
SynSaber: Only 41% of ICS vulnerabilities require attention
The industrial cybersecurity vendor analyzed 681 ICS vulnerabilities that were disclosed this year and found many had a low probability of exploitation.
Less than half of the industrial control system common vulnerabilities and exposures reported so far this year need to be prioritized, according to new research by SynSaber.
To help security teams navigate an overwhelming patching process and increased ICS threats, the industrial security vendor took a closer look at the vulnerabilities disclosed this year so far. SynSaber analyzed 681 CVEs included in Cybersecurity and Infrastructure Security Agency (CISA) ICS advisories from the first half of 2022 to determine which CVEs had a lower probability of exploitation, which had any available remediations and which percentage required attention from enterprise security teams.
While SynSaber estimated the volume of reported ICS CVEs will not decrease, it determined that the crop of bugs so far this year is manageable because the majority have an extremely low probability of exploitation.
"Of the CVEs reported thus far in 2022, 41% can and should be prioritized and addressed first (with organization and vendor planning)," SynSaber said in the report.
Typically, CVEs for IT are measured by severity based on attack vectors or security protocols such as authentication and credentials, which are not as relevant for industrial systems. According to SynSaber, ICS and operational technology (OT) environments are unique, and exploitation of vulnerabilities often requires significant human interaction -- and in some cases, a local presence in the target environment.
These differences, SynSaber said, should affect how ICS entities respond to vulnerability alerts compared with traditional enterprises.
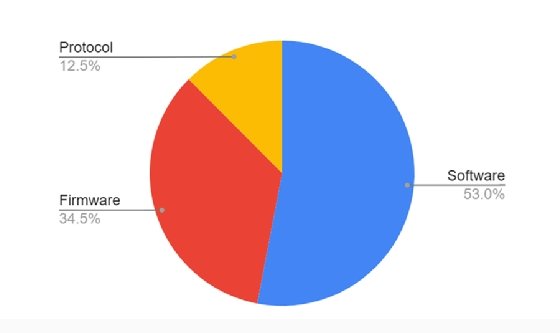
However, SynSaber co-founder and CTO Ron Fabela said advisories and alerts, especially ones that are CISA-amplified, will trigger a lot of responses even when a fix is not possible. According to the research, for the CVEs reported in 2022, 13% had no patch or remediation currently available from the vendor, and 34% required a firmware update.
The research also examined CVEs by Common Vulnerability Scoring System score and found that a majority were ranked high and medium. Only 5% scored a low rating. That can increase the pressure to respond to alerts even though fixes might not be available or necessary.
The main question that inspired the research was, if a vulnerability is identified but has no fix, how should industrial organizations respond?
The question also applies when fixes are available, but require applying patches to thousands of devices interconnected with hundreds of switches that are potentially talking to hundreds of servers and workstations, Fabela said. Sometimes that could require an entire system rebuild, and if advisories are issued but there's no fix other than rebuilding a power plant, for example, then what worth does that alert hold?
"As we see the increase of vulnerabilities reported, we wanted to give asset owners qualifiable metrics -- to say, 'You probably had this feeling anecdotally that these don't really apply to [you], but here's the data to back it up so [you] can have those conversations internally,'" Fabela said. "We don't need to jump every time an advisory is released."
Exploitation is unlikely
The biggest reason that not every alert requires a response is a low probability of exploitation. SynSaber researchers determined that 29% of reported CVEs required user interaction for exploitation to occur. In addition, more than 22% required local or physical access to the system in order to exploit.
"It comes down to this idea that ICS were not secured by design when they were implemented three or four decades ago," Fabela said. "They were serial components, not built to be on an IP network, let alone connected to enterprises and third parties. They did not have built-in security controls like authentication or a lot of things these CVEs still talk about, including hardcoded passwords."
Rather, ICS was designed for efficiency, safety and reliability. Fabela emphasized that there are many advisories related to security protocols that essentially cannot be fixed in ICS environments because of the way those systems were designed. One example was encryption, which ICS designers feared would slow down processes. In addition, fixing flaws can require more complicated communications between asset owners and the original equipment manufacturer (OEM).
Another factor that makes a vast majority -- nearly 70% -- of CVEs unlikely to be exploited is a concept Fabela referred to as "access equals control." For some systems, there are no access controls or protocols preventing unauthorized use, he said. If a threat actor gets onto a network segment and can physically communicate with the programmable logic controller or relay, they can just send a command. The threat actor doesn't need to exploit a vulnerability to obtain control because the system was designed to be broadly accessible.
"It doesn't mean you shouldn't patch," he said, "but there's this weird tension between not wanting to overtly downplay the importance of patching and vulnerabilities while still having a contextual lens."
One example he provided was cross-site scripting, a type of attack young hackers often learn because it doesn't require a high level of sophistication. Fabela said there's no practical application in a control environment, but if someone wanted to send the device a command, they could. This is where having a contextual lens comes into play in recognizing that security teams do not have to prioritize cross-site scripting bugs, which could amount to thousands of fixes.
Another example Fabela provided was a CISA advisory on Inkscape that hit some of the key areas of what's practically exploitable. For one, it required a high level of human interaction. While examining the Inkscape flaw, which was reported by a researcher working with Trend Micro's Zero Day Initiative (ZDI), SynSaber researchers discovered that it affected a little-known plugin for engineers to create animated icons for their screens.
"It's so far removed from operations, and there are so many complicated steps to exploit it," Fabela said. "But if you look at it at face value, CISA put out an advisory, and it's rated 7.8."
OEMs come out on top
While security vendors and researchers, like those with ZDI and Claroty, accounted for 42% of total reported ICS vulnerabilities during the first half of 2022, the majority was generated by OEMs. The largest contributor was Siemens, which disclosed 230 CVEs, according to the research.
While Fabela said that could be interpreted as Siemens having insecure products, it's actually the opposite. He applauded the industrial manufacturing company for its transparency.
"They actually have a really good product security team, and finding their own bugs in house and going that extra step to report this is a huge sign of maturity. No other vendors are really doing that," he said.
Other generators include independent researchers and consultants who find bugs and disclose them to vendors or third-party organizations like ZDI. Fabela said there's an increased interest in industrial flaws, with more people hacking and analyzing ICS and OT, looking for high-profile vulnerabilities.
"There is a significant barrier to entry with bug hunting and research in industrial because sometimes you have to get your hands on the actual software or hardware, which is more difficult than enterprise," he said.
Though this was the inaugural report, Fabela said it is something SynSaber will continue to analyze. For the second half review, he said SynSaber will seek to gain additional insights in order to provide a different view of CVEs to the industrial community.





