supplement other infosec careers, such as an identity professional, cybersecurity risk analyst or risk advisory manager. The exam costs $575 for ISACA members or $760 for nonmembers. It must be renewed every three years. Membership in ISACA is also recommended.
Certified Information Systems Manager (CISM)
ISACA also offers the CISM certification for professionals seeking a role in cybersecurity leadership. Considered an advanced credential, it requires significant exam preparation. The certification demonstrates an individual's proficiency in cybersecurity practices and is highly regarded in the profession.
Four areas of cybersecurity competence are tested: incident management, infosec program development and management, risk management, and governance. Candidates must also agree to the ISACA Code of Professional Ethics and commit to continuing professional education. An extensive array of CISM training programs and documents is available. The exam costs $575 for ISACA members or $760 for nonmembers. It must be renewed every three years.
Certified Information Privacy Technologist (CIPT)
Considering the growing importance of data privacy and data protection fundamentals, the CIPT certification, as administered by the International Association of Privacy Professionals (IAPP), recognizes an individual's knowledge of privacy-related issues and practices as applicable within IT security.
The CIPT body of knowledge covers identity and access management and authentication. CIPT certification can enable individuals in private and public sectors to demonstrate the practical and technical knowledge required to apply privacy and data protection measures in the development, deployment or auditing of products and services.
Additional certifications from the IAPP that IAM professionals might wish to consider include the Certified Information Privacy Professional (CIPP) and Certified Information Privacy Manager (CIPM). The former demonstrates proficiency and knowledge of data protection laws, regulations and standards; the latter demonstrates competence in managing the day-to-day functions associated with information privacy and data protection operations. Each exam for the above certifications costs $550 and must be renewed every two years. Membership in the IAPP is also recommended.
Identity Management Institute (IMI) certifications
IMI has established an independent accreditation process by setting standards of excellence for identity management professionals through various certification programs. To obtain an IMI certification, candidates must join the organization and pass the corresponding exam, which can cost between $195 and $395. Two certifications -- CIST and CIGE -- offer an exam waiver. Fees include a study guide along with the exam, except for the two certifications noted above. IMI certifications include the following:
- Certified Access Management Specialist. CAMS-certified professionals gain IAM skills necessary to ensure compliance and risk management requirements regarding system and data access are met. Typical CAMS duties include designing and administering access management policies and procedures, granting access and conducting access reviews.
- Certified Identity and Access Manager. CIAM-certified professionals are IAM experts who work for a variety of organizations and demonstrate their ability to design, implement, improve and manage IAM programs, processes and tools. Typical CIAM duties include developing and administering programs that address identity and access risks to enterprise systems, deploying IAM tools and ensuring compliance.
- Certified Identity Governance Expert. CIGE-certified individuals demonstrate their ability to guide and support their organization's management in addressing identity data issues, including privacy, security, regulatory and contractual compliance, customer expectations and authentication. People with the CIGE are considered thought leaders who can analyze industry standards and frameworks as well as develop new identity policies and procedures.
- Certified Identity Management Professional. CIMP-certified professionals prove their ability to develop and implement identity management systems and services that can streamline IAM processes, improve workflow and coordinate activity tracking and reporting at scale. CIMP professionals typically participate and/or lead identity management project teams, analyze and recommend IAM solutions, and communicate IAM activities to key stakeholders and senior leadership.
- Certified Identity Protection Advisor. Geared toward professionals who select, develop, configure and deploy IAM technologies, the CIPA certification covers critical risk domains, including product selection and implementation, IoT and API security, and compliance assurance. CIPAs are considered theft management specialists. They typically provide support and guidance to customers who may need advice on addressing identity theft and its associated risks.
- Certified Identity and Security Technologist. The CIST professional is one who defines, develops and deploys IAM products to not only streamline IAM processes and reporting but also counter threats. Typical CIST duties include IAM technology leadership, planning and management services, including product development and facilitating the deployment of IAM systems.
- Certified Red Flag Specialist. The CRFS program is a registered workplace identity theft prevention training program based on the U.S. government's Red Flags Rule. A CRFS-certified individual can identify risks to consumer information to better protect against identity fraud and theft security incidents.
- Certified in Data Protection. The CDP program provides guidance in the development and management of data protection and system security initiatives. It is recommended for individuals who wish to learn about information security and data protection.
- Certified Metaverse Security Consultant. This final IMI certification recognizes proficiency in Web3 security and the metaverse. The CMSC certification course includes blockchain security training that examines metaverse cybersecurity topics and issues such as identity management, fraud prevention, risk management and compliance.
Microsoft Identity and Access Administrator Associate
Microsoft identity and access administrators design, implement and operate an organization's identity and access management systems by using Microsoft Entra ID, formerly known as Azure Active Directory. Candidates for the Identity and Access Administrator Associate certification must pass the SC-300 exam. Preparation includes taking several courses in the SC-300 series prior to the exam, which costs $165. Certification must be renewed annually.
Google Identity & Access Management Course
Administered by Codecademy, candidates learn how to manage access authorizations across an enterprise using Google Cloud IAM. While the course is targeted at Google customers, it can provide a good foundation for understanding IAM principles. The free course is part of a set of courses that serve as preparation for obtaining the Google Cloud Associate Engineer certification.
AWS Cloud Technology Consultant Professional Certificate
The course is designed for individuals wishing to become a cloud technology professional by gaining knowledge of AWS cloud services, including AWS Identity and Access Management. The certificate is achieved after completing nine courses addressing areas such as cloud administration, application development, project management, cloud automation, processing access requests and data analytics and databases. Courses are free. Upon completion of the nine modules, a certificate as an AWS Cloud Technology Consultant is awarded.
IBM Security Verify Badge
This credential demonstrates knowledge of IBM's IAM products, including Access Management, Directory Services, Identity Governance, and Privileged Identity Management. Candidates for the badge take free courses in IBM Security Verify, IBM Consumer Identity and Access Management solutions, access certification, and security architecture principles. They must demonstrate their knowledge using structured assessments prior to receiving the badge.
Cisco Certified Network Professional (CCNP) Security
One of several different CCNP certifications, CCNP Security focuses on network, cloud and content security, network access and other security issues. Considered a professional-level certification, this requires passing a core exam and one of seven CCNP Security specialization exams. The required core exam costs $400, and each specialization exam costs $300. Many training options are available.
Cisco Certified Internetwork Expert (CCIE) Security
This advanced certification demonstrates knowledge of planning, designing, deploying, operating and optimizing complex enterprise network security environments. To obtain the CCIE Security, candidates must pass a core exam and a hands-on lab exam to demonstrate technical proficiency. The required core exam costs $400, and the eight-hour lab exam costs $1,600. Many training options are available.
Red Hat Certified Specialist in Identity Management
Obtaining this certification demonstrates proficiency in creating, configuring, and managing Red Hat Enterprise Linux authentication services. The certified individual can install and configure Red Hat Identity Management as well as various identity management services. The exam is based on Red Hat Enterprise Linux 9 and Red Hat Identity Management 4.8. Costs, which vary depending on the location and training provider, typically average about $350.
Okta Identity Certifications
Okta provides identity-focused cloud products, including the Customer Identity Cloud and Workforce Identity Cloud. The company offers certifications for individuals working in Okta environments. Five certifications are available for Workforce Identity Cloud; one is available for Customer Identity Cloud. Digital badges are available for each credential.
- Okta Certified Professional. This is the primary certification. It focuses on knowledge of Okta technology and services. The exam, divided into two parts, includes hands-on use cases. The cost is $250.
- Okta Certified Administrator. This certification is designed to demonstrate proficiency in managing Okta environments. The exam is given in two parts and includes hands-on use cases. The cost is $250.
- Okta Certified Consultant. Once the Okta Certified Administrator has been achieved, the next level is Certified Consultant. These professionals have a high level of planning, implementation and administrative knowledge of Okta environments. The two-part exam includes hands-on use cases. The cost is $250.
- Okta Certified Developer. Individuals with this certification have high technical proficiency in all aspects of Okta technology. They can configure authorization arrangements using API access management and can implement single sign-on with OIDC, for example. The exam, in two parts, includes hands-on use cases. The cost is $250.
- Okta Certified Technical Architect. Okta's highest certification is awarded to individuals who demonstrate exceptional proficiency at designing and implementing IAM environments using Okta technology. Candidates for the exam must have achieved the four previous certifications. Contact Okta for details on exam scheduling and fees.
- Okta Certified Customer Identity Cloud Developer. Recipients of this credential are identity and access management professionals who design and implement Okta Customer Identity Cloud (CIC) products for B2B and B2C customers. This exam is also given in two parts and includes hands-on use cases. The cost is $250.
Ping Identity Certifications
Ping Identity offers the Ping Identity Platform for implementing identity and access management capabilities in enterprise environments. The company also offers certifications in various Ping products. The following are examples of key certifications:
- Certified Expert -- PingAccess. This recognizes the achievements of professionals responsible for advanced administration and deployment of PingAccess products. The cost of the exam is $495.
- Certified Professional -- PingAccess. Candidates include IT professionals responsible for administering and deploying PingAccess tools. The cost of the exam is $395.
- Additional certified expert/professional options. Certifications are available at the Expert and Professional levels for other Ping products, including PingDirectory, PingFederate, PingOne DaVinci, and PingOne. Pricing is $495 for Expert and $395 for Professional.
IAM and cybersecurity career paths
Regardless of the circumstances, having a certification is probably better than not having one, especially for IAM professionals or those wishing to move into IAM and cybersecurity.
The importance of IAM is confirmed by its market growth. A 2023 report by Credence Research predicted the value of the IAM market will grow to $62.4 billion by 2032, up from $16.2 billion in 2023. That growth and the ongoing changes in IAM will require professionals who can show they are current on the key concepts and best practices in identity management.
Editor's note: This article was updated in January 2025 to reflect changes in certifications programs and their pricing.
Paul Kirvan, FBCI, CISA, is an independent consultant and technical writer with more than 35 years of experience in business continuity, disaster recovery, resilience, cybersecurity, GRC, telecom and technical writing.
Katie Donegan contributed to this article.




