
Getty Images
Exchange Server bugs caused years of security turmoil
The four high-profile sets of security vulnerabilities in Microsoft Exchange Server, disclosed by researcher Orange Tsai, are set to remain a major concern for organizations.
Nearly two years after the first series of Microsoft Exchange Server vulnerabilities became known, four collections of high-profile bugs are likely to remain a headache for enterprises for the foreseeable future.
Orange Tsai, a researcher with security vendor Devcore, has taken credit for the discovery and reporting of all four sets of Exchange flaws. Following his most recent disclosure in October, Tsai suggested that he would for now be stepping away from Exchange flaws and declared that "this series has finally come to an end."
That would conclude a campaign that dates back to December 2020 with Tsai's discovery of the notorious ProxyLogon vulnerabilities and has seen administrators and defenders scramble to patch their servers as threat actors primed a potent set of exploits. Though Tsai might be done for now, experts say that for those charged with protecting Exchange servers, the threat won't lift anytime soon.
"I think it will remain a target," Tenable staff research engineer Satnam Narang told TechTarget Editorial. "As long as these systems are accessible online and they are unpatched, it is still going to be a problem."
ProxyLogon makes a splash
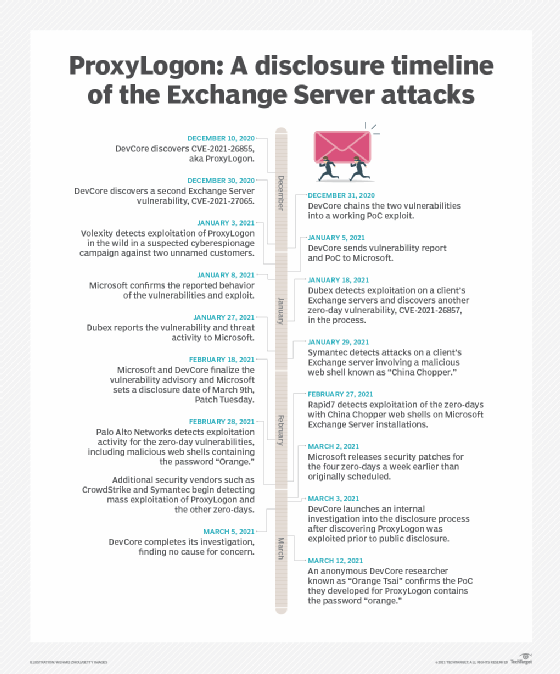
The first set of Microsoft Exchange flaws remains the most well known. The ProxyLogon vulnerabilities included CVE-2021-26855, which is a server-side request forgery flaw that allows an attacker to bypass authentication controls for the ubiquitous Microsoft communications server platform.
While such a bug might not seem like a massive vulnerability in most systems, it is a critical flaw for a server whose sole purpose is to handle email. To make matters worse, Tsai discovered another Exchange flaw in late December that when chained with CVE-2021-26855 could form a remote code execution exploit. Two other related vulnerabilities were discovered by Danish infosec consultancy Dubex and Microsoft's own Threat Intelligence Center.
Tsai later pointed out that the vulnerabilities, as with the other Exchange flaws, are logic errors rather than memory overflow errors, making them easier for attackers to reliably exploit.
Things only got worse when, in March, mass exploitation of ProxyLogon was observed in the wild. It was later revealed that some attacks on the vulnerability had occurred before the bug was even disclosed.
According to Tsai, the research into the ProxyLogon bug also provided the Devcore team with a rather exciting yet concerning discovery about the Exchange platform.
"While looking into ProxyLogon from the architectural level, we found it is not just a vulnerability, but an attack surface that is totally new and no one has ever mentioned before," he wrote in a 2021 blog post. "This attack surface could lead the hackers or security researchers to more vulnerabilities."
The forgotten Proxy
Later in the year, Tsai dropped the second of the Proxy vulnerability sets. Known as ProxyOracle, the bug set is considered to be the lowest risk and is probably the least discussed of the four collections.
The flaw was divided into two separate CVE-listed vulnerabilities that could be chained together and used in a phishing attack in the wild. In a ProxyOracle attack, an unauthorized attacker would potentially be able to access session cookies, eventually resulting in the theft of plaintext user passwords by way of a relatively simple cross-site scripting attack.
Tsai noted that this particular attack was devious because even if the targeted user closed their browser in the middle of the attack process, the attack could still be carried out.
All Shell breaks loose
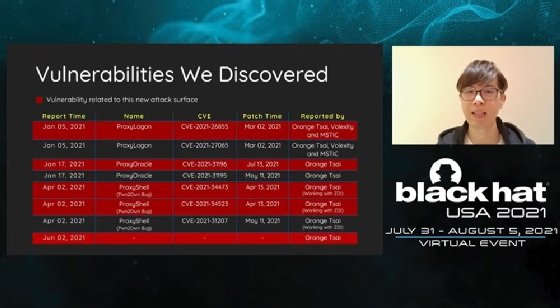
While ProxyLogon and ProxyOracle posed significant risks for enterprises, the situation went to another level in August 2021. During a Black Hat USA conference presentation, Tsai discussed a third set of Exchange flaws known as ProxyShell, which he first shed light on during the Zero Day Initiative's Pwn2Own Vancouver hacking competition in April that year.
Essentially, ProxyShell is a trio of vulnerabilities -- an authentication bypass, elevation of privilege and command execution -- that when chained together would give a remote attacker what amounted to total control over the targeted machine via port 443.
In practice, this meant threat actors were able to create scripts that could be used against vulnerable machines to perform everything from data extraction to ransomware attacks, as well as lateral network movement that could lead to even more damage being done.
And attack they did -- within a month of Tsai's presentation, security vendors reported seeing a spike in active attacks on the ProxyShell flaw. While Tsai did not release a proof-of-concept exploit for ProxyShell, two other researchers used Tsai's work to reproduce and publish a POC during the Black Hat conference.
Though the flaws had been disclosed and patched earlier in the year, many organizations had left their systems vulnerable, likely due to not realizing the threat of the flaws or what could potentially happen should the three vulnerabilities be linked together.
Greg Fitzgerald, chief experience officer and co-founder of Sevco Security, said that given the wide reach Microsoft has across the IT landscape, in many cases companies might not realize how important a single Patch Tuesday issue could potentially be.
"The efficiency is great, but the exposure is massive," Fitzgerald explained. "When they close one hole in Patch Tuesday, the reality is they are interlinked with other tools."
The saga concludes with ProxyRelay
Fast-forward to October 2022 when, with many attackers still successfully exploiting unpatched ProxyLogon and ProxyShell vulnerabilities on Exchange servers, Tsai unleashed a fourth set known as ProxyRelay.
The final of the four bug sets is once again a series of vulnerabilities that can be chained together to not only compromise a single Exchange server, but -- thanks to flaws in the Microsoft NTLM component -- also jump to every other server on the network using those same pilfered account credentials.
In disclosing ProxyRelay, Tsai also lamented Microsoft's slow patching rollout, noting that one of the CVE-listed issues in the ProxyRelay chain sat unpatched for one year before finally being addressed. The researcher did note, however, that Microsoft wanted to address the flaw at the architecture level -- something that would take far longer than issuing a conventional patch.
Because ProxyRelay remains a relatively recent disclosure, there has been little data as to how many attacks have occurred using the bug. If history is any indication, though, threat actors will be eager to put the last of the four Proxy bug sets to use.
The aftermath
Though Tsai has since hung up his proverbial Proxy gloves and promised to move on to new projects, other security researchers have uncovered similar Exchange Server vulnerabilities over the last two years, most recently with the ProxyNotShell flaws. Whether or not new Proxy bugs will be discovered, experts believe that the four sets of flaws -- ProxyLogon and ProxyShell in particular -- will have a long tail.
A major factor for that long tail will likely be just how difficult it can be to apply fixes for Exchange in many use cases.
"With Exchange or VPNs, it is not a simple endeavor to patch these," Narang explained. "It is still a painstaking process."
Perhaps the most disturbing scenario, however, could be when a vulnerability falls into the hands of a long-term attacker.
Fitzgerald pointed out that threat actors focused on cyberespionage or intellectual property theft will often seek to remain dormant but present on a network on a long-term basis. This could lead to a Proxy flaw only coming back to haunt a company years down the line.
"They just want to observe. They want to be present," Fitzgerald warned of certain threat actors. "It does not mean they are taking anything -- they are watching."




