
rvlsoft - Fotolia
Stay in control with Azure AD Privileged Identity Management
Rampant use of elevated privileges can prove hazardous to enterprises. Rein in access and manage resource access with help from this Azure Active Directory feature.
While the growing shift to cloud services lightens the data center footprint, the added responsibility to secure the expanded attack surface can weigh down the most diligent of administrators.
Online services, such as Office 365 apps, are easily accessible through a browser without the need for physical access or a VPN. All it takes is one set of leaked administrative credentials for a threat actor to take control of the organization's servers and cloud services. Administrators have been using principle of least privilege to decrease the use of administrative roles to reduce the risk if a breach occurs and limit the damage by attacks launched from privileged accounts. While security services such as Azure AD Privileged Identity Management streamline the process to manage elevated roles, the system still requires administrators to monitor and audit the access granted to users to maintain compliance with the organization's access policies and restrictions.
Why elevated permissions can lead to problems
Threat actors continue to target privileged accounts to gain access to important resources. By placing restrictions on the widespread use of elevated permissions, attackers would have less ability to move laterally and companies would limit the effects of breaches.
To help reduce these potential risks of damage associated with elevated rights, Microsoft's Privileged Identity Management provides the functionality to limit who has access to what and for how long. As a service in Azure AD, Privileged Identity Management integrates with Microsoft Active Directory to assign elevated administrative privileges to resources on a temporary basis to admins and contractors when needed. Azure AD Privileged Identity Management lets users request an administrative role in Office 365, such as global admin, or security administrator and other permissions in Azure to make changes. These requests come through the Azure portal.
Azure AD Privileged Identity Management addresses security needs in three key areas.
1. Workflow automation to streamline and validate elevated access
IT only requires admin access in specific instances: during a configuration change, a review of the Office 365 admin portal or during an application installation on some systems. Azure AD Privileged Identity Management uses an approval workflow that routes the access request to the appropriate individuals within the IT team to validate and approve the activation of the privileged role.
Azure AD Privileged Identity Management's just-in-time access feature automatically removes the assignment role given to a user after a specific time period that IT configures per role or request.
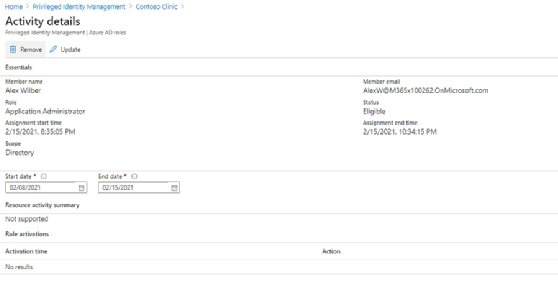
2. Enforcement of policies for those with elevated access and for their roles
Azure Active Directory Privileged Identity Management gives administrators the option to grant admin access to a user while still requiring them to use multifactor authentication. This additional restriction ensures the identity of the individual requesting the privilege when a new role is activated for a user.
Azure Active Directory Privileged Identity Management provides the ability to customize roles and adjust the available settings for each. This gives the organization the flexibility to have different configurations based on the different IT requirements.
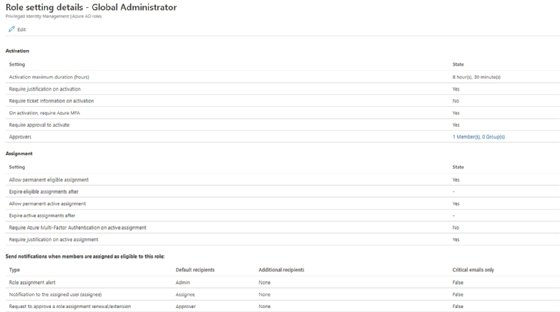
3. Monitoring and assessment capabilities for AD roles
For large organizations with frequent requests for elevated privileges, Azure Active Directory Privileged Identity Management offers an efficient way to review any outstanding roles that may need to be revoked or reevaluated. The access review feature scans outstanding elevated access and generates a comprehensive view of the requests and their statuses. The platform provides additional reporting capabilities for auditing.
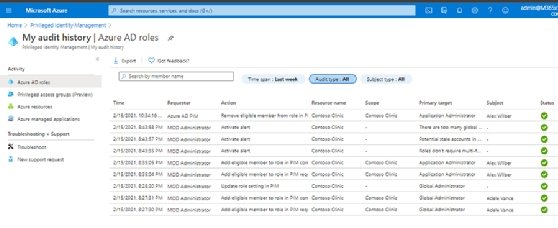
Deployment stages for Azure AD Privileged Identity Management
To use Azure AD Privileged Identity Management, an organization must have at least one of the following licenses or bundles: Microsoft Azure AD Premium P2, Enterprise Mobility + Security E5, Microsoft Enterprise 365 E5 or Microsoft 365 Education A5.
To deploy Azure AD Privileged Identity Management, administrators need to configure the service to interact with the on-premises Active Directory.
The next step is to prepare the different roles for assignments. The roles can already exist, such as the built-in ones in Office 365 or Azure, or custom roles that the IT organization builds with specific privileges within their Active Directory.
After defining the roles, the organization identifies the appropriate stakeholders to participate in the approval process and review of role assignment requests. Generally, there are three types of users who will interact with the system and need to be defined:
- the individual(s) who needs to sign off on a request for elevated permissions or assigned roles;
- the individual(s) who needs to review the request and provide input on it; and
- the individual(s) who needs to be informed of the role assignment, usually help desk and the users who make the request.
After this process, IT can draft their role assignment and overall policies to implement for each elevated role.






