
What reverse shell attacks are and how to prevent them
Attackers use reverse shells to covertly attack an organization's environment. Discover what a reverse shell is and how to mitigate such attacks.
Attackers infiltrate target environments in a variety of ways. One common method is a direct attack. Another, called a reverse shell, uses a remote device to deploy an attack.
Let's look at what a reverse shell attack is, how it differs from a direct attack and how to prevent it.
Direct attack vs. reverse shell
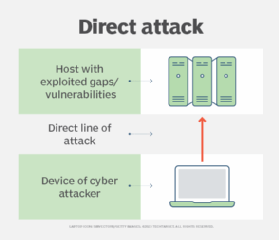
When people hear "cyber attack," they often think of a direct, brute-force attack where the attacker gains access to a server, workstation, wireless device, etc. To penetrate a device in a direct attack, the malicious actor exploits vulnerabilities or security gaps and then deploys a malicious payload, as illustrated in Figure 1.
Many cyber attacks are direct attacks.
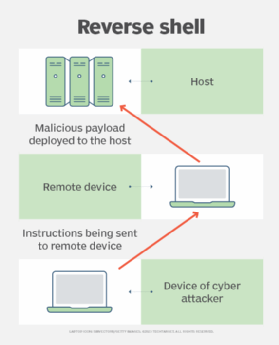
In the more roundabout reverse shell attacks, malicious actors use remote devices to connect to the target's host. All command and control takes place on the attacker's device, but the remote device executes all commands and directives to the host. This is illustrated in Figure 2.
This approach is used for the following reasons:
- Attackers are masked behind a remote device, making it difficult to be discovered.
- By using a remote device, hundreds and even thousands of other hosts can be infected at the same time, as evidenced in the SolarWinds attack.
The following two shells exist:
- Normal shell session. A shell is created when users first start up their devices. Each device has only one shell session. It serves to interpret user commands.
- Reverse shell session. This is where an attacker initiates a shell session with a host using a remote device. Once granted, the attacker has access to the host.
How a reverse shell attack is launched
In reverse shell attacks, malicious actors wait for the host to request a connection to the outside, thus giving the attack the name reverse shell. Through remote devices, attackers can configure the host and request connections outside the target's network.
Once this happens, attackers can execute a suite of commands via the remote device, for example, to deliver a malicious payload to the host. The attackers then can gain a foothold into the host and wreak havoc.
Malicious actors usually want to remain unnoticed in reverse shell attacks. Their goal is often to stay inside the environment as long as possible to move laterally within infrastructure. Once attackers find what they want, the data exfiltration process starts. Attackers often move stolen data to the hacked remote device for temporary storage.
How to prevent reverse shell attacks
Organizations should do the following to prevent attackers from setting up reverse shells:
- Conduct vulnerability scans. Vulnerability scans reveal open ports in network infrastructure. Ports that aren't required for business operations should be closed immediately.
- Have good password hygiene. Have a solid password security policy that requires employees to use unique and complex passwords for every account and to update passwords every few months. This helps prevent attackers from accessing remote devices and elevating privileges to initiate a reverse shell.
- Regularly patch hosts. Keep up to date with patch management to ensure devices are protected against the latest attacks. Having host systems regularly patched lowers the chances of attackers penetrating unpatched vulnerabilities.
- Change firewall rules. Most firewalls and routers are configured to examine inbound network traffic because threat vectors often come directly from outside. Configure firewalls to also examine outbound traffic for suspicious activity.
- Limit outbound access. Limit how much outbound access employees have. Consider restricting remote access to only IP addresses and ports that are required for employees to do their daily jobs.








