What is IT/OT convergence? Everything you need to know
IT/OT convergence is the integration of information technology systems with operational technology systems. IT systems are used for data-centric computing; OT systems monitor events, processes and devices, and make adjustments in enterprise and industrial operations.
Modern organizations grapple with two worlds. There is the traditional physical world composed of machines, electromechanical devices, manufacturing systems and other industrial equipment. Then there is the more recent digital world using servers, storage, networking and other devices used to run applications, process data and even make critical decisions without human intervention. These two worlds have largely occupied separate domains, shared little -- if any -- meaningful data or control and relied on oversight from business staff with distinctly different skill sets.
Today, the worlds of IT and OT are converging. Advances in technologies such as the internet of things (IoT) and big data analytics are systematically enabling the digital information world to see, understand and influence the physical operational world. When implemented properly, IT/OT convergence can merge business processes, insights and controls into a single uniform environment.
What is OT?
OT focuses on the management and control of physical devices existing and operating in the physical world. The control of real-world devices is as old as industry and manufacturing itself. The introduction of electronics and digital technologies over time also found plentiful uses in operational control systems, such as computerized numerical control (CNC) machining systems.
Where IT focused on data and communication, OT focused on behaviors and outcomes. Most control systems employed across industrial and manufacturing installations weren't networked, resulting in silos of specialized devices -- each electronic at some level, but not readily able to communicate or share information. This means human operators were tasked with programming or managing the physical operations of each piece of equipment. Even equipment that provided centralized control used closed or proprietary protocols.
Consider a traditional automobile. Although a modern vehicle contains a wide array of electronic devices, it remains an unintegrated and singular system. The vehicle might record data but doesn't share data and doesn't enable any overarching management or control. It functions in all real-world conditions but relies solely on the capabilities and experience of a human operator for successful operation.
What's the difference between IT and OT?
IT includes any use of computers, storage, networking devices and other physical devices, infrastructure and processes to create, process, store, secure and exchange all forms of electronic data.
OT, traditionally associated with manufacturing and industrial environments, includes industrial control systems such as supervisory control and data acquisition.
The problem is that IT and OT were never integrated. For example, a CNC machining station on a factory floor might be fully digitized, and it might bear proprietary connectivity to other similar machines, but it never connected to the enterprise LAN where other business data, such as spreadsheets and PDFs, were exchanged. Thus, the status, behaviors and outputs of that isolated machine in the OT world were never really available to the broader enterprise for analysis and control. Today's technologies are finally enabling such integrations.
One technology that fostered the integration between IT and OT was the development and deployment of IoT devices. IoT devices include a wide assortment of sensors for gathering real-world conditions, such as temperature, pressure, dimensional measurements, chemical compositions and countless other physical parameters. IoT devices also include an array of actuators, such as motors and solenoids, that translate digital commands and instructions into physical actions, such as controlling valves and moving mechanisms. Each IoT device is designed to communicate over standard networks, enabling them to exchange OT data with IT resources -- servers and storage -- sometimes over considerable distances.
Consider a wind turbine. By itself, a wind turbine would be classified as OT industrial equipment, and it would include all of the equipment and electronics necessary to generate power and connect that power to the grid. But that's all. By including IoT devices to drive IT/OT convergence, the wind turbine could use sensors to detect wind direction and intensity while communicating its output and status to a centralized controlling location. The central facility would analyze the data, provide commands needed to autonomously configure the wind turbine for optimum performance in current weather, and create work orders for maintenance based on operating time and condition sensor data, such as vibration or wear.
While IT inherently covers communications as a part of its information scope, OT hasn't traditionally been networked technology -- meaning connected to a larger network such as a LAN or the internet. Many devices for monitoring or adjustment weren't computerized. Those OT systems with compute resources generally used closed proprietary protocols and programmable logic controllers rather than technologies that afford full computer control. The systems involved often relied on air gapping -- the deliberate choice to forego network connections -- for security.
As IT reaches more OT systems, air gaps can't provide adequate security for network communication and OT data. Organizations driving IT/OT convergence must educate and train staff to understand and implement adequate security. This often involves a mix of cross-hiring, cross-training and close observance of regulations, such as the GDPR and California Consumer Privacy Act, in the context of both IT and OT in terms of data security, privacy and protection.
IT/OT convergence project success and overall security can benefit from a range of initiatives involving project teams, including the following:
- Having an IoT sponsor.
- Keeping OT and IT in the same loop.
- Understanding how to design IoT.
- Understanding how to integrate IoT.
- Training staff and developing expertise.
- Planning for scale.
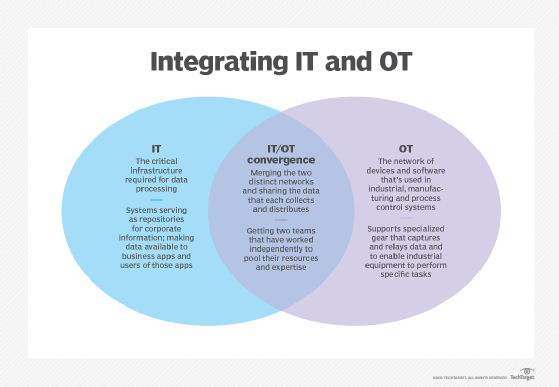
What is IT/OT convergence?
The idea of technological convergence isn't new. By enabling different technologies to integrate and interoperate efficiently as a single cohesive system, businesses can improve efficiency, reduce errors, cut costs, enhance workflows and gain measurable competitive advantages.
Enterprise IT has long been a focus of convergence efforts, bringing often-disparate data center technologies together and supporting seamless interoperation. One example of convergence is the appearance of IT converged infrastructure -- later evolving into hyperconverged infrastructure. These developments merge traditionally separate servers, storage, networking and management tools into a single, cohesive, singularly deployed and centrally managed product.
The idea of IT/OT convergence seeks to bring physical -- OT -- equipment and devices into the digital -- IT -- realm. This is possible because of advances such as machine-to-machine communication, as well as the introduction of sophisticated IoT sensors and actuators that can be fitted to physical equipment. These devices can employ wireless communication over standardized networking protocols, such as TCP/IP, to communicate the relevant data from each physical system back to a central server for monitoring and analysis. The results of that analysis can then be passed back to the physical system to enable more autonomous operation, enhance accuracy, benefit maintenance and improve uptime.
Consider how this affects everyday technologies, such as vehicles. The addition of sensors, actuators and standardized communication enables a vehicle to pass real-time position, movement and condition data back to a collection point for analysis. At the same time, instructions and real-time data, such as traffic and weather, can be passed to the vehicle. This can help a human driver make better driving decisions, such as finding alternate routes or servicing the vehicle before breakdowns occur. But this kind of IT/OT convergence is also the underpinning of autonomous vehicle, also known as self-driving vehicle, technology.
Types of IT/OT convergence
Convergence isn't a single initiative or effort. Convergence initiatives can take a variety of directions depending on the needs and goals of the particular organization. There are three main categories of IT/OT convergence:
- Process convergence covers the convergence of workflows. IT and OT departments must reform their processes to accommodate each other and make sure important projects are communicated. This is an organizational convergence, dealing with the structure of the internal business. For example, a business might follow specific processes for storing and protecting IT data, but this process might be adapted or extended for converging OT systems.
- Software and data convergence deals with getting the software and data in the front office to work to address OT needs. This is a technical convergence involving the network architecture of the business. For example, IT might need to implement new tools to gather OT data and combine OT and IT data for analysis. For example, future business analytics and decision-making might include data collected and processed for OT systems as well as IT systems.
- Physical convergence includes physical devices being converged or retrofitted with newer hardware to accommodate the addition of IT to traditional OT. This is an operational convergence, where the hardware itself is updated and maintained over time. This might include the purchase of new OT systems or the addition of aftermarket devices to facilitate data communication and control.
IT/OT convergence industry examples and use cases
Increasingly, sensors and connected systems, such as wireless sensor and actuator networks, are being integrated into the management of industrial environments, such as those for water treatment, electric power and factories. The integration of automation, communications and networking in industrial environments is an integral part of IoT and is often referred to as Industry 4.0. Today, some technology leaders envision an impending convergence of human intelligence and AI that might come to signify a fifth industrial revolution -- sometimes called the cognitive age -- though that point of inflection has not yet occurred.
Here are some industries that benefit from the convergence OT and IT:
- Manufacturing. IT/OT convergence enables organizations to be more cost- and resource-efficient by using sales and inventory data to drive manufacturing operations -- optimizing equipment and power use while minimizing maintenance and unsold inventory.
- Utility and energy companies. Modern IT enables OT teams to access operational data remotely, helping industries such as oil, gas and electricity to optimize industrial equipment inspections, make damage assessments and handle inventory monitoring and distribution.
- Transportation. Asset management is a priority in transportation. Integrating IT and OT can help rail, bus, delivery and other transportation organizations gain better visibility into the coordination, condition and usage of assets to guide short-term repairs, route optimization and long-term planning for asset replacement and safety.
- Military and law enforcement. IT/OT convergence can aid in the coordination and rapid deployment of resources, while providing more insight into the condition and maintenance of critical equipment.
- Communications and media companies. Regional and global communication providers can employ IT/OT convergence to oversee the performance and operation of equipment and quality of service, leading to faster troubleshooting and better user satisfaction.
- Retail. The use of IoT devices such as start product tags, along with other OT devices such as cameras and point-of-sale terminals, can deliver more data to IT for analysis, leading to inventory and sales floor optimizations for cost savings, as well as better revenue generation and shopper experience.
- Medical and pharmaceutical. IT/OT integration enables more medical devices to exchange and share patient information for real-time visibility, leading to better patient analysis and outcomes; meanwhile, convergence can improve the manufacturing of medicines to enhance and ensure product quality.
IoT and IT/OT convergence
IoT, especially when paired with edge computing, enables the IT portion of IT/OT convergence. As mentioned, OT devices aren't traditionally networked technology. IoT devices, by definition, are networked computing devices with the ability to collect, transfer and analyze data. Traditional OT devices -- sensors, for example -- can collect data, but can't transmit the data over a large network or perform any sort of in-depth analysis on that data.
Newer smart sensors would be able to collect the data from the source, such as a factory floor, and transmit it to an IoT hub or gateway, which would then transfer that information to an analytics application or an enterprise resource planning software platform to be integrated into an organization's unified system of business operations. When networked, an OT device functions as an IoT device. In the factory floor example, a sensor can collect operational data on materials or machines in the factory and send it over a wireless network to the back-end system application to be interpreted and trigger an action -- maintenance on factory equipment, for example.
The addition of edge computing capabilities to industrial internet of things (IIoT) devices enables real-time data processing closer to the source. Instead of sending the data over a network to a centralized location for processing, the IoT devices can analyze time-sensitive manufacturing process data on site and return insights quickly for direct monitoring of industrial conditions before it becomes obsolete. This is important because IoT and OT devices are often part of a distributed network architecture, making transmission to a central processing location difficult or impossible -- IoT is an important technology behind distributed or edge computing. These devices are also often responsible for critical industrial systems that, if shut down or interrupted, would incur severe consequences.
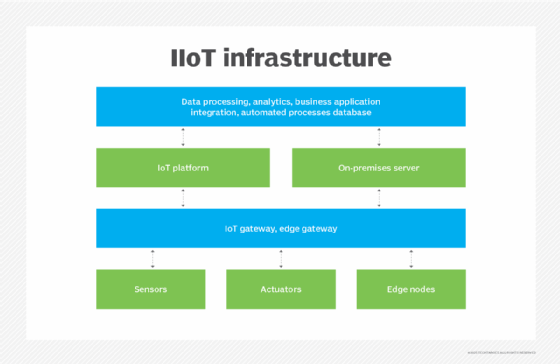
The addition of IT technology to OT enables organizations to make better use of data that's generated by OT through IoT devices and edge computing.
IT/OT convergence can pose challenges in IoT security. Convergence isn't just a blending of technologies, but also teams and processes. The addition of OT brings new stakeholders into the security environment. IT security teams and processes must incorporate the diverse real-time demands of industrial environments. For example, it's just not possible to shut down a smart grid for a few hours to apply patches or change configurations. In other cases, OT systems might be in place decades longer than IT systems, presenting additional security risks to consider and mitigate. But OT systems weren't built for internet connectivity and must be retrofitted with IoT devices and proper security controls.
There are five principal security threats to IT/OT convergence:
- Lack of collaboration. IT and OT teams have rarely worked together, and this can lead to security oversights that can increase complexity, duplicate efforts, increase operating costs and expose security flaws that attackers can exploit. To ensure security, disparate teams must prioritize, collaborate and communicate in ways that might not have been necessary or even possible in years past.
- Legacy OT systems. Where IT systems rarely last more than five years, OT systems, such as manufacturing machines, can have lifecycles that measure into decades. Such legacy systems typically incorporated few, if any, security features and can't be upgraded because of proprietary designs or protocols. Every converged system must be evaluated for security, and systems that can't support security requirements might demand new or updated OT equipment.
- Insufficient insight. IT routinely relies on asset discovery and configuration to provide a clear and complete picture of the environment being managed. OT systems must be able to share this environment, offer discoverability, and remote configuration and management. If an administrator can't see an OT device, they can't secure and manage the device. Such gaps can lead to security vulnerabilities.
- Mission-critical demands. OT production systems are often called upon to function 24/7, year-round and can't be paused or turned off for upgrades or updates without a significant loss of revenue or physical risk. Imagine turning off medical life support equipment for software updates. Organizations might ignore potential security vulnerabilities simply because they can't afford the cost of downtime needed to remediate risks.
- The effects of disruption. Although integration is seen as a positive thing, the effects of disruption can be potentially devastating. Consider what happens when a factory floor of active machinery suddenly can't communicate because of a network disruption, such as a network gear failure or external DoS attack. IT/OT convergence demands a careful assessment of resilience and fail-safe factors.

Benefits of IT/OT convergence
IT/OT convergence enables more direct control and more complete monitoring, with easier analysis of data from these complex systems, from anywhere in the world. This enables workers to do their jobs more efficiently and improves decision-making, as organizations, leaders and employees have access to real-time insights that converged data provides. Businesses including manufacturing, transportation, mining and other industrial organizations are embracing IT/OT convergence.
The following are some of the benefits of IT/OT convergence over separate IT and OT:
- Less siloed IT and OT departments, as the departments must share their respective areas of expertise to manage converged technology.
- Improved cybersecurity where IT and OT systems are blended and protected as a single unified environment, rather than two disparate systems.
- Reduced development, operational and support costs, as well as less unplanned downtime due to predictive maintenance enabled by IoT devices.
- Faster time to market for converged technology.
- Improved compliance with regulatory standards, as the addition of IT to OT enables better visibility, management and auditing.
- Improved automation and visibility into distributed OT because OT gains the ability to transmit real-time maintenance data.
- More efficient energy and resource usage, as OT systems can be engaged more in line with actual product needs.
- More efficient asset management because all IT and OT systems are seen and managed through a common methodology.
Challenges of IT/OT convergence
Digital transformation requires organizations to reform most or all areas of the organization to be successful. OT's modernization through IT integration is no different.
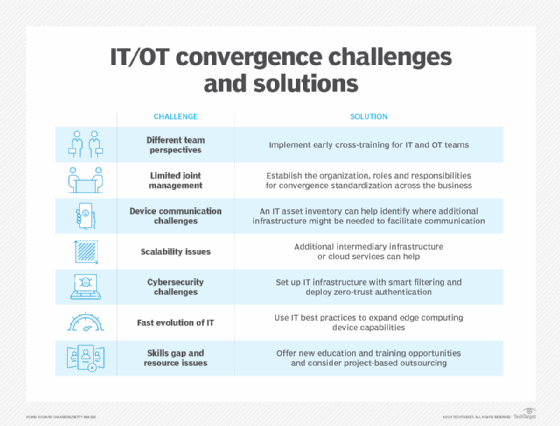
One oft-cited challenge of convergence is maintaining security. Many operational technology systems were never designed for standardized communication or remote accessibility, and as a result, the risks of connectivity weren't considered. Such systems might not be regularly updated. Additionally, OT systems are often distributed in nature, and are often relied upon to uphold critical infrastructure. Their distributed nature makes for a larger attack surface. The vulnerabilities of OT systems can leave organizations and critical infrastructure at risk of industrial espionage and sabotage.
But security concerns are not just technical. People play a vital role in IT/OT security. The parallel, and sometimes conflicting, roles and priorities of IT and OT teams leave ample opportunity for security oversights and vulnerabilities -- which can complicate proper governance. It's up to people to change the corporate culture to support IT/OT convergence, establish the communication and collaboration needed to approach convergence, and adjust the business policies and workflows that establish necessary security configurations and guidelines.
Other challenges of IT/OT convergence include the following:
- Process convergence. Organizations might struggle with reorganizing previously siloed IT and OT departments to manage and operate newly converged technology.
- Secure IoT implementation. Oftentimes, IoT initiatives aren't owned by any one department, and communication of a new project might not reach all departments -- especially in a more siloed organization. Typically, OT departments have limited knowledge of security, and IT has a limited knowledge of the projects currently underway. This can create a dangerous security gap with IoT deployments.
- Training. Only recently have certifications, such as the Cisco Certified Network Associate Industrial IoT, been offered to help OT workers understand how the technology they are accustomed to intersects with networked technology. Before that, there was little in the way of standardized courses for manufacturing process control. This means that older systems and staff might have previously been adhering to standards that vary from organization to organization, causing compatibility and security issues.
- Integration with existing systems. The business side of an organization might be tempted to replace technologies instead of modernizing existing OT with IT technology. This defeats one of the benefits of convergence, which is cost efficiency. The point of convergence is to do more with what is available.
IT/OT convergence strategies and best practices
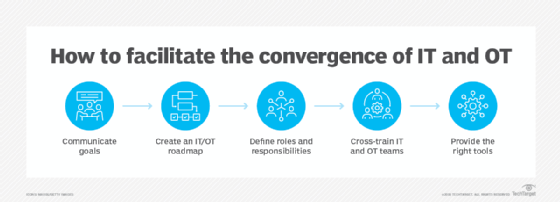
So, what's the right way to approach an IT/OT convergence initiative? Given the wide array of OT systems and industries that might opt for convergence, there are few clear paths that guarantee a successful convergence strategy. However, there are some general guidelines that can help an organization maximize its chances of success:
- Communicate goals. Develop a clear picture of the overall objectives and ensure that both IT and OT groups understand the convergence goals involved.
- Show the overlap. Illustrate the ways in which IT and OT will overlap for each team, especially in terms of systems management and security.
- Define the roles and responsibilities. Outline the duties, goals, roles and responsibilities for IT and OT teams, and focus on opportunities to collaborate.
- Provide training. Cross-training can help IT and OT groups develop a better sense of each other and understand each other's needs. In addition, a growing number of IT/OT convergence certifications are appearing to help organizations manage convergence projects more effectively.
- Use the right tools. Teams can work together to identify and deploy tools that can provide the appropriate amount of visibility and control over IT/OT assets. Tools should cover discovery, configuration, management and security.
- Measure and adjust. Goals should include clear metrics that can be measured to gauge the actual outcomes of IT/OT convergence. Take the time to implement those metrics and measure them with tools. Review metrics regularly and make constructive adjustments to the plan that can overcome any difficulties and refresh goals along the way.
The path toward any IT/OT strategy typically involves three distinct phases: organizational, technical and operational.
The organizational phase is intended to facilitate collaboration and communication by getting IT and OT teams to work together to share information and align efforts, often under the guidance of a senior manager or convergence evangelist. The technical phase is where the actual convergence architecture -- including IoT and other parts of the infrastructure -- are designed and developed. This usually includes management and security issues and involves some amount of proof-of-principle validation. The operational phase involves deploying and operating the converged environment, which includes regular reporting, as well as infrastructure refreshes and updates as technologies evolve.
With a set of overarching guidelines in place, a business can focus on more practical aspects of IT/OT integration. There are generally three accepted approaches:
- Creating a separate network for IT and OT.
- Partitioning IT and OT networks.
- Fully integrating OT traffic in the IT environment.
Each approach has its challenges and tradeoffs, but IT and OT systems have different requirements that must be addressed. They aren't the same and often can't be treated interchangeably, especially where legacy OT systems are involved. For example, consider the presence of mission-critical OT systems, such as critical safety systems in an industrial process. It might be better to create and maintain a separate network for IT and OT systems than to share a network that could be subject to heavy traffic loads and disruptions. In effect, use the approach that's most appropriate for the business and its regulatory or governance requirements.
Stephen J. Bigelow, senior technology editor at TechTarget, has more than 20 years of technical writing experience in the PC and technology industry.
Ben Lutkevich is the site editor for Software Quality. Previously, he wrote definitions and features for Whatis.com.





