
Getty Images/iStockphoto
Enterprise ransomware preparedness improving but still lacking
An Enterprise Strategy Group survey found enterprises are making strides in ransomware preparedness, but work remains to prevent and mitigate attacks.
The majority of organizations have made ransomware preparedness a top-five business priority, yet only half believe their preparedness is stronger than it was two years ago. That is according to a recent survey, "The Long Road Ahead to Ransomware Preparedness" by Enterprise Strategy Group, a division of TechTarget.
Ransomware is a top priority
Despite warnings and available preparedness resources, ransomware continues to distress companies. Seventy-nine percent of survey respondents said they suffered a successful attack within the last year, and 73% reported they had one or more attacks that caused negative financial impact or disrupted business operations in the same time period.
The good news is the board and the C-suite are finally getting the message that more needs to be done to address impending ransomware attempts. In fact, 79% of respondents said business leaders made ransomware preparedness a top business priority, and 82% of organizations plan to invest more in ransomware preparedness over the next 12 to 18 months.
How are companies handling ransomware preparedness?
With preparedness investments expected to grow, the survey asked how organizations currently tackle ransomware. Respondents said the most important prevention tactics involve efforts in the following:
- network security (43%)
- backup infrastructure security (40%)
- endpoint security (39%)
- email security (36%)
- data encryption (36%)
Ongoing activities cited included data recovery testing, employee security awareness training, response readiness assessments, incident response functional exercises, penetration testing, incident planning and playbook development, phishing simulation programs, tabletop exercises, and blue/red/purple team engagements.
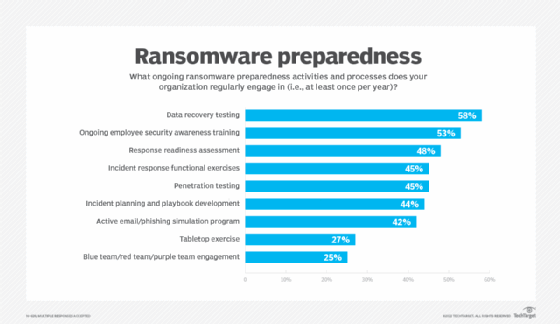
How unprepared are companies?
Companies said they are improving their fight against ransomware, but it's clear that more work needs to be done. Ransomware preparedness gaps exist, and few organizations have solid mitigation strategies in place. Among activities that need more attention are the following:
- Vulnerability management. Only 47% of respondents said their organizations can remediate issues within 30 days of discovering them. The rest report gaps in their vulnerability management programs.
- Incident response communication. Only 53% of organizations reported having a well-thought-out incident response communication plan in place.
- Backup security. Forty-three percent of respondents said they felt very concerned about their backups suffering infection or corruption following a ransomware attack, and an additional 44% said they were somewhat concerned. Less than half (49%) said their organization takes extra measures to protect all backup copies.
The report also looked at the most common points of entry for organizations that experienced an attack within the past year. The top three initial vectors are the following:
- application vulnerabilities
- systems software vulnerabilities
- app user permissions or misconfigurations
"Because it's talked about so frequently, we think about the initial entry point coming from some phishing exercise," said Dave Gruber, analyst at Enterprise Strategy Group (ESG), in an interview. "But the data showed the most common entry points for ransomware weren't email threat factors, but rather software configuration vulnerabilities." Phishing was fifth on the list.
ESG ransomware preparedness recommendations
ESG analysts offered four key ransomware preparedness best practices in the report:
- Embrace teamwork. Ensure all employees understand how the company handles ransomware preparedness and what they should do if a potential attack is detected.
- Improve vulnerability management programs. Be able to address any discovered weaknesses quickly and efficiently. Gruber called vulnerability management the "antidote to protect against ransomware attacks."
- Protect backups better. Backup protection needs to be addressed and improved. Using immutable backups -- which cannot be changed once written -- is one option, Gruber said. Air-gapping backups is a second. A third option is backing up to tape. "Our research showed that tape is not dead," Gruber said. And the best organizations, he added, use a combination of immutable backups, air gapping and tape to help ransomware recovery efforts.
- Protect infrastructure data. Ensure infrastructure configuration data is secured against attack. While protecting business-critical data from attack is a no-brainer, remember that system configuration data is also at risk during a ransomware attack.








