
ag visuell - Fotolia
4 Docker security best practices to minimize container risks
Without the right tools and processes in place, Docker security can feel like a moving target. Use these four practices -- related to container images, hosts and more -- to keep deployments safe.
When it comes to container security, there are two key areas IT admins should emphasize: the container image and host. You can't, after all, secure one without the other.
At the end of the day, virtualized containers still run on a host system. A privilege escalation bug could compromise the security of the entire host and lead to loss of confidentiality, integrity and availability.
The good news is that IT admins can use freely available tools -- combined with a coherent build and test process -- to mitigate risks. To get started, embrace these four Docker security best practices.
Keep software up to date
The first and most basic step toward a secure container deployment is to ensure the container host runs the most up-to-date programs. To do this with Ubuntu, issue the following command via an SSH session:
sudo apt update sudo apt upgrade -y sudo reboot
In addition, use the latest version of Docker. The versions that tend to ship with Docker distributions are usually woefully out of date compared to those shipped by Docker itself. To install the latest Docker edition in Ubuntu, add the Docker repository key, add the repository, and install Docker, as shown below:
sudo apt-get install \
apt-transport-https \
ca-certificates \
curl \
gnupg-agent \
software-properties-common -y
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
sudo add-apt-repository \
"deb [arch=amd64] https://download.docker.com/linux/ubuntu \
$(lsb_release -cs) stable"
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io -y
Another important step is to use a key-based login, rather than a standard password. This dramatically reduces the chance of an account compromise.
Use trusted container images
One of the most trivial, but critical, Docker security best practices is to ensure the integrity of container images. Always confirm that publicly available images come from non-malicious and security-aware sources.
If you can't trust a container image, don't run it -- especially not in production. Even with auditing, nothing is set in stone. Restrict usage to officially signed container images. To view official Docker Hub container images in a web browser, visit here.
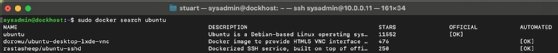
To ensure you get the official image, perform a Docker search -- using the docker search command -- before pulling the image in Docker Hub. For example, to find the official docker image for Ubuntu, use the command docker search ubuntu. This will show all the images that meet that criteria. If the official column has [OK] listed under it, as shown in Figure 2, it's the official image.
Another Docker security best practice is to enable Docker Content Trust to use and verify digital signing. Signed images do two things. First, they ensure image users get what they expect. Second, they confirm image integrity.
To experiment with Docker Content Trust, use the following command.
export DOCKER_CONTENT_TRUST=1
Implement scanning tools
IT admins can also use several scanning tools to check Docker images for vulnerabilities.
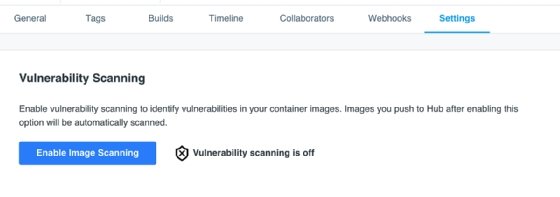
Those with a Docker Hub account can use the scanning functionality within the repository. Turn on the scanning capability in the Settings menu, as shown in Figure 3. This will automatically scan every uploaded image, and offer a report on the scan shortly after.
To enable scanning functionality locally via the command line, use the docker scan command. This native feature relies on Synk.io to provide back-end scanning.
Both docker scan and the Docker Hub repository scan highlight common vulnerabilities and issues. However, scanning through Docker Hub requires a Pro or Teams Docker account.
Manage container resources and hosts
A core part of the CIA security triad -- and another important Docker security best practice -- is to ensure resource availability. As such, IT admins should manage the amount of resources that containers can consume.
Use built-in controls in the Linux subsystem to configure resource limitations. For example, to restrict CPU usage, run:
docker run -it --cpus=".5" ubuntu /bin/bash
The above command will allow one container to consume a maximum of 50% of a single CPU. Similarly, limit the amount of memory a host consumes using the –memory switch.
For effective host management, don't use the default docker0 bridge network. Use of the bridge network in its default state grants all VMs access to the same virtual network. One compromised container can listen to all network traffic; to reduce exposure, restrict traffic to smaller networks. Encrypt all traffic at the application level, and make sure web hosts are not on the same network as application servers.
There are several discrete areas to consider regarding a container host. Consistency is key if the administrator wants to spool up hosts on demand. Run Docker Bench for Security -- a scanning and reporting tool -- against the default host image to identify potential optimizations.
To install a copy locally, clone the Docker Bench system:
git clone https://github.com/docker/docker-bench-security.git
To run the Bench security tool, use:
sudo ./docker-bench-security.sh
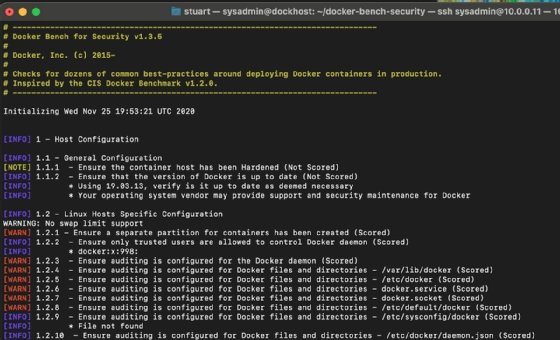
Remember that every remediation item in the Docker Bench output is not mandatory; they are suggestions. Each installation will vary, so take time to understand fully what the tool recommends.
Roll any optimizations into the default image for when hosts need to be spun up in the future. Also, always keep the Docker Bench installation up to date. To simplify updates, consider using a local copy of the script rather than a Docker instance.






