
p0temkin - Fotolia
3 post-SolarWinds supply chain security best practices
Following the devastating SolarWinds breach, IT leaders should renew their focus on third-party risk management. Start by implementing supply chain security best practices.
In 2020, the largest cybersecurity breach in U.S. history began to unfold: the SolarWinds hack. In this supply chain attack, suspected nation-state actors exploited upstream software and credentials of SolarWinds, Microsoft and VMware -- companies that provide downstream services to public and private organizations. Thousands of enterprises worldwide were subsequently breached, as well as U.S. and European governments. All were left scrambling to decontaminate and reconfigure following the disclosure, costing untold losses.
While the effects of the hack are still unfolding, it highlights the necessity for enterprises of all shapes and sizes to assess the security of their own supply chains, and follow best practices to prevent them from falling victim to similar attacks.
Why supply chain attacks are so dangerous
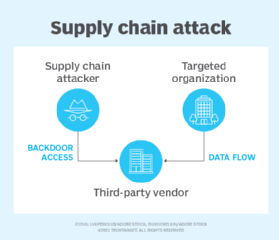
In a supply chain attack, sometimes called a third-party or value-chain attack, a malicious actor accesses an organization's network by infiltrating another part of a company's supply chain ecosystem.
Supply chain attacks are so pernicious because the time taken to detect such an attack is significantly longer than other security incidents. In fact, nine months passed before the SolarWinds breach was first detected.
By embedding malware into third-party services, the threat landscape is widened and more victims -- the customers -- can be exploited. Further, supply chain attacks can penetrate multiple degrees of separation. Thus, security leaders can no longer assume they are safe simply because they are not contracted with the breached company.
Supply chain security best practices in a new enterprise ecosystem
In the age of ecosystem-based business models, tech platforms, app marketplaces, APIs and data sharing are the norm, and supply chain agility is the key to resilience. But cybersecurity strategies have failed to keep pace. The increasingly networked and data-driven nature of the economy requires security leaders to extend beyond enterprise security.
When the organization, business or government is only as strong as its weakest link, it is imperative to develop an ecosystem-wide security strategy. Implementing the following supply chain security best practices can help mitigate third-party risk and meet the needs of the changing enterprise ecosystem.
1. Conduct asset and access inventories
A strong and up-to-date asset inventory is a crucial first step. Record specifications across hardware and software, updates, patches and associated traffic patterns. Obtaining a high level of visibility is a prerequisite to any specific mitigation tactics, especially in today's widening IT/OT, endpoint and remote work landscape.
But supply chain security requires another dimension: Security professionals must also take inventory of access to keep track of participants. Many companies fail to identify -- never mind map -- all vendors or third parties who access their data and assets. This creates major blind spots in security management, threat measurement and participant credentialing. To bolster data security and privacy, organizations must manage access more precisely based on clear, finite and temporary parameters.
2. Elevate third-party risk management
Although it is finally among business and government leaders' top priorities, cybersecurity investments and efforts within the organization itself are not enough. Organizations must extend risk management strategies and tactics across third parties by doing the following:
- Include security policies in vendor contracts. Create a cultural baseline for interorganizational security collaboration and set parameters around data lifecycle management, as well as notification and assessment requirements.
- Require validation of vendors' security posture. Make sure vendors conduct penetration testing, calculate security ratings and adhere to compliance frameworks, such as GDPR or the Cybersecurity Maturity Model Certification.
- Conduct ongoing risk assessments. Incorporate inspections, questionnaires and simulations to test incident response capabilities.
3. Ensure third-party relationships are collaborative
The above supply chain security best practices center on aspects of third-party risk that organizations can control. However, the goal is not to coerce or command third parties.
The best way to address systemic threats is collaboration. Security presents an opportunity for organizations to work together, outside of regular business transactions. Here's how to develop a culture of security-mindedness across the ecosystem:
- Invite mutual risk assessment, where all parties openly participate in proactive risk mitigation, such as penetration testing, credentialing and vulnerability patching.
- Develop communications and best-practice sharing among security analysts. This helps security teams connect the dots when unusual behavior occurs. A benign instance in one area may signal greater urgency around unusual behavior in another or over time.
- Avoid concentrating too many mission-critical services delivered by one vendor. Spread the risk more evenly by incorporating new partner collaborations as part of the strategy.
Because supply chain risk is a systemic problem, it requires systemic approaches to solving it. Multilateral collaboration, coordination and cooperation are crucial to mitigating cybersecurity breaches caused by supply chain attacks.








