supply chain attack
A supply chain attack is a type of cyber attack that targets organizations by focusing on weaker links in an organization's supply chain. The supply chain is the network of all the individuals, organizations, resources, activities and technology involved in the creation and sale of a product. The supply chain encompasses everything from the delivery of materials from the supplier to the manufacturer through to its delivery to the end user. By targeting a weak point in a supply chain, a cyber attack may be more likely to succeed -- with attackers taking advantage of the trust that organizations may have in third-party vendors. Supply chain attacks are a type of island hopping attack.
Supply chain attacks could occur in any industry that has contracts with third-party vendors, such as in financial or government sectors. Supply chain attacks have been rising in relevance due to new types of attacks and the high status of the targets hit. Because weak links in a supply chain are an easier target for cybercriminals, organizations should be more aware of the security implemented within each step of their supply chain.
Cybercriminals will use supply chain attacks to tamper with the manufacturing processes of a company either by hardware or software. Malware could be installed in any stage of the supply chain. This cyber attack can also cause either disruptions or outages of an organization's services.
Supply chain attacks allow for specific targeting, and the number of victims can grow quickly if the attacked vendor has a lot of customers.
Supply chain attacks are difficult to detect, as they rely on software that has already been trusted and can be widely distributed. In addition, there is not one dedicated part of an organization that manages third-party vendors, so if a risk comes to one, it'll get pushed from one team to another.
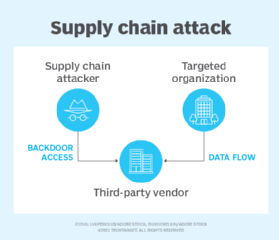
What do supply chain attacks do?
The goal of a supply chain attack is to infiltrate and disrupt a weak point of a system within an organization's supply chain with the intent to cause harm. One typical way of doing this is by attacking a third-party supplier or vendor connected to the actual target. Attacks are typically made on third parties that are considered to have the weakest cybersecurity measures by the attacker. When the weakest point in the supply chain is identified, the hackers can focus on attacking the main target with the supply chain attack.
How do you detect a supply chain attack?
To effectively detect supply chain attacks, an organization should first have a systematic verification process in place for all the possible pathways into a system. An inventory of all the assets and data pathways within a supply chain should be made, which should help in detecting potential security gaps within a system.
The next step would be to create a threat model of the organization's environment. The threat models can include assigning assets to adversary categories. The categories can then be rated, which will help in determining how severe of a threat of an attack could be. These scores should be continually updated. Assets should be classified by most at risk to least at risk.
All new updates should be tested as they come out. Tests to detect supply chain attacks should be able to find malware file activity, registry keys and mutual exclusion (mutex) files. This process should also be done with automated tools.
How do you prevent a supply chain attack?
There are a number of ways to help prevent supply chain attacks. Some of these processes include the following:
- Evaluating the risks of third parties. An organization can ask vendors to perform self-assessments to aid in ensuring that they are secure vendors to support.
- Reducing the number of individuals within an organization that are authorized to install third-party software. This would decrease attack surface
- Including supply chains in response and remediation plans in order to enable a fast response and minimize damage if a cyber attack does occur.
- Reviewing who has access to what sensitive data. Limit access to sensitive data for only those who need it.
- Making sure the organization's data is terminated from the vendor's systems after a contract termination with a vendor.
- Investing in tools provided by security firm Cybersecurity firms can provide automated threat forensics and malware protection against advanced cyber threats.
The U.S. passed the Comprehensive National Cybersecurity Initiative (CNCI) and the Cyberspace Policy Review, which provides federal funding for the development of multipronged approaches for supply chain risk management (SCRM). Likewise, the U.K. Department for Business, Innovation & Skills (BIS) outlined an effort to protect small and medium-sized enterprises (SMEs) from cyber attacks like supply chain attacks.
In addition, one could use the Mitre ATT&CK framework, which provides up-to-date cyber threat information to organizations that want stronger cybersecurity strategies.
Supply chain attack vectors
Supply chain attacks can be either hardware- or software-based attacks -- more specifically, by compromising software building tools, stolen code-sign certificates, specialized code shipped into hardware components or installed malware on a third party's devices.
A supply chain attack may begin with an advanced persistent threat (ATP) that is used to determine the weakest point in an organization's supply chain -- generally, a third-party vendor or application. Once that weak point is discovered -- in a software supply chain attack, for example -- malware in the form of worms, viruses, spyware or a Trojan horse is injected into the system. The malware could be used to modify code sources the third party uses and to then gain access to the target's data.
These cyber attacks could occur at any location in the supply chain.
Supply chain risks
Supply chain attacks can pose a large risk to organizations today. Organizations affected can include financial and government systems, as well as other industries, such as retail, pharmaceutical and information technology (IT) systems.
A large risk that will open an organization up to supply chain attacks is sharing data with third parties, vendors or suppliers. Even though sharing that data in a supply chain may be essential for operation, it also comes with an inherent risk. Likewise, increasing the number of vendors an organization includes in its supply chain increases the number of attack vectors.
Types and examples of supply chain attacks
In 2020, FireEye, one of SolarWinds' 300,000 customers, disclosed it had been breached and itsred team toolswere compromised. SolarWinds later confirmed it was thevictim of a supply chain attackconducted by nation-state hackers. According to SolarWinds, 18,000 of its 33,000 customers were now left vulnerable. In addition, it affected various U.S. government agencies.
The attack involved the insertion of a backdoor by nation-state threat actors into updates for SolarWinds' Orion product that was then distributed to customers worldwide, leading to the massive amount of customer data becoming vulnerable.
SolarWinds took immediate steps to address the attack, issuing a cybersecurity advisory and urging customers to upgrade to the latest version, while releasing a new hotfix to mitigate the backdoor. However, issues still flowed in the vendor's response. On Dec. 24, 2020, another backdoor was discovered. Several media outlets have reported that APT29, a Russian state-sponsored hacking group also known as Cozy Bear, was behind the SolarWinds campaign.
In 2013, the U.S. retailer Target was struck with a large supply chain attack. About 40 million credit and debit card numbers of Target customers became open to fraud once malware was introduced into its point-of-sale (PoS) system. This happened in more than 1,800 stores. Even though a new cybersecurity system was installed prior to the attacks, the cybercriminals were still able to work around it. Although not confirmed, it is suspected that cybercriminals infiltrated a third-party supplier of heating, ventilation and air conditioning (HVAC) systems, using passcode credentials stolen from the provider.
Another example of a supply chain attack is NotPetya from 2017. The malware made its appearance in Ukraine as a backdoor in a tax accounting software. The attack grew to target other countries, including some in North America, Europe, Asia and the Middle East. It targeted government, telecom companies and consulting organizations.






