
jro-grafik - Fotolia
Best practices to maintain VPN security
Enterprises looking to maintain VPN security should focus on proper endpoint security and authentication, VPN server security and documentation for security policies.
A virtual private network permits users to create a secure connection to another network over the internet. The VPN concept typically connects an endpoint running VPN client software to a VPN server connected to the secure network.
For enterprises, VPNs initially became popular to provide users with secure access to corporate resources while they traveled or occasionally worked from home. For most enterprises, only a small percentage of a typical workforce traveled or worked remotely at any one time, so these implementations didn't have the capacity to handle the changes spurred by the COVID-19 pandemic. As a result, during the crisis, many firms bypassed normal channels and best practices and stood up less secure systems, such as implementing direct VPN access to Linux or Windows servers or using consumer-grade equipment to cover the load.
VPN endpoint security, authentication and authorization
VPNs focus on enabling connectivity, and the original concept didn't offer endpoint security or user authentication. As long as the end-to-end tunnel negotiation is set up correctly, the connection will be established. While this may be sufficient for individual users, most corporations demand that devices meet the same level of requirements normally seen in on-site environments. They also require the authentication of users on those devices.
Endpoint protection platforms and endpoint detection and response systems come into play for this level of access. These systems shield user devices from malware and viruses and can even ensure that systems connecting to the enterprise meet minimum software update standards. This is especially important for users that work from home or other unsecure locations for extended periods.
Most of the major next-generation firewall (NGFW) systems and security platforms integrate the VPN server function with this type of access control and can even ensure multifactor authentication (MFA) is used for client authentication and access.
VPN server security
VPN services can be supported on Windows and Linux platforms, but this is not recommended in most corporate environments. The typical systems administrator isn't equipped to deal with the onslaught of security issues associated with directly exposing servers to the outside world. However, teams that have this setup should take care to restrict use to the VPN function and restrict access to server management.
For better security, most of the major NGFW vendors and even some of the newer software-defined WAN and Secure Access Service Edge offerings support enterprise-grade VPN services. With these types of systems, the VPN server function is embedded in a hardened security device or system.
Implement and document VPN security policy
It is difficult for enterprises to make consistent access and security policies when they have a hodgepodge of systems. A good place to start is to consolidate the VPN systems to a common standard. Once consolidated, it's much easier to define and implement policies.
More sophisticated NGFW systems enable user profiles to be associated with Security Group Tags (SGTs), which provide unique labels that describe which privileges the user is permitted within the network. The SGT nomenclature is from Cisco, but this level of abstraction is possible across many technology vendors and can even work in a multivendor approach using Cisco's Platform Exchange Grid, which is now an Internet Engineering Task Force standard, RFC 8600. This concept is important because policies can be applied to groups and users can be assigned to groups, permitting an extra layer of policy controls.
VPN security challenges
When following the best practices to secure a VPN, it's important to also understand the associated challenges.
Split tunneling. Split tunneling is the capability of a remote router or endpoint to connect to more than one network service. In practical terms, split tunneling typically involves direct internet access for some services and connecting via a VPN tunnel for other enterprise traffic. A common approach is to enable direct offloading for SaaS applications, such as Microsoft 365, but require VPN tunneling for all other traffic.
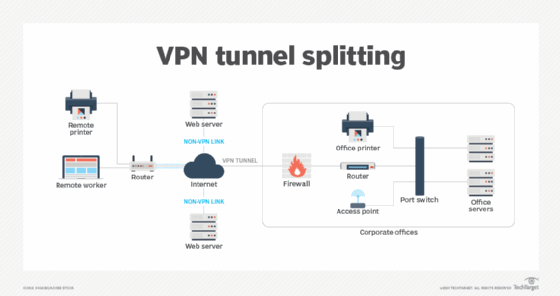
While split tunneling is popular, it does come with drawbacks. SaaS access is direct, which improves performance, but this can also be a vector for attacks and data exfiltration. Security planners should also be aware that in some highly regulated environments -- such as those subject to U.S. Department of Defense standards -- split tunneling is prohibited.
Timeouts. Enterprises must also take care to ensure idle sessions time out -- but this must be balanced with UX. Typical security recommendations to initiate VPN timeouts range from 10 to 30 minutes. When enterprises have control over the endpoints, it's also crucial to require a screen lock after some interval of inactivity, such as 10 minutes.
Timeouts can also include a connection or authentication timeout. With MFA, enterprises should increase the length of these timeouts to permit the user enough time to provide the additional information. Typical ranges are from 60 to 90 seconds.








