Cisco Meraki MX appliances: UTM product overview
Expert Ed Tittel examines Cisco's Meraki MX UTM Appliances, a series of UTM products that combines various network security and protection features into a single device.
Cisco is the largest provider of network infrastructure products and services, catering to small and medium-sized businesses, as well as the largest of enterprises. Cisco's ISA500 series of integrated UTM products for small businesses reached its end of life in 2013, and is no longer sold. The company's current unified threat management offerings are Cisco Meraki security appliances, which are cloud-managed devices designed for SMBs, and are integrated with Sourcefire intrusion protection -- or contextual feeds.
Gartner's 2014 Magic Quadrant for Unified Threat Management lists Cisco as a challenger, along with Juniper Networks, to the UTM market leaders -- Fortinet, Check Point, Dell, Sophos and WatchGuard.
Product specs and performance
Six Cisco Meraki MX models are available as of this writing.
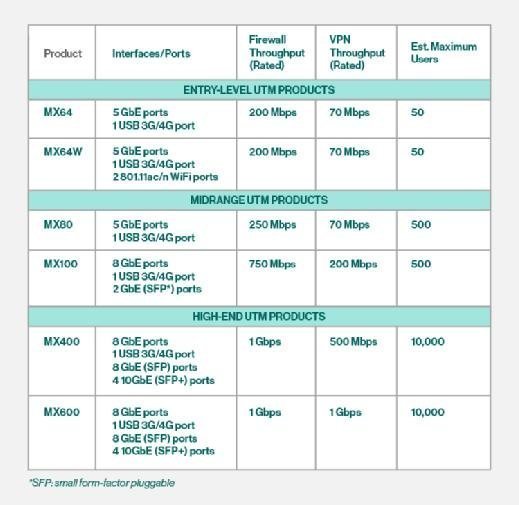
- Cisco recommends the MX64 models for small offices, the MX80 and MX100 for medium-sized offices, the MX400 for larger offices and the MX600 for campus environments.
- Cisco also sells the Meraki Z1 Teleworker Gateway, which includes a firewall, VPN client and 802.11n wireless access point for folks who work from home.
The number and type of interfaces, firewall and VPN throughput rates, and estimated maximum number of users are shown in the following table.
Product features
Cisco Meraki MX appliances include an application firewall, Web search and content filtering, intrusion prevention (SNORT) and Web caching, with integrated Kaspersky antivirus and antiphishing services.
The site-to-site IPSec VPN supports Windows, Mac OS X, iOS and Android clients, but there is no SSL VPN available. Each model also provides identity-based security policies and application management, as well as "intelligent WAN" that has multiple WAN uplinks and 4G failover. The cloud-based centralized management console gives administrators a view of Meraki appliances, wireless access points and switches.
Unlike many competitors, Cisco Meraki MX appliances do not include email scanning or SSL decryption for HTTP.
Cisco lets customers and prospects try Cisco Meraki MX units on their own networks for free. Other testing options include free webinars by Meraki experts, which include live demonstrations, question and answer sessions, and a simulated demonstration of the Cisco Meraki cloud management platform via a Web browser.
Pricing and licensing
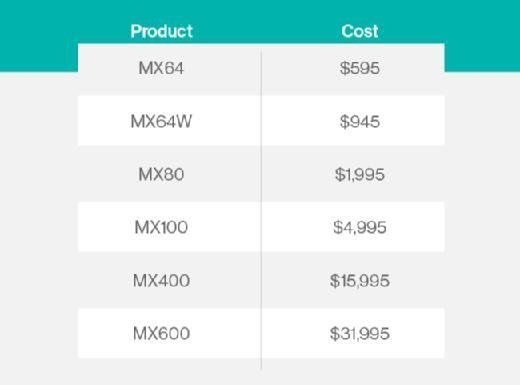
Cisco list prices are shown in the following table.
The Cisco Meraki MX UTM products use cloud-based management, and Cisco requires customers to purchase a license for the cloud on a per-device basis. The licensing tiers are Enterprise Edition and Advanced Security Edition, and each license is limited to a term of one to 10 years, depending on the selected license.
Licensing covers specific features and services used by the appliances; note that the Enterprise Edition license does not cover geography-based firewall rules, intrusion protection, content filtering, antivirus and antiphishing, or Web search filtering.
License prices vary by MX appliance. For example, a one-year Enterprise license lists for $300 for the MX64, and $16,000 for the MX600. An Advanced Security license is $600 and $32,000, respectively.
Support
Cisco provides full online documentation for installing and configuring Meraki security appliances. Enterprise-class support is included in both types of Meraki MX cloud licenses.








