macrovector - Fotolia
Compare the top cloud-based IoT security platforms to protect devices
IoT security tools can protect widely used computing devices that pose cybersecurity risks in the current remote work era. Explore the leading cloud-based options here.
Securing IoT devices has always been a challenge, but with the COVID-19 pandemic forcing enterprise workers out of the office, it has become essential. Many IoT devices are now in widespread use in work-from-home environments with minimal, if any, security protection. While employee laptops possess preprogrammed security against a wide range of threats, IoT devices are much less likely to. Attackers are well aware of the security vulnerabilities that come from widespread work from home, leading to a significant increase in cybersecurity threats. That said, IoT security is more important than ever.
IoT devices can refer to computing devices that use wireless networks to transfer sensor data, or inputs, and/or actuators, or outputs, that interact with the physical world. These connected devices are nonstandard in terms of how users manage and secure them as compared with standard computing devices, like servers, desktops and laptops. IoT devices such as printers and cameras often face the same threats as standard devices but lack the security capabilities that are built into standard devices. This is often due to difficult challenges, such as resource-constrained devices that can't compute strong security mechanisms, like encryption, access control and logging, to simpler yet often not remedied issues, including devices with preset passwords that never get changed and security teams simply not knowing which devices are connecting the corporate systems.
Cloud-based IoT security platforms, like IoT devices themselves, are incredibly varied. Considering the huge variety of IoT devices and device vendors and the lack of standardization in IoT devices, no IoT security tool will be able to support every IoT device. Buyers must ensure any potential cloud-based IoT security service can sufficiently support the organization's IoT devices currently in use.
Comparing cloud-based IoT security platforms
The leading cloud-based IoT security services are difficult to compare because each option has fundamentally different architectures, security levels and pricing structures. The latter is particularly challenging, with some service providers having one set of charges for everything they offer and other service providers having highly granular pricing, like a monthly charge for each IoT device it supports, issued commands and network usage. Charges also can vary based on geographic area.
Amazon Web Services
AWS offers two services that work together to provide IoT security capabilities: AWS IoT Device Management and AWS IoT Device Defender. The IoT Device Management service supports a range of basic device management functions, including registering new devices, as well as performing other asset management functions for IoT devices, resetting devices remotely and installing updates. The service can also establish and enforce access control policies for IoT devices in groups.
The IoT Device Defender service is composed of two features called Audit and Detect. The Audit feature continuously looks for deviations from a set of security best practices and then sends admins a report on a scheduled or ad hoc basis. IoT Device Defender administrators can choose which of the security best practices to include in the audit. The Detect feature performs rudimentary anomaly detection by observing device network activity and generating alerts when the observed activity is anomalous compared to expected activity. The Detect feature provides a basic intrusion detection capability that can find compromised IoT devices that are in misuse within botnets or in other ways that generate unexpected volumes or types of network traffic.
Pricing for AWS IoT Device Management has several components, including the number of registered IoT devices, indexing updates, queries performed, issued commands and established tunnels to individual IoT devices for troubleshooting purposes. Pricing for AWS IoT Device Defender has separate usage charges for the Audit feature and the Detect feature.
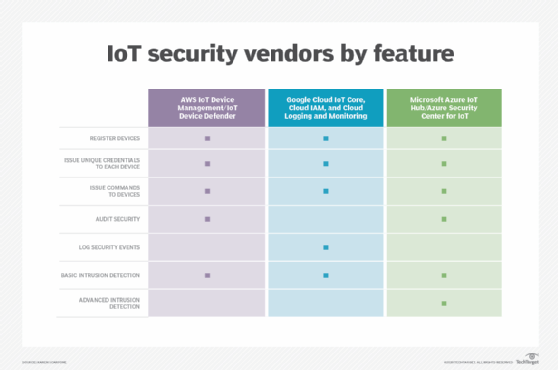
Google Cloud IoT Core provides a variety of IoT device management and security capabilities. Cloud IoT Core can register IoT devices and define metadata for each device that can be used for asset management purposes. Each IoT device can obtain a unique cryptographic key pair with Cloud IoT Core for authentication purposes.
Cloud IoT Core manages IoT devices through what are known as protocol bridges. The protocol bridges speak two of the protocols most widely used by IoT devices: HTTP and Message Queuing Telemetry Transport (MQTT). The bridges act as translators between IoT devices that speak HTTP or MQTT and the device management services Cloud IoT Core provides. Cloud IoT Core can send configuration capabilities, including the ability to issue any instructions or commands, to IoT devices through the bridges. IoT devices can then send information about their state back to Cloud IoT Core.
Google also offers supporting services that aren't limited to IoT devices. Cloud Identity and Access Management (IAM) helps control who can manage groups of IoT devices. Another is Cloud Monitoring, which monitors usage metrics exported by Cloud IoT Core and generates alerts based on the values of these metrics. Its Cloud Logging service offers a range of log management and monitoring services for Cloud IoT Core audit and device logs. However, device logs are not included by default, and there will be charges based on the volume of logs uploaded from devices to Cloud IoT Core.
Pricing for Google Cloud IoT Core is based on the amount of data registered IoT devices send and receive, with some exceptions. Google provides pricing information and a pricing calculator for Cloud IoT Core. There is no additional charge for use of Cloud IAM with Cloud IoT Core, but there are additional charges for the Cloud Logging and Cloud Monitoring services.
Microsoft
Microsoft's Azure Security Center for IoT service relies on the Azure IoT Hub service. IoT Hub provides basic IoT device management services, including device provisioning, support for other asset management features, authentication for each IoT device with device-unique credentials and issuing commands to IoT devices.
Security Center for IoT offers several security services for IoT devices. For example, it can perform continuous security monitoring for IoT devices to audit their security settings and identify potential security problems. It also offers threat protection by using threat intelligence and machine learning to identify and stop potential risks against IoT devices. It also has incident response capabilities for compromised devices. The extent to which an IoT device can support these security services depends on whether it has the Azure Security Center for IoT security agent installed and running on the device. Security Center for IoT won't be able to interact with agentless devices to the degree it can interact with devices with the agent installed.
Pricing for Microsoft Azure IoT Hub is based on a tiered structure, with different monthly charges per IoT Hub instance depending on the tier and edition of each instance. Azure Security Center is priced separately from Azure IoT Hub. It uses a two-tiered model -- Free and Standard -- but only the Standard tier supports IoT devices. Pricing is by IoT device per month and by IoT device transaction.
The benefits of cloud-based IoT security
Cloud-based IoT security platforms can help protect IoT devices from unwanted access or tampering, regardless where users access them from. These services help organizations remotely manage their IoT devices from a single centralized place, with capabilities such as the following:
- asset registration and enrollment;
- asset identity verification;
- vulnerability management and remediation;
- update installation;
- configuration setting changes; and
- remote control actions, including resetting a device, troubleshooting device problems, issuing commands to a device and checking the state of a device.
Some cloud-based services offer additional capabilities for IoT device security, such as the following:
- auditing how well the device's security complies with best practices;
- finding threats through anomaly detection and threat intelligence usage; and
- automating incident response actions, like alert generation and forensic data collection.
Many cloud-based IoT security platforms also offer integration capabilities, like APIs, which developers can use to customize service usage and support for common protocols that provide interoperability with an organization's existing enterprise asset management and security management platforms.








