
Sergey Nivens - Fotolia
How to use two VPN connections at the same time
Network managers and users might opt to set up two VPN connections at the same time, from the same remote device. But that might not be possible -- or safe.
VPNs are among the most popular ways to gain remote access to IT resources.
Many enterprises now have employees that work both in the office and remotely. Most will likely continue to use remote access for business information systems and services, which means network managers must think about how to balance the optimization of resources available to remote users and in-office employees.
This article examines the pros and cons of setting up two VPN connections at the same time from one remote device. It explores scenarios where multiple VPN sessions provide value to individual users, as well as the risks associated with expanded remote access. Finally, it discusses the advantages and disadvantages of using multiple VPNs.
Can two VPNs be used at once?
Consider the following scenario: A remote laptop normally connects to host-based systems via a VPN that uses the internet as the transmission medium. The VPN -- whether initiated by a physical appliance or software application -- provides access control, security and other mechanisms for a secure connection.
Now, suppose the remote user wants to connect to another resource offered by the company. Can that user connect via the same VPN tunnel? In most cases, the answer is no because the VPN software generally supports only one connection at a time.
Installing a second instance of VPN software and an additional network interface card probably won't work, as the VPN clients may overlap and interfere with each other. The image below depicts how that might work in practice.
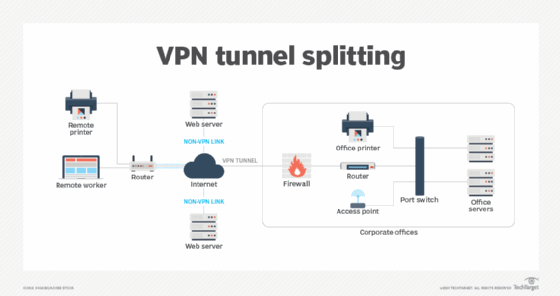
Remote workers normally use a VPN tunnel to access their primary work systems and resources. However, if they need to access additional web-based services, they must use a non-VPN connection to the remote host.
Security and availability are primary drivers for VPN usage. As such, network managers must make arrangements for traffic that uses non-VPN connections to ensure the information being accessed is secure, its confidentiality and integrity are protected, and its availability is assured. One way to ensure this is by using encryption.
It's also possible to configure a single VPN client with a policy that permits the client to reach more than one destination, which is called split tunneling. For example, the VPN policy might say all traffic sent to 192.168.0.0/24 goes over a VPN tunnel to the main office. Other traffic -- with no VPN -- goes over the internet to the remote locations.
How to use multiple VPNs together from one system
It can be more challenging to run multiple simultaneous VPNs than to configure two VPN providers and connect them. While one VPN may appear to be performing properly, the second may display routing errors. This problem is because the two VPNs compete until one VPN wins, which results in only one running VPN. The first VPN establishes various routes with lines of netmasks that take over a default gateway. Once this set of connections has been established for the first VPN, the second VPN will attempt to use the same routes, causing errors.
For example, Microsoft offers a networking utility called rasphone.pbk, which is designed to facilitate multiple VPN sessions from a single device, while retaining the unique settings of each connection. A review of issues associated with using rasphone.pbk showed that the initial VPN set up as desired, but the second lost its authentication parameters and required manual reentry of username and password.
Run VPNs on the primary OS and a VM
One technique for using multiple VPNs together is to run one VPN on the primary OS and install the other VPN on a VM that runs in the device. If more than one OS is available, such as Windows and Linux, consider using Linux for the VM.
Once the VM is launched, install free software, such as OpenVPN, in the VM. This approach can, in effect, create two tunnels. Note that the system's IP address initially routes through the computer and then routes to the VM. This can affect processing speeds as more VPNs are added.
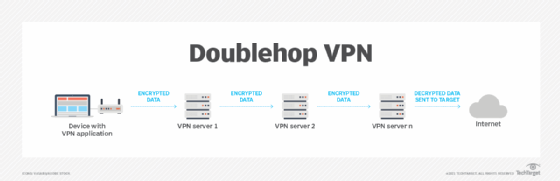
Create a VPN chain -- or double VPN
A double VPN uses multiple VPNs in a chain arrangement by routing through more than one VPN server. This strategy provides greater security for a VPN connection because of the double encryption. This arrangement is also referred to as a double VPN, doublehop VPN or multihop VPN.
It is possible for a double VPN service provider, such as NordVPN, to support multiple VPNs from a single device, with appropriate configuring of the NordVPN Double VPN feature.
Use browser extensions
Another way to set up VPNs is to use browser extensions -- specialized applications that can be accessed via a device browser, such as Microsoft Edge. For example, two VPN applications available for Edge are VPNizer and Ivacy. Check each application to see if it supports multiple VPNs.
Advantages and disadvantages of using multiple VPNs
Reasons to use multiple VPN arrangements include the following:
- greater security for data transmission, especially when using chained VPNs; and
- access to additional resources using multiple VPN tunnels.
Reasons not to use multiple VPN arrangements include the following:
- reduced data connection speeds due to added processing for the different VPNs; and
- added costs associated with the resources needed to create multiple VPNs.
Questions and considerations for planning VPN connections
The following are seven questions network managers should answer when contemplating concurrent VPN connections, such as split tunneling and VPN chaining options:
- Can you program a VPN policy definition that performs what you want to do?
- Are the IP addresses of the two private destinations you want to use nonoverlapping and static? If the remote host has a dynamic address, configuring a policy may be difficult.
- Does the VPN device or application permit split tunneling?
- What arrangements must be made in advance before using split tunneling or the other VPN arrangements noted?
- Does the split tunneling device have a security feature to prevent opening a backdoor in which traffic that goes through the non-VPN connections could enter through the VPN tunnel and enter your machine?
- Does the VPN device permit detailed VPN policy definition and configuration?
- Does the VPN device permit your client-server protocol to accept incoming connections to your laptop?
Planning considerations
If your VPN client doesn't support split tunneling or other multiple tunnel options, you may not be able to access local and international internet services concurrently, you may use up much of the network bandwidth and you may not be able to access LAN-connected devices while on the VPN.
If the VPN device supports split tunneling, verify the following items:
- It can access remote systems, as well as local IP addresses.
- Downloads can be made safely without affecting the throughput for web activity.
- Other local devices, such as a printer, can operate while accessing internet resources.
When using other multiple VPN arrangements as described in this article, be prepared for slower throughput speeds.
Data traffic that doesn't travel over a secure VPN may be accessible by others, such as an ISP or cybersecurity threat actors. When using chained or double VPNs, data security can be enhanced significantly.
Determine the business requirements from remote workers before investigating alternate VPN arrangements. To ensure optimum VPN response times, security and performance, network engineers must carefully analyze the following:
- which resources workers are accessing remotely;
- the kinds of activities -- e.g., sessions -- remote users will be performing;
- available bandwidth; and
- network access and security devices.
Network engineers can use these best practices to generate additional efficiency for remote users who use VPNs to access company information services. Teams must carefully research the necessary requirements before evaluating any specific devices and network configuration changes.






