
jro-grafik - Fotolia
How supply chain security has evolved over two decades
Both physical and cyber supply chain security are critically important. Expert Ernie Hayden outlines the recent history of supply chain defenses and what enterprises need to know.
In October 2018, the terms supply chain security and cyber supply chain security were key subjects of many news headlines.
Bloomberg Businessweek reported that an investigation of some motherboards found in widely used servers had been infiltrated with a chip -- the size of a grain of rice -- that was not included in the original circuit board design. The alleged infiltration appeared to be done by Chinese military operatives and allowed for remote monitoring and control of the boards and their associated servers [Editor's note: the Bloomberg Businessweek article has since come under intense scrutiny from infosec experts and journalists].
Later in October 2018, the U.S. Federal Energy Regulatory Commission (FERC) officially approved a new standard for the North American electric energy industry. The critical infrastructure protection standard, referred to as "CIP-013-1 -- Cyber Security -- Supply Chain Risk Management," was issued to address "... cyber security risks to the reliable operation of the Bulk Electric System (BES) by implementing security controls for supply chain risk management of BES Cyber Systems."
The concept of supply chain security is not new. While it surfaced around the time of the Sept. 11 terrorist attacks in 2001, the cyber aspects are just recently getting attention.
The history of supply chain rules and guidelines
Prior to the attacks on Sept. 11, 2001, common discussions regarding supply chain risk management primarily took place in the insurance and risk management industries. For instance, there were concerns about whether shipments of spices were protected from loss due to force majeure, piracy or other threats. However, there was no systematic methodology to analyze shipment risks.
After 9/11, supply chain security began to evolve into a more structured and methodological approach. However, the focus from 2001 to about 2006 was primarily about the physical security of shipments, and cybersecurity was not a necessity per the rules and guidelines. Since 2012, there has been increased awareness and emphasis on cybersecurity in the supply chain process.
One can visualize this evolution from physical to cyber supply chain risk management with the timeline shown in Figure 1.
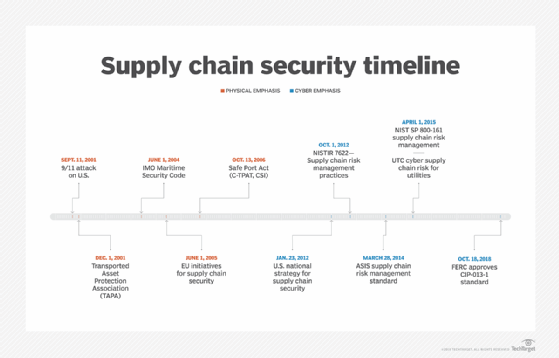
Phase one: Physical supply chain security
The world of security and threat management changed substantially after 2001. There was not only increased sensitivity to transportation security -- such as airport security and the Transportation Security Administration -- but there was also increased concern about maritime security, especially containerized shipments that could contain weapons of mass destruction.
Early on, Congress implemented the Maritime Transportation Security Act of 2002. The act directed the U.S. Customs and Border Protection (CBP) agency to enact the regulations necessary to better secure maritime activities like ship security plans and seaport security assessments. However, this still left a void in how the shipments themselves were tracked, traced and monitored to ensure they were not modified during shipment.
In 2006, the Safe Port Act was signed into law. This law also codified the CBP's physical security programs, such as the Customs-Trade Partnership Against Terrorism (C-TPAT) and the Container Security Initiative. This act included new regulations to assure port operators that the integrity of a container's contents was not modified in transit. This act included the inspection of containers and their contents in foreign ports before they were loaded and placed onto ships bound for the U.S.
As observed in the book Global Supply Chain Security by James R. Giermanski, C-TPAT really began to raise awareness of the concept of an international supply chain and its importance for the security of shipments from beginning at stuffing to arrival at the port of entry.
However, C-TPAT and the Container Security Initiative were still focused on the physical integrity of the shipments and not on the cybersecurity of electronic goods.
Phase two: Cyber supply chain security
After a six-year wait, new emphasis on supply chain security arose first with the U.S. National Strategy for Global Supply Chain Security, a bill signed by then-President Barack Obama. This strategy emphasized that earlier efforts were still important, but that there needed to be a new focus on cybersecurity in the supply chain.
Later work in 2012 and 2015 continued to expand on the concept of physical and cyber supply chain security. Such guidance included "NIST IR 7622: Notional Supply Chain Risk Management Practices for Federal Information Systems," and "NIST SP 800-161: Supply Chain Risk Management Practices for Federal Information Systems and Organizations."
NIST IR 7622 offers some suggested guidelines and "... repeatable and commercially reasonable supply chain assurance methods ... and visibility throughout the supply chain." NIST SP 800-161 covers the concepts from NIST IR 7622, but it includes more specific guidance for U.S. federal agencies to follow to identify, assess and mitigate information and communications technology (ICT) supply chain risks.
In parallel with the release of NIST SP 800-161, the Utilities Telecom Council published cybersecurity supply chain guidance specifically for electric utilities in its document "Cyber Supply Chain Risk Management for Utilities -- Roadmap for Implementation." This report offered ideas and approaches for electric utilities to organize and approach cyber suppliers and minimize cybersecurity risks.
This emphasis on supply chain cybersecurity is not unique to the U.S. The European Union Agency for Network and Information Security (ENISA) published its own overview of ICT supply chain risks in August 2015. ENISA's summary of the concern is well-stated:
Governments, corporations, organizations, and consumers are increasingly reliant on ICT products and services, and thus on the supply chains that deliver them. As a result of this reliance threats to supply chains have attracted more attention, including the threat of intentional tampering during development, distribution or operations, or the threat of substitution with counterfeit (including cloned or overproduced) components before or during delivery, and attacks against the economy through the supply chain.
And, as was mentioned above, FERC just approved a new standard for cyber supply chain risk management -- CIP-013-1 -- that most North American electric utilities must comply with within 18 months following its approval, or around April 2020.
Today, it's not uncommon to see many electric utilities already asking for vendor support via requests for proposal to develop effective and adequate programs to meet these new requirements.
How big is the problem?
This problem is a global one, and it is getting more challenging as supply chain cyberattacks become more sophisticated. But this is not a new problem, as there have been cases of supply chain security issues starting around 2008.
For instance, in 2008, SANS issued a warning that some digital picture frames sold at Walmart had been infected by a virus. Similar reports around this time period indicated that BestBuy had similar issues with some digital picture frames.
SANS also reported in its Digital Hitchhikers series that it received reports of malware contamination in MP3 players, video cameras, external hard drives and USB drives. SANS said "Whatever the cause, there seems to be some sort of breakdown in the security of the supply chain."
Also in 2008, the previously mentioned Bloomberg Businessweek report raised concerns about how counterfeit, defective computer chips and devices from China were being installed in U.S. military fighters and warships. In one example they cited," ... a chip falsely identified as having been made by Xicor ... was discovered in the flight computer of an F-15 fighter jet at Robins Air Force Base in Warner Robins, GA." The 409th Supply Chain Management squadron confirmed that they found four counterfeit Xicor chips.
Later, in February 2017, Microsoft reported a supply chain cyberattack in which the attackers "compromised the update servers for an unnamed third-party editing tool." Essentially, this allowed software updates for the servers to inject malware without users knowing.
That same year, the U.S. Missile Defense Agency reported that counterfeit integrated circuits surfaced in replacement part inventories, U.S. Navy ship-based aviation antenna equipment and helicopter night vision systems.
In a technical paper called "Counterfeit Integrated Circuits: Detection, Avoidance, and the Challenges Ahead," a team of researchers listed ways counterfeit integrated circuits can be pushed into the cyber supply chain. These methods include using:
- recycled/reused chips that have originally been disposed of;
- remarked/relabeled chips;
- sale of out-of-specification/defective chips;
- cloned or copied chips;
- forged certificates of compliance for the supplied chips; and
- altered chips.
Where to start and how to protect your company
Most North American electric utilities are obligated to comply with CIP-013-1 and "... develop one or more documented supply chain cyber security risk management plan(s) for high and medium impact BES Cyber Systems." The U.S. federal government is obligated to comply with NIST SP 800-161. These are good starting points for all companies. However, there are other considerations.
It's important to understand your company's supply chain. Understand how the supply chain works with suppliers, their suppliers, the transport/shipping mechanisms, how you receive and inspect the ordered products, how and where you store the products, and so on. Basically, understand where the inject points are and where changes can be made to physical, software and firmware integrity.
It's also necessary to understand your procurement strategy. How does your company qualify its suppliers? How are the suppliers checked to ensure that they have a security program and that they follow it?
Be sure to know who the users of the end product of your supply chain are. For instance, do these users simply plug and play the device into systems without inspection and hardening or do they inspect the part for tampering and verify that the part or subsystem is updated with a new password and is patched?
Map all the players of your supply chain -- and include your supplier's suppliers if you can. Once this is done, review the mapping and supply chain flow and identify threats and vulnerabilities. Then, act to remediate these risks.
Establish processes to review supply chain physical and cyber risks continuously and constantly enhance the methodologies used to reduce the chances of counterfeit or flawed parts/subsystems.
Consider the reliance on standards such as the Open Trusted Technology Provider Standard and the Software Assurance Forum for Excellence in Code. Verify and encourage your suppliers to adhere to these standards and become certified as compliant if possible.
The future of supply chain security
With the official approval of CIP-013-1, the ramifications of the supposed attack on server circuit boards as reported by Bloomberg Businessweek, and increased concerns about software integrity and legitimacy, it will be very surprising if supply chain security turns out to be a fad. Soon there will be more guidelines, standards and checklists developed and promulgated to help different critical infrastructure and industry sectors better protect their procurement and supply chain processes.






