
lolloj - Fotolia
What enterprises need to know about ransomware attacks
Ransomware attacks on enterprises are often the result of a company's poor IT hygiene. Expert Joe Granneman looks at attacks like those by WannaCry and SamSam ransomware.
2017 was the year that ransomware became a boardroom-level concern.
Management looked agog at images of compromised systems at airports and on billboards around the world. They reached out to their IT managers, frantically seeking reassurance that their organization was safe from attack.
The IT staff, in turn, was searching through technical documentation and reviewing the company's security patch deployment status. The security industry responded with a plethora of new products and informational webcasts to capitalize on ransomware fears.
Our firm received its own share of questions about how organizations should defend their networks against this new threat. Our answers typically involve basic security hygiene issues, such as patching, password strength, antivirus software, employee training and monitoring. We learned quickly that these weren't the answers that clients expected or appreciated.
Users seemed to be looking for that high-tech silver bullet solution to their problem being peddled by security vendors all over the internet. The assumption these clients were making was that ransomware must be state-sponsored or designed by an uber-hacker because it was doing so much damage. These IT departments prioritized patching for ransomware vulnerabilities even when they were still missing the decade-old patch for MS08-67 -- the vulnerability exploited by the Conficker worm and patched by Microsoft in 2008.
These IT departments were not alone in their response, as we have all gotten used to setting our security risk priorities based on news articles and vulnerabilities that have catchy names and logos. This reactive style of information security management will not succeed, and it can ultimately lead to more ransomware attacks as basic IT hygiene falls behind.
Ransomware has not been successful because a fictional uber-hacker used a newly developed attack. It is successful because some organizations make basic IT management mistakes, such as the following:
- Inventory management: Organizations lose track of what systems are available on the internet.
- Configuration management: Organizations mistakenly open services to the internet that did not need the internet to function.
- Network segmentation: Organizations do not utilize a DMZ, which enables inbound services from the internet to target internal network hosts.
- Vulnerability management: Organizations do not address critical vulnerabilities in internet-accessible systems.
You need look no further than the news to find evidence of these IT hygiene failures. Many of these public ransomware attacks can be investigated using open source intelligence tools.
The security search engine Shodan.io may be all you to need to make an educated guess about how these public ransomware attacks unfolded. Shodan.io scans the internet regularly and discovers open services, and then organizes the results in a searchable database. You can easily search by organization using the built-in Shodan.io query, org: "organization name". The query can then be further refined to locate vulnerable services typically used by ransomware.
SamSam ransomware attacks
One of the most common ransomware exploits is SamSam, also known an Samas. It made the rounds a few years ago and has made a strong comeback in 2018. SamSam works against web servers running vulnerable versions of Java applet servers like Tomcat and JBoss. It uses an exploit to gain system-level access on a web server and then recover any available administrative credentials.
The attacker can then use these harvested credentials to target the rest of the internet network for encryption. These attacks start by scanning for potential targets running these vulnerable servers. Shodan.io has already performed a similar scan and will have the results for investigation even if the targeted organization has taken their network offline.
Here is example of an organization that did make the news recently after being hit with SamSam. A Shodan.io query was run against the organization name and filtered for available JBoss services. The potential source of the infection popped up right away, as a server was found running an old version of JBoss that is vulnerable to the exploits used by SamSam.
This version of JBoss -- version 1.1 -- was released in 2006, and the server has not been updated since the initial release, making it an easy target for ransomware.
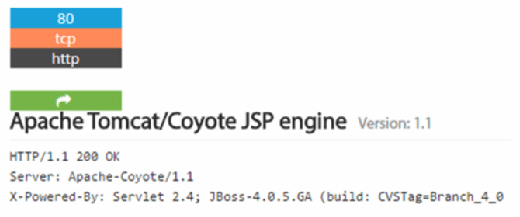
These JBoss search results are bad enough for an organization that has already been targeted by ransomware. Unfortunately, bad IT hygiene runs deep, and there are sure to be other vulnerable servers operated by this organization.
Additional Shodan.io searches find that Remote Desktop Services are enabled and a MySQL Server is available on the same subnet. These are prime targets for hackers and ransomware. They were not compromised in the JBoss attack, but they will be if they are left on the internet.
Many organizations forget that the local administrator account will not lock out users when brute-forced, making the remote desktop protocol an attractive attack vector. Some organizations even allow public connections to their remote desktop servers, so the attacker can see the domain name in use and any user accounts logged in.
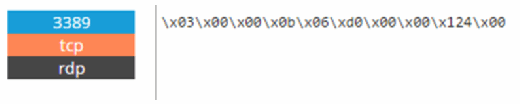
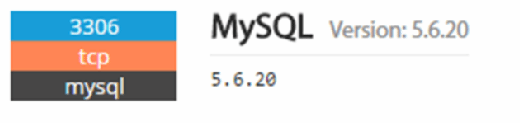
Ransomware attacks like SamSam and WannaCry will probably continue to make headlines in 2018. Their enormous success is directly related to the lack of basic IT hygiene.
There are inexpensive tools, such as Shodan.io, that are available to help organizations easily identify their internet-facing inventory and potential vulnerabilities. Good IT hygiene is the most cost-effective way to protect organizations from ransomware, as it doesn't require additional security products.
Organizations may finally start to address these basic IT foundational processes now that there is board-level attention to the risks associated with ransomware attacks. Maybe this is the bright side of ransomware.




