three-factor authentication (3FA)
What is three-factor authentication (3FA)?
Three-factor authentication (3FA) is the use of identity-confirming credentials from three separate categories of authentication factors -- typically, the knowledge, possession and inherence categories.
This type of multifactor authentication (MFA) improves security over single- or two-factor authentication (2FA), as it's unlikely that an attacker could fake or steal all three elements involved in 3FA. 3FA is useful for organizations that handle sensitive data and require a high level of security for logins.
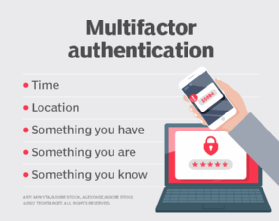
Authentication factors classically fall into the following three categories:
- Knowledge factors -- also referred to as something you know -- include things a user must know in order to log in. These include usernames, IDs, passwords and personal identification numbers (PINs).
- Possession factors -- also referred to as something you have -- include anything a user must have in their possession to log in. This category includes one-time password tokens, key fobs, smartphones with OTP apps, employee ID cards and SIM cards.
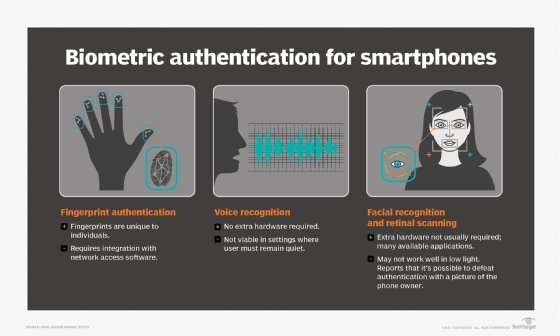
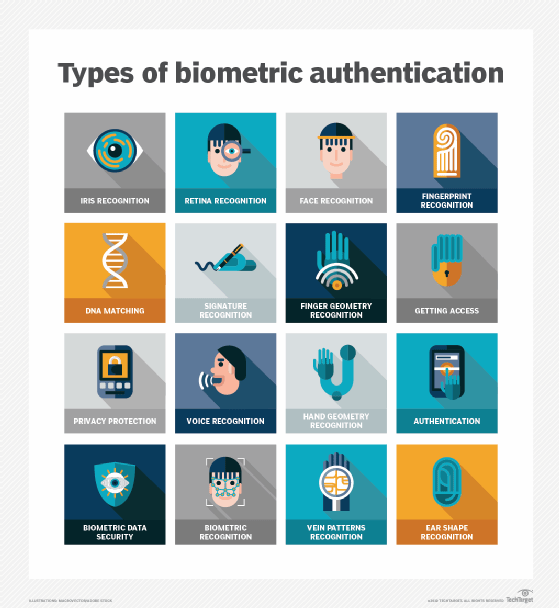
- Inherence factors -- also referred to as something you are -- include any biological traits the user has that are confirmable for log in. This category includes the scope of biometrics, such as retina scans, iris scans, fingerprint scans, facial recognition, voice recognition, hand geometry and even earlobe geometry. For example, biometric data is commonly used in smartphones that use fingerprint scanners or facial recognition.
Three-factor authentication use cases
Three-factor authentication is more secure than 2FA, as it requires users to provide three proofs of identity, as opposed to the two different proofs 2FA requires. The use of at least one element from each category is required for a system to be considered three-factor authentication -- selecting three authentication factors from two categories qualifies only as 2FA.
As such, 3FA is commonly used by businesses that require a high level of security. For example, 3FA may be used by businesses, universities and colleges, government agencies and healthcare organizations for accessing accounts and making transactions.
Using three-factor authentication
The reliability of authentication is affected by the number of factors involved, as well as how they're implemented. In each category, the choices made for authentication rules greatly affect the security of each factor.
Poor or absent password rules, for example, can result in the creation of weak passwords like guest, which defeat the value of a password. Best practices include requiring inherently strong passwords that are updated regularly.
Biometric security systems that use facial recognition could be defeated if an individual holds up a picture of the authorized user. More sophisticated systems might have more secure requirements, such as a depth scan or compelling the user to blink for their retina scan to register. Lax rules and implementations result in weaker security; alternatively, better rules can yield better security per factor.
3FA vs. 2FA
The biggest difference between 2FA and 3FA is that 3FA requires the use of one more distinct security factor than 2FA. This makes 3FA a more secure form of MFA.
2FA is used in a number of places, including automated teller machines, where an individual must provide a card (possession factor) and a PIN (knowledge factor) to gain access. 3FA access might require a system login that requires a PIN, OTP and fingerprint scan.
Although 3FA is generally considered more secure, if poorly implemented, a system that uses 2FA could be more secure -- as two stronger, well-implemented factors are more secure than three weak authentication factors. Some 2FA factors, however, are also starting to be treated as a paid-only feature by social media companies.
Additional factors, such as location or time, can also be employed to create four-factor authentication.
Learn more about common authentication factors, such as location and time factors.







