
Getty Images
Enable vSAN data-at-rest encryption for extra VM security
Data-at-rest encryption secures data all the way down to the storage level. Increase VM security in a couple of steps and vSphere's built-in native key provider function.
VMware data-at-rest encryption enables IT administrators to protect their encrypted vSphere vSAN data stores and the corresponding VMs within those data stores.
Data-at-rest encryption was first available in vSphere 6.5 but required external key management system (KMS) software. In version 6.6, VMware finally implemented an in-house KMS offering that is easy to use.
The vSphere 7.0 Update 2 introduced the native key provider (NKP) feature, which uses an internal encryption mechanism instead of external software to provide the KMS function. The NKP does not have everything that a full-fledged KMS offers but is enough for vSAN encryption.
How VMware vSAN data-at-rest encryption works
VSAN uses encryption keys, so when admins enable encryption, vSAN encrypts all data stores content. Only admins with encryption privileges can encrypt or decrypt.
Data-at-rest encryption protects vSAN storage data. This encryption type only starts after all other processes -- such as deduplication and compression -- finish. Data at rest is a protective measure in case a device is removed from the cluster or the cluster is stolen.
In vSAN 7.0 Update 3 and later, data-at-rest encryption adds more resiliency, so the software can continue to encrypt data even if the KMS has downtime or experiences issues. KMS stores the encryption keys on the hypervisor's trusted platform module (TPM) device.
If the hosts are without a TPM device, admins can enable encryption key persistence via a command-line interface (CLI) command. With key persistence enabled, the ESXi hosts can keep the encryption keys after a reboot without the need to request them again from the KMS.
Encryption operations can continue when the key server is not available because the keys persist in the TPM or ESXi cache.
VSAN data-at-rest encryption requirements
There are two main requirements to run vSAN data-at-rest encryption. The first is to have a KMS. Previously, it was a necessity for admins to purchase an additional external KMS software to use vSAN encryption, but the release of vSphere 7 U2 includes an internal offering called NKP.
The second is to have vSAN with a license that allows data-at-rest encryption; only vSAN Enterprise and Enterprise Plus provide this feature. Admins with Standard or Advanced editions must upgrade vSAN before they put data-at-rest encryption in place.
If admins run shared storage for their clusters, then a vSAN encryption setup is not the ideal choice for data-at-rest encryption.
Admins must use approved hardware from the VMware hardware compatibility list to use vSAN encryption on vCenter servers. VSAN ReadyNodes, which is hardware preapproved for vSAN use and configurable to infrastructure needs, is also an option.
Implement and deploy vSAN data-at-rest encryption
VSAN data-at-rest encryption requires a KMS or NKP. This is done through the vSphere web client in five steps.
First, connect to the vSphere environment via vSphere web client and Select your vCenter server > Configure > Security > Key Providers > Add.
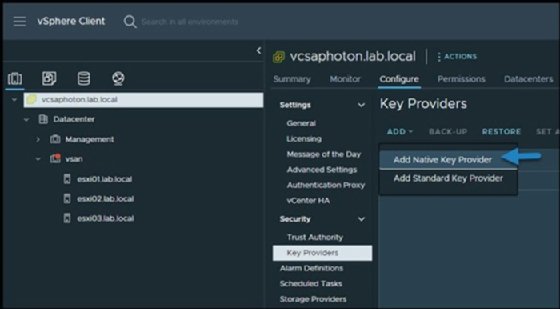
Second, name the NKP. Make sure the NKP name is easy to rediscover or remember.
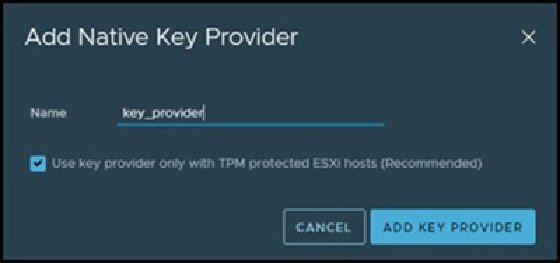
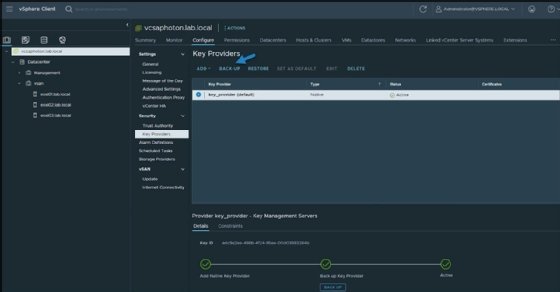
Third, as a best practice, create a backup before the NKP runs. To password protect the NKP, admins can click on a link that provides the option to password protect the NKP. Backup creation is not a mandatory step to run data-at-rest encryption, but highly recommended.
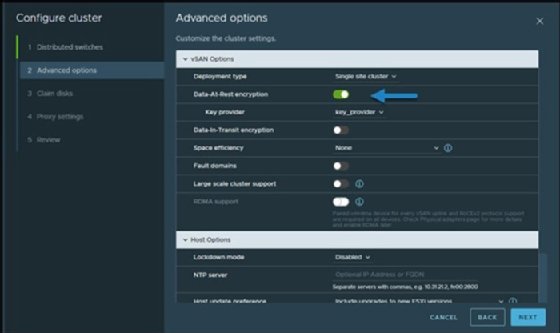
Fourth, enable data-at-rest encryption during vSAN cluster creation and select the newly created NKP. This option is in the Advanced Options menu for cluster configuration.
Finally, determine which services run with vSAN data-at-rest encryption with Select your cluster > vSAN Services > Edit.
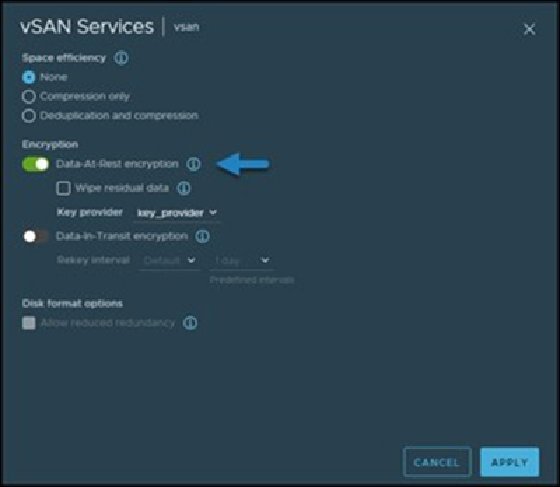
This completes the workflow to set up vSAN data-at-rest encryption and adds an extra protection layer to any VMs on a VMware vSAN cluster.








