Getty Images/iStockphoto
Where do business continuity plans fit in a ransomware attack?
Recovery isn't the only priority when ransomware hits. Careful planning, training and coordination among IT teams are critical to maintain business continuity during an attack.
Ransomware attack recovery is a critical activity that IT cybersecurity teams typically address. Business continuity cannot be a footnote in this process. Ransomware attacks can disrupt operations, but if an organization uses and stores sensitive information, it must also be prepared to maintain business continuity if that information is compromised.
In a ransomware attack, multiple emergency plans can come into play. Assuming IT teams launch the ransomware response plan quickly, and cyberthreat technology does its job, it might not be necessary to activate other plans.
However, in situations where the ransomware attack is more serious than initially determined, it is critical to know when to activate additional business continuity and disaster recovery (BCDR) plans. This will help ensure the technology infrastructure, critical systems and data, and business operations are secure.
Where BCDR fits in a ransomware plan
An organization's cybersecurity plan should be the first barrier to ransomware attackers. This plan typically activates once firewalls have detected an anomaly using intrusion detection and prevention systems as well as other threat detection systems. If the nature of the attack quickly escalates and begins threatening critical systems, such as blocking access to critical files, it might be necessary to activate BCDR plans.
A unique business continuity plan for ransomware is not always necessary, especially if existing BCDR, cybersecurity and ransomware action plans are in place. Business continuity plans should ideally include references to cybersecurity plans if a ransomware event occurs.
The cybersecurity plan should refer to disaster recovery processes if and when an attack has affected technology operations and to business continuity activities for resumption of business operations following an event.
Streamline ransomware plans for better response
One challenge organizations must address in advance of an attack is the role of IT personnel. Cybersecurity teams are responsible for attack response, but will they hand off event management to a BCDR team when the attack escalates? This is where careful advance planning is essential, as well as training of all teams and periodic plan exercising.
Another dilemma is how many plans the organization needs in a ransomware attack. If there are too many plans in play, it can result in confusion as to which plan to use or plans being overlooked by IT teams in an actual event.
The natural tendency is to have specific plans for different situations. While this certainly makes sense -- and is also important from an audit perspective -- it could be a problem without enough planning, training, exercising and management support.
Launching business continuity plans in a ransomware attack
A cybersecurity plan or ransomware plan is the first point of response. The plan should include its own incident response steps, such as anomaly detection, analysis and mitigation. It should also identify what steps to take if the attack escalates and begins to threaten the organization's technology infrastructure and business operations.
The chart below presents a flow diagram with a suggested set of steps for addressing a ransomware attack and when IT teams can activate business continuity or disaster recovery plans.
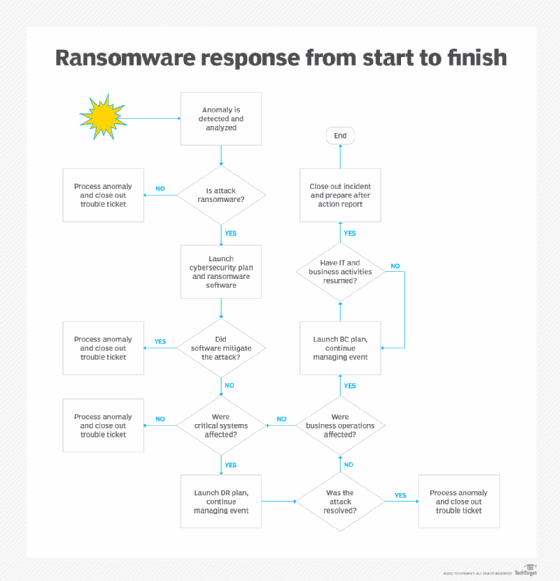
At various stages of the process, IT teams assess the status of the attack and its effects on technology and business operations. When the attack is finally mitigated, teams usually complete a closeout process and an after-action report.
The attack's effect on technology precedes its effect on business operations in the diagram above, but that is not always the case. In some situations, the attack might be so severe and progress so rapidly that it can concurrently disrupt or compromise technology and business processes.
In these cases, launch both business continuity and disaster recovery plans as quickly as possible to minimize damage. As the plans progress and associated teams perform their roles, at some point the incident is resolved. An after-action report is essential to analyze what might have gone wrong and prepare for similar situations in the future.