
How to enable Active Directory fine-grained password policies
Specifying multiple password policies customized to specific account types adds another layer to an organization's security posture. Using PSOs instead of Group Policy can help.
Fine-grained password policies enable security and Active Directory admins to define password settings for individual user accounts and global groups. This enables far greater security than the Group Policy Default Domain Policy, which enforces a single password policy for all domain members.
Read on to learn how to enable fine-grained password policies using the graphic AD Administrative Center, as well as Windows PowerShell.
Fine-grained password policy examples
Admins can create fine-grained password polices for different types of accounts, including user accounts and global groups that need modified password requirements. Note, these are not Group Policy settings and, therefore, not linked to organizational units.
Learn about four sample identities -- IT admin accounts, service accounts, executive accounts and contractor accounts -- and how to define a Password Settings Object (PSO) for them.
How to create a PSO
Now that a PSO is defined, it's time to apply it to users and groups.
Launch AD Administrative Center from the Server Manager Tools menu. Select your domain, and browse to System, Password Settings Container. To input your new PSO, right-click the Password Settings Container, and select New.
Fill in the values for your first group. In this example, I use the values for the itadmins_fgpp group.
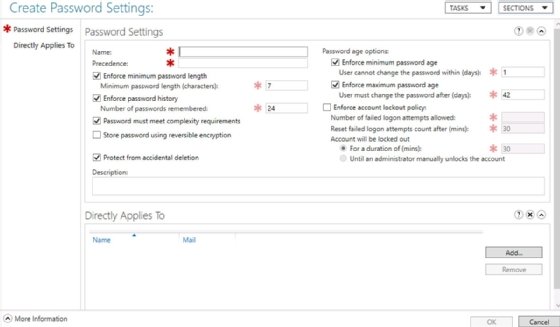
Use the Description box to explain why the PSO exists and why the users or groups require specialized settings. This is especially helpful as a courtesy to future admins who may not understand why you chose these particular configurations.
Admins can either link the PSO to users and global groups during the creation process or return to the PSO and select additional users and global groups in the future. To apply the PSO, select Add in the Directly Applies To box, and browse to the chosen users or groups.
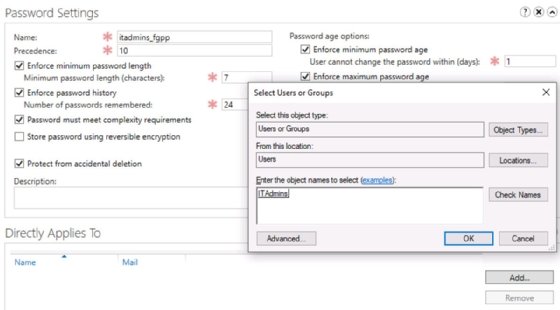
Follow the same steps to create other PSOs. As you configure each PSO, name it, set the precedence value, and populate the password requirements and lockout settings based on the design.
How to view a user's or group's settings
Troubleshooting password issues for users can be complex with fine-grained password policies. In the past, help desk technicians had a single password policy to communicate to users who called in with questions. Because everyone's password requirements were the same, it was easy to tell a user to select a password that was at least 14 characters and that did not repeat the last 10 passwords.
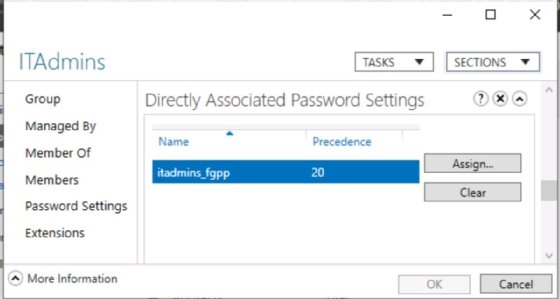
Fine-grained policies aren't as easy. To view a group's password requirements, browse to the group, right-click the group name and select Properties. Choose the Password Settings button to view which PSO is applied.
Supply the help desk with a knowledge base entry containing the detailed settings for each PSO. If someone calls for help, it will be easier for help desk techs to respond.
How to enable fine-grained passwords using PowerShell
PSOs can also be created and applied using PowerShell.
Use the New-ADFineGrainedPasswordPolicy cmdlet to create a PSO and populate its settings. Note, it may be easier to write the PSO in the PowerShell Integrated Scripting Environment and confirm its syntax before running it. Parameters exist for each possible password configuration, including precedence and lockout settings:
PS C:\> New-ADFineGrainedPasswordPolicy -Name "itadmins_fgpp" -Precedence 20 -ComplexityEnabled $true -Description "Restrictive password settings for all IT administrator accounts" -DisplayName "itadmins_fgpp" -LockoutDuration "0.00:00:00" -LockoutObservationWindow "0.00:30:00" -LockoutThreshold 3
Apply the PSO to a user or global group using the Add-ADFineGrainedPasswordPolicySubject cmdlet. The -Subjects parameter defines the global group or user to which the setting applies:
PS C:\> Add-ADFineGrainedPasswordPolicySubject -Identity itadmins_fgpp -Subjects 'ITAdmins'
Note that the -WhatIf parameter shows the result of running the cmdlet without applying the settings.
The Get-ADFineGrainedPasswordPolicy displays PSO settings. Use the -Identity parameter to specify which policy PowerShell displays:
PS C:\> Get-ADFineGrainedPasswordPolicy -Identity itadmins_fgpp
Don't forget documentation
Documentation is a key element of implementing fine-grained password policies in AD. Many IT support specialists reference these policies when troubleshooting or running security audits. Create the proper documentation for not only your team, but also future IT staff.








