
peshkov - stock.adobe.com
How to create fine-grained password policy in AD
Fine-grained password policies are a simple and effective way of ensuring password settings meet business requirements.
Standard Active Directory configurations include a single password policy for all domain members, enforced domain-wide via Group Policy through the application of the Default Domain Policy. While Group Policy has thousands of options and is powerful and flexible, it cannot apply the fine-grained password policies that many of today's organizations need to stay secure.
To meet organizations' needs, Microsoft began offering fine-grained password policy options of Password Settings Container and Password Settings Objects with Windows Server 2008.
Getting started: Why fine-grained password policies?
Those of us who have evolved with Active Directory (AD) likely followed -- or still follow -- the mantra that one password policy rules the entire domain. Forget that assumption.
Today's environments have multiple different users and groups that may require different password policies. Maybe you want to separate user accounts and service accounts -- or standard users and privileged users. Or maybe you want to synchronize passwords with other authentication providers.
You can do this with fine-grained password policy options.
Fine-grained password options
Fine-grained password policies are deployed via Password Settings Objects (PSOs), which are stored in the Password Settings Container.
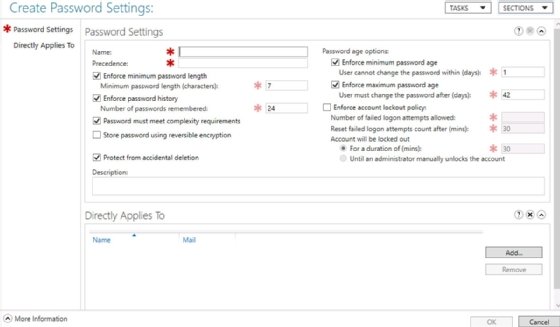
A PSO offers the same password settings from Default Domain Policy options, including standard settings -- for example, minimum password length, minimum password age and minimum password age -- and account lock settings, such as threshold, observation window and duration. It also includes the following fine-grained policy-specific settings:
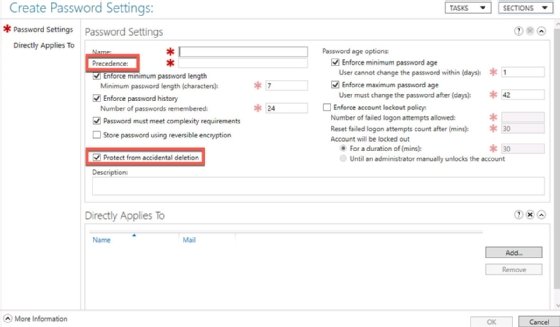
- Precedence. This sets the priority of the PSO when an account has two or more PSOs applied to it. Note, a lower number has a higher precedence. Consider a CFO who has "executive" and "finance" PSOs applied. If the executive PSO has a precedence value of 20 and the finance PSO a precedence level of 30, the executive PSO would overrule -- have precedence over -- the finance PSO. A PSO with a precedence value of 10 would precede over an executive policy. Carefully consider precedence values when defining PSOs.
- Protect from accidental deletion. This setting, if checked, protects a PSO from being deleted from AD by mistake.
Note, any account without a PSO applied is subject to the password requirements defined in the Default Domain Policy.
In older networks, ensure the domain functional level is at least Server 2008. This shouldn't be a problem for most modern AD environments.
Designing a fine-grained password policy
Before a PSO can be implemented, it must be created. First, identify the types of accounts that need specialized password requirements. For the sake of example, here, we look at the following four identities:
- IT admin accounts.
- Service accounts.
- Executive accounts.
- Contractor accounts.
Next, document password settings for each type.

IT admin accounts
- Name: itadmins_fgpp
- Description: Restrictive password settings for all IT administrator accounts.
- Password history: 20 passwords
- Maximum password age: 30 days
- Minimum password age: 1 day
- Minimum password length: 15 characters
- Complexity enabled: Yes
- Enforce account lockout policy: Checked
- Number of failed logon attempts allowed: 3
- Reset failed logon attempts count after (mins): 30 minutes
- Account will be locked out: Until an administrator manually unlocks the account
- Precedence: 20
Service accounts
- Name: serviceaccounts_fgpp
- Description: Restrictive password settings for all service accounts.
- Password history: 10 passwords
- Maximum password age: 365 days
- Minimum password age: 1 day
- Minimum password length: 30 characters
- Complexity enabled: Yes
- Enforce account lockout policy: Unchecked
- Precedence: 30
Executive accounts
- Name: executives_fgpp
- Description: Password settings for members of the executive team.
- Password history: 20 passwords
- Maximum password age: 45 days
- Minimum password age: 1 day
- Minimum password length: 15 characters
- Complexity enabled: Yes
- Enforce account lockout policy: Checked
- Number of failed logon attempts allowed: 3
- Reset failed logon attempts count after (mins): 15 minutes
- Account will be locked out: Until an administrator manually unlocks the account
- Precedence: 40
Contractors
- Name: contractors_fgpp
- Description: Password settings for contractors, temporary employees and other guests.
- Password history: 20 passwords
- Maximum password age: 15 days
- Minimum password age: 1 day
- Minimum password length: 12 characters
- Complexity enabled: Yes
- Enforce account lockout policy: Checked
- Number of failed logon attempts allowed: 3
- Reset failed logon attempts count after (mins): 15 minutes
- Account will be locked out: Until an administrator manually unlocks the account
- Precedence: 50
Create a global group for each account type, and add the accounts to the appropriate groups. It's almost always more efficient to link settings to groups than individual users. These are sometimes called shadow groups and contain the same members as an organizational unit in AD.
Learn how to configure and implement PSOs and apply them to users and global groups.








