What is a UUID (Universally Unique Identifier)?
A UUID (Universal Unique Identifier) is a 128-bit value used to uniquely identify an object or entity on the internet. Depending on the specific mechanisms used, a UUID is either guaranteed to be different or is, at least, extremely likely to be different from any other UUID generated until A.D. 3400.
UUIDs can be generated to refer to almost anything imaginable. For example, they can identify databases, system instances, primary keys, Bluetooth profiles or objects with short lifetimes.
UUID is an analogous term to GUID, or Global Unique Identifier. Originally, GUID referred to a variant of UUID used by Microsoft, but the terms became synonymous in the Internet Engineering Task Force (IETF) Request for Comments (RFC) 4122 specification. UUID was standardized by the Open Software Foundation, becoming a part of the Distributed Computing Environment (DCE). Different versions of UUID follow the more recent RFC 9562 specifications.
UUIDs are generated using an algorithm based on a timestamp and other factors, such as the network address. Free tools to generate UUIDs include UUID Tools or the Online UUID Generator.
How does a UUID work?
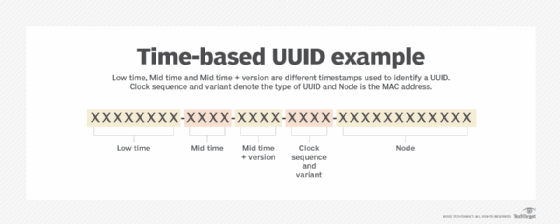
The UUID relies on a combination of components to ensure uniqueness. UUIDs are constructed in a sequence of digits equal to 128 bits. The ID is in hexadecimal digits, meaning it uses the numbers 0 through 9 and letters A through F. The hexadecimal digits are grouped as 32 hexadecimal characters with four hyphens: XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX. The number of characters per hyphen is 8-4-4-4-12. The last section of four, or the N position, indicates the format and encoding in one to three bits. Within this format, UUIDs can be generated independently across systems with no need for coordination or management.
For example, UUIDs based on time have segments divided by hyphens that signify low, mid and mid time and version, which are different timestamps used to identify the UUID. The digits under the last section, the node, denote the Media Access Control (MAC) address.
There are three variants of UUIDs:
- Variant 0. This variant is reserved for backward compatibility with the obsolete Apollo Network Computing System from the late 1980s. It is similar in construction to the version 1 UUIDs used today.
- Variant 1. Variant 1 is the main variant used today. These variants are referred to as RFC 4122/DCE 1.1 UUIDs, or Leach-Salz UUIDs after the authors of the IETF working document defining UUID specifications. As an example, GUIDs are variant 1 UUIDs.
- Variant 2. Variant 2 is reserved for Microsoft backward compatibility. Even though many of the GUIDs Microsoft uses are variant 1 UUIDs, early GUIDs on the Windows platform used variant 2. The difference between variants 1 and 2 is the number of bits in the N position. Variant 1 UUIDs use two bits, while variant 2 UUIDs use three bits.
UUID vs. GUID
UUID and GUID are two representations of a single concept, differing only slightly in their origins and common usage. The following is a comparison:
- UUID is a unique identifier defined by the IETF standard, whereas GUID is a unique identifier defined by Microsoft.
- UUID was introduced as part of the Open Software Foundation standard. GUID began as a component in Microsoft's Component Object Model.
- UUID is cross-platform and can run on Linux, whereas GUID is Microsoft-specific and is used within the Windows Registry and .NET framework.
- UUID supports a range of versions. GUID in a .NET context uses UUIDv4.
UUID and GUID identifiers are identical in structure; both are displayed in hexadecimal and hyphenated. GUID identifiers align with the UUID standard RFC 9562. In most practical scenarios, the two are interchangeable.
UUID versions
The current variant of UUID, variant 1, consists of five different versions. These versions differ in how they are constructed. Types of UUIDs include the following:
- Version 1. This version is generated from a specified time and node. It is a timestamp-based unique host identifier.
- Version 2. This version is generated similarly to version 1; however, less significant bits are replaced. Namely, eight bits of the clock sequence are replaced by a local domain number, and 32 bits of the timestamp are replaced with the number for the specified local domain. These are reserved for DCE Security UUIDs.
- Version 3. This version is generated by hashing both a namespace identifier and a name. Versions 3 and 5 are constructed similarly; however, version 3 uses the message-digest algorithm 5 (MD5) as the hashing algorithm.
- Version 4. This version of UUID is generated randomly. Although the random UUID uses random bytes, four bits are used to indicate version 4, while two to three bits are used to indicate the variant. These can be created using a random or pseudo-random number generator. More bits are used in this version, so there are fewer UUID combinations. However, there are still enough UUID combinations to avoid the possibility of a collision.
- Version 5. Version 5 is generated the same way as version 3. However, it is generated using Secure Hash Algorithm 1, or SHA-1, as opposed to MD5, which version 3 uses for hashing. Versions 3 and 5 are well-suited for use as unique identifiers for information and data within a namespace of a system.
- Version 6 and 7. These newer UUID versions are designed for sorting databases and address the limitations of earlier versions.
- Version 8. This UUID format is custom and enables applications to embed specific data into the UUID.
An extra version of UUID, and a special case, is the Nil UUID. This UUID contains all zeros for integers.
UUID collisions
A collision occurs when the same UUID is generated more than once and is assigned to different objects. Even though it is possible, the 128-bit value is extremely unlikely to be repeated by any other UUID. The possibility is close enough to zero, for all practical purposes, that it is negligible. Even in version 4 UUIDs, where there are fewer UUID combinations, the chance of a collision is low enough to be ignored.
It's so low, in fact, that it's entertaining to ponder: About 2.71 quintillion (2.71 x 10^18) UUIDv4s would need to be generated before the probability of a collision rose to 50%.
UUID use cases
The UUID identifier has a broad range of common applications in wide usage. These include the following:
- Primary keys in databases. UUIDs guarantee the uniqueness of identifying keys across distributed systems.
- Object storage. Files and binary large objects are often named using a UUID to ensure filename uniqueness.
- Application programming interfaces (APIs). UUIDs are frequently used in RESTful API URLs for resources.
- Internet of things (IoT) devices. UUIDs are often used to uniquely identify IoT devices, sensors and nodes.
- Sessions and tokens. UUIDs are commonly found in session IDs and authentication tokens.
- Blockchain. UUIDs facilitate unique transaction IDs and block references in blockchain systems.
Sometimes, using a UUID is not a good idea; for instance, in a system where IDs must be strictly sequential or when indexing overhead might be a problem, as in relational databases.
How to generate a UUID
UUIDs are so ubiquitous that it comes as no surprise that there are many ways to generate them. Doing so is a straightforward process, facilitated by built-in libraries in all the most commonly used programming languages. The following steps are generally the same across languages:
- Declare the library that facilitates UUID creation; this could be an import statement or equivalent.
- Invoke the library code that generates the UUID.
- Declare a variable in the program to store the generated UUID; for example, this could be uuid or uuidv4.
The library references are as follows:
- In Python, import uuid.
- In Linux, with the command line uuidgen.
- In Java, import java.util.UUID.
- In Javascript, const { v4: uuidv4 } = require('uuid').
- In C#, Guid guid = Guid.NewGuid();
Apple devices also have a unique device identifier known as the UDID, which is mainly used to associate a device with a specific Apple account. Learn how a UDID works and the benefits it provides Apple devices.







