What is a public key certificate?
A public key certificate is a digitally signed document that serves to validate the sender's authorization and name. It uses a cryptographic structure that binds a public key to an entity, such as a user or organization. The digital document is generated and issued by a trusted third party called a certification authority (CA). Public key certificates are also known as digital certificates.
The common fields found in public key certificates include the following:
- Serial number. This number distinguishes the certificate from other certificates.
- Subject distinguished name. This is the name of the identity to whom the certificate is issued.
- Algorithm information. The issuer uses this algorithm to sign the certificate.
- Issuer. This is the name of the CA that issued the certificate.
- Validity period. These are the start and end dates that define when the certificate is valid.
- Subject public key information. This is the public key that is associated with the identity to whom the certificate is issued.
What is a public key certificate used for?
Public key certificates include the identity information about the owner who is authorized to use the key pair and the name of the issuing CA. The aim of these certificates is to verify that the sender of digital information is authorized to send that information.
By ensuring that only approved parties have access to specific information, the certificates help ensure the security and integrity of online transactions and communications. For this reason, they are important for maintaining cybersecurity and streamlining access management.
How does a public key certificate work?
Public key certificates form a part of a public key infrastructure (PKI) system that uses asymmetric encryption technology to secure messages and data. Here, asymmetric refers to the use of a pair of encryption keys by the public key certificate, one of which is public and the other is private.
The public key is made available to anyone who wants to verify the identity of the certificate holder, while the private key is a unique key that is kept secret. This enables the certificate holder to digitally sign documents, emails and other information without a third party being able to impersonate them. They can thus prove that they are who they say they are, encouraging recipients of their information to trust them and the transaction.
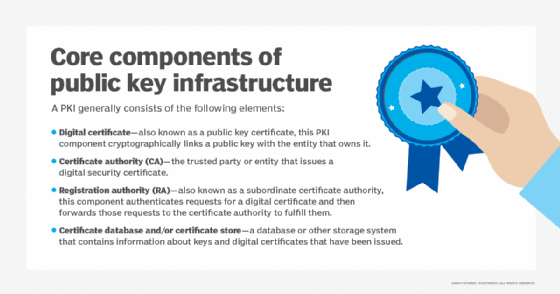
PKI components and role in public key certificates
Public key encryption, where two keys are used to encrypt and decrypt information, is a crucial element of PKI. The other main components of PKI from the context of public key certificates are the CA, registration authority (RA), and certificate database or store.
Both the CA and RA are trusted third parties. The RA verifies the identity of the entity requesting a digital certificate and submits relevant information to the CA. The CA then issues the certificate.
The database is a central repository of public key certificates. It contains the public keys assigned to various entities within the PKI system. The repository enables users to access and validate the public keys issued by various CAs. Private keys are not stored in the directory since they are meant to be private or available only to the authorized recipient of an encrypted message.
Role of certification authorities in public key certificates
The CA is a trusted third party that issues digital certificates. These certificates verify the identity of parties when they exchange information over the internet. Anyone wishing to obtain a public key certificate, whether for an individual entity, an organization or a website, must go to a CA. The certificate, which is signed by the CA using its private key, provides assurance of the entity's identity.
The CA establishes this assurance by validating the identity of the person who requests the certificate. In doing so, the CA and certificate indicate that the person identified in the certificate is the only one with access to and control of the private key. This is important to identify and authenticate authorized users and to maintain the integrity of transactions between authorized senders and recipients.
Types of public key certificates
There are different types of public key certificates for different functions, such as authorization for a specific type of action.
Transport Layer Security/Secure Sockets Layer certificates
These certificates are the core of Transport Layer Protocol (TLS), which is an updated version of Secure Sockets Layer (SSL). These digital files contain a public encryption key that is used to validate server identity and a digital signature to ensure the integrity and the source of data and other information transmitted online. These certificates facilitate the exchange of encryption keys between web servers and browsers, which enable a secure connection.
The chain of trust, trust path or trust chain is a sequence of certificates that a web browser must traverse to verify that a particular website is authentic and, therefore, secure. It typically includes a root certificate, intermediate certificate and leaf certificate.
There are multiple types of SSL/TLS certificates:
- Domain validation (DV) certificates. These certificates are typically the most basic and most affordable type of certificate web browsers trust. DV certificates require that the domain name of an organization is verified by the issuing CA before they are issued. These certificates can be issued within minutes and do not require the website owner to prove their identity. When a browser sees a DV certificate, it trusts that the owner of the domain is indeed the owner of the certificate and that the certificate is only meant for that specific domain.
- Organization validation (OV) certificates. This is a process of validating the identity of the root CA, followed by a validation of the business or organization requesting the certificate. An OV certificate is one of the ways that organizations can be validated for quality assurance through a formal and accredited process.
- Individual validation (IV) certificates. These certificates are issued to individuals rather than organizations, making them popular choices among consumers, particularly for securing email.
- Extended validation (EV) certificates. These certificates are issued after an extensive vetting process by both a CA and the CA's reputation partners. Under the EV guidelines established by the CA/Browser Forum, the applicant must meet the validity requirements and submit proof of their identity. Also, the organization must pass an independent audit. The combination of these factors provides an extra layer of trust in the site owner's identity. Companies issuing EV certificates are also required to pass an independent audit.
- Client certificates. While less common than server certificates, client certificates authenticate the identity of the user who wants to connect to a TLS service, rather than a device seeking a connection.
Email certificates
Secure/Multipurpose Internet Mail Extensions is a standard for sending encrypted email. Rivest-Shamir-Adleman security created it to resolve the problem of sending encrypted email without the need to exchange a public key. It is commonly used within an organization that has its own CA.
EMV certificates
Europay, Mastercard, Visa (EMV) payment cards have an embedded microchip containing a card issuer certificate. The embedded microchip enables the EMV payment card to generate a unique code for each transaction. In the case of EMV certificates, Europay, Mastercard and Visa are the CAs.
Code-signing certificates
Code-signing certificates are used in software development and IT operations to digitally sign the software or firmware of an application or device. This provides recipients with assurance about who created the code and the integrity of the code.
Root certificates
A root certificate is a digital certificate that is used to sign other digital certificates. Since it is at the top of a hierarchy of digital certificates used to verify other digital certificates, it is sometimes referred to as a trust anchor. The hierarchy starts with a root certificate, which is the highest level of certificate. The root certificate is verified by a second-level certificate, which is verified by a third-level certificate and so on.
Intermediate certificates
Intermediate digital certificates are used to sign other certificates and are best used as a bridge between a root CA and a subordinate CA. They are also used to sign end-user certificates that a website or a local server uses. The root certificates verify the identity of the intermediate certificate, which, in turn, verifies the end-user certificates.
Leaf certificates
A leaf certificate, or an end entity, is the endpoint for the signing and encrypting of data and cannot be used to sign other certificates. These include SSL/TLS, email and code-signing certificates.
Self-signed certificates
A self-signed certificate is a certificate that is signed by the same entity to whom it is assigned. Most certificates can be self-signed and are verified by their own public key. They are not signed by a CA, which means they might be perceived as less trustworthy.
Advantages and disadvantages of public key certificates
The main advantage of using public key certificates is that they enable secure authentication. The integrity of the public key certificate is guaranteed by the CA. Further, this type of certificate prevents man-in-the-middle attacks, which occur when a malicious third party intercepts the communication between two entities and relays the message between them. Lastly, public key certificates are supported by many enterprise networks and applications, and the certificate issuance process is transparent and efficient.
The biggest disadvantage of public key certificates is the entity's lack of control over the encryption key. This means that, if the certificate is compromised, it cannot be revoked. Someone could hack into the server to steal the certificate and use the public key in the certificate to decrypt any information that was encrypted with the public key. A fraudulent root certificate can be installed, and a browser does not provide warning when a web certificate is changed.
Before buying a digital certificate, review this buyer's handbook to learn how it works, which features are a must and how to evaluate the available options.






