
arthead - stock.adobe.com
The benefits and challenges of managed PKIs
Managing a public key infrastructure is a difficult task. Discover the benefits and challenges of PKI as a service to determine if managed PKI would benefit your organization.
Public key infrastructure is critical to enabling users, devices, software and other digital assets to securely exchange data. But deploying, operating and maintaining an organization's PKI is a difficult task. A single mistake can cause disastrous consequences.
To maintain security but simplify the task, organizations are increasingly turning to PKI as a service (PKIaaS).
Let's look at the benefits and challenges of managed PKI offerings to determine if they're the best fit for your organization.
On-premises PKIs and PKIaaS
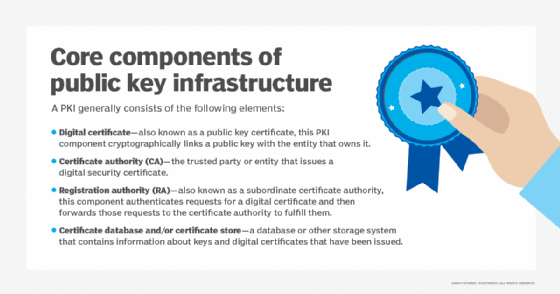
A PKI establishes certificate authorities (CAs) and uses them to issue and revoke digital certificates to confirm the identities of users, devices, services, software and other digital entities. Each certificate is based on the public key of a public and private key pair, and it is signed first by the certificate owner's private key and then the CA's private key.
When creating a PKI, security teams must start with a root CA, which is usually stored offline in a hardware security module (HSM) at a physically secure facility. The root CA is used to create a hierarchy of CAs and certificates, with each additional CA stored in its own HSM. A security incident could put the entire hierarchy at risk, so the root CA is only placed online when needed.
PKIaaS moves a PKI's hardware, software and service components -- including all the stored CAs -- from on premises to the cloud. The PKIaaS provider then becomes largely responsible for operating and maintaining the PKI. Most PKIaaS offerings are subscription-based and provide APIs to integrate the service into an organization's system.
The benefits of PKIaaS
PKIaaS offers the following benefits typically associated with cloud-based services:
- Organizations using PKIaaS can set up a PKI in minutes rather than weeks or months. They also don't need to buy and implement HSMs for CAs or establish data centers with physical security measures to protect offline root CAs.
- PKIaaS is highly scalable. If, for example, an organization needs to quickly issue multiple certificates, it could use PKIaaS to streamline this task.
- PKIaaS providers offer around-the-clock monitoring and support.
Additional benefits specific to PKIaaS include the following:
- Due to the nature of the service, PKIaaS providers typically have more experience with PKIs than internal IT and security teams.
- PKIaaS providers have the physical and digital security measures needed to protect CAs, systems and cloud data centers. Providers also build their systems and security architectures with resilience in mind.
- PKIaaS is highly automated, especially when it comes to certificate lifecycle management activities. When a certificate is due to expire, for example, PKIaaS can ensure the old certificate is revoked and a new one is issued and distributed. Forgetting to renew certificates is a common mistake that has caused costly outages at many organizations. PKIaaS also provides a single interface for PKI management. In short, PKIaaS helps reduce complexity for organizations.
The challenges of PKIaaS
The most common challenges with PKIaaS are generally the same as other cloud-based offerings:
- A PKIaaS provider could have insider threats that affect their clients. The risk, however, is probably less than the risk of insider threats at the client's organization. Organizations should conduct audits of their PKIaaS provider or review third-party audits to confirm that their provider is following best practices.
- Organizations may face lock-in issues if they decide to change PKIaaS providers. Companies should choose a CA-independent PKIaaS provider to avoid this problem.
- A PKIaaS provider might not support all certificate use cases, especially if an organization uses certificates in uncommon ways. Companies should ask which use cases a provider supports.
For most organizations -- whether large, small or somewhere in between -- the benefits of PKIaaS greatly outweigh the challenges. Organizations can avoid these challenges altogether by doing thorough research when evaluating PKIaaS providers and offerings.





