How to use Azure AD Connect synchronization for hybrid IAM
Organizations face many challenges authenticating and authorizing users in hybrid infrastructures. One way to handle hybrid IAM is with Microsoft Azure AD Connect for synchronization.
The Microsoft Cybersecurity Architect certification requires candidates have a wide range of enterprise security knowledge, including how to use Microsoft products for identity and access management.
As more organizations migrate to the cloud, IAM becomes more complicated than ever. Users are accessing resources both on premises and in the cloud, creating numerous security headaches.
In Microsoft Cybersecurity Architect Exam Ref SC-100, author Dwayne Natwick explains how organizations can use Azure and Azure Active Directory (AD) for user authentication and authorization. One key aspect is using Azure AD Connect for synchronization in organizations with hybrid infrastructures.
In the following excerpt from Chapter 4 of the book, Natwick explains how Azure AD Connect works and the three options for using Azure AD Connect for synchronization: password hash synchronization, pass-through synchronization and federation with AD Federation Services synchronization.
Download a PDF of Chapter 4 for more on how to use Microsoft products for IAM.
For Microsoft Cybersecurity Architect exam candidates, check out an interview with Natwick on how to prepare for the exam. Try out this practice SC-100 exam quiz to test your knowledge.
Recommending an authentication and authorization strategy
In current organizational infrastructures, authentication and authorization to resources are not limited to cloud-only users. Many companies have applications that are still in on-premises data centers that users require access to. This provides additional challenges to enforcing the modern authentication techniques for Zero Trust. When using Azure AD for authentication and authorization to cloud resources, you should also determine the proper techniques for users to access on-premises resources. Azure AD Connect provides this capability for SSO to cloud and on-premises resources, but you need to determine the best method for your company to synchronize and manage these hybrid users.
Hybrid identity infrastructure
The term hybrid identity is meant to signify that the company has users that use on-premises resources, and users that use cloud-native resources. Within this hybrid identity infrastructure, there is going to be an on-premises Windows AD domain controller that is used to manage the on-premises users, and Azure AD, which manages the cloud-native users, both members and guests. This infrastructure coincides with companies that have a hybrid cloud approach. Many companies have Windows AD domain controllers in place today. Azure AD Connect provides a hybrid infrastructure connection to Azure AD.
Azure AD Connect is a software solution that is installed within the on-premises infrastructure and configured to synchronize users and groups to Azure AD. Azure AD Connect simplifies the management of these users and groups by providing ways that an identity and access administrator can manage users in one interface and have the changes updated in near real time.
Since there are structural differences in how Active Directory Domain Services (AD DS) and Azure AD are built, Azure AD Connect provides the means to create a consistent user and administrator experience for identity and access management.
There are some prerequisites and aspects that are out of scope within Azure AD Connect that you should understand. The installation prerequisites can be found at this link: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-install-prerequisites. When planning to implement Azure AD Connect, the following information should be understood and planned accordingly:
- Azure AD Connect synchronizes users and groups, not devices or applications. There are ways to co-manage devices and support on-premises application access within Azure AD. Both of these will be covered in later chapters.
- Azure AD Connect synchronizes a single AD DS forest per Azure AD tenant. If there are multiple forests, then multiple tenants will be required in Azure AD.
There are additional considerations in planning for AD DS and Azure AD synchronization with Azure AD Connect, but these will be covered within the use cases for each synchronization type.
There are three options when configuring Azure AD Connect for synchronization:
- Password hash synchronization (PHS)
- Pass-through synchronization
- Federation with Active Directory Federated Services (AD FS) synchronization
Each of these options has its own unique uses. The following subsections will detail these uses and options to consider when choosing one to use within your company.
PHS
PHS is the easiest to configure and is the default option within Azure AD Connect's express setup. PHS maintains both the on-premises and cloud identities of users. This takes place by providing on-premises user identities to Azure AD along with an encrypted hash of their passwords. This allows users to sign into on-premises and cloud applications with the same authentication credentials.
PHS is a good option when a company has a single on-premises domain and is moving quickly to a cloud-native infrastructure. PHS is not for companies with complex authentication and password requirements within an on-premises AD.
As previously stated, PHS maintains authentication credentials on-premises and in Azure AD. Therefore, PHS can have users authenticate to cloud applications through Azure AD, while passing authentication responsibilities to on-premises applications to on-premises AD. The benefit here is that if the connection fails in Azure AD Connect between the on-premises AD DS and Azure AD, users are still able to authenticate to their cloud applications and remain partially productive. Figure 4.4 provides a visual diagram of how this workflow is handled:
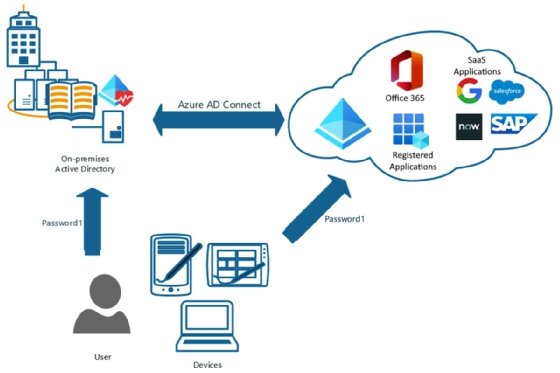
Additional information can be found at this link: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-phs
This configuration for Azure AD Connect is the least complex of the three options and should be preferred for a cloud-native authentication approach. The next sections will provide information about pass-through synchronization and AD FS synchronization.
Pass-through synchronization
The next hybrid identity synchronization option is pass-through synchronization. Unlike PHS, which allows user identities to be authenticated in either the on-premises AD or Azure AD, pass-through synchronization requires all users to authenticate to the on-premises AD.
In this configuration, if the Azure AD Connect connection between Azure AD and on-premises AD were to become disconnected, no users would be able to authenticate to on-premises or cloud resources. Therefore, it is important to actively monitor this connection and build resiliency in the architecture. Figure 4.5 shows a diagram of how pass-through synchronization functions and how you can build resiliency with redundancy in pass-through agents (PTA) and a backup domain controller:
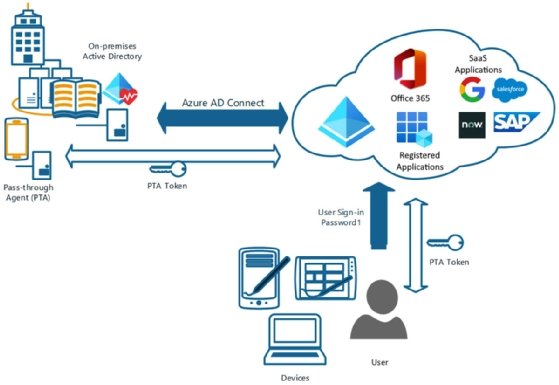
There are some reasons to utilize pass-through synchronization. An organization may require authentication parameters and limits that only allow users to access resources during certain times. Such rules can only be configured currently on an AD domain controller. With pass-through synchronization, you can utilize modern authentication features with Azure AD, such as MFA and self-service password reset (SSPR). However, you will need to enable the password writeback feature within Azure AD Connect to use SSPR. Password writeback will allow the Azure AD password to be written to the on-premises AD. If this is not enabled, the AD password will always take precedence.
In order to have a resilient architecture, it is recommended that at least two of these PTAs are installed on member servers in the on-premises infrastructure. Microsoft's recommendation is that up to four PTAs should be deployed. The next section will discuss the third and final synchronization type within hybrid identity infrastructures, AD FS.
Federation with AD FS synchronization
Federation with AD FS synchronization is the most complex of the three Azure AD Connect synchronization types. AD FS requires additional infrastructure in place to support the authentication process. In comparison, PHS and pass-through authentication can be installed directly on the on-premises domain controller in many cases. Figure 4.6 provides an overview that shows the complexity of the infrastructure and necessary components:
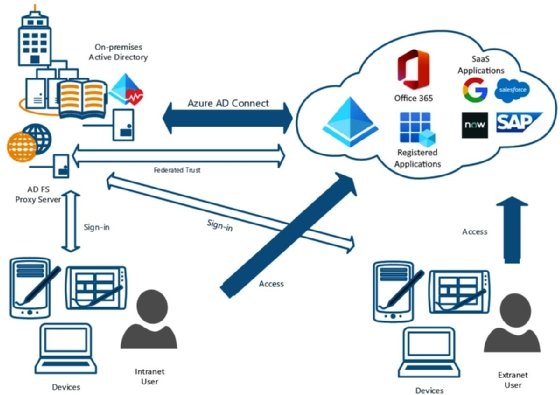
AD FS synchronization is utilized in complex AD infrastructures where there are multiple domains, and third-party MFA solutions or smart cards are utilized. For additional information on the configuration of AD FS synchronization, you can read more here: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-fed-management.
PHS and pass-through synchronization are the more widely discussed of the three Azure AD Connect options. Federation with AD FS is necessary when utilizing third-party solutions that are not native to Microsoft, such as third-party MFA.






