
Getty Images/iStockphoto
How to use arpwatch to monitor network changes
The arpwatch utility flags administrators in the event of any unexpected changes or unauthorized devices, which could signal ARP spoofing or credential-harvesting attacks.
Managing the devices that connect to a network is critical, and Layer 2 MAC addresses are some of the most fundamental identifiers.
Network devices use the Address Resolution Protocol (ARP) to connect Layer 2 MAC addresses with logical IP addresses. Tracking these mappings is essential to ensure only authorized devices connect to a network.
The arpwatch utility helps administrators track physical MAC addresses and logical IP addresses to detect unexpected changes and -- potentially -- unauthorized devices. Its fundamental goal is to alert administrators of changes to the nodes on the network.
Each network interface card (NIC) has a unique MAC address that identifies it. When two devices exchange data over the network, the source and destination MAC addresses -- also known as physical addresses -- are part of how the nodes identify each other.
Network nodes also have logical addresses. Sending and receiving computers use these IP addresses to identify each other.
When addressing network data frames, source computers broadcast an ARP message asking the computer with a given IP address to respond with its MAC address.
The arpwatch utility uses this information to build a database of related MAC and IP addresses. As more data flows in, this database, based on these addresses, becomes an accurate reflection of a network environment. Changes to this configuration become anomalies, triggering arpwatch to issue warnings to administrators.

Arpwatch also offers the following security features:
- ARP activity monitoring. Arpwatch monitors MAC and IP address exchanges, providing a more holistic view of a network environment for security and troubleshooting.
- Security alerts. Arpwatch alerts administrators to suspicious activity, including ARP and MAC address spoofing.
- Logging. Arpwatch stores MAC and IP address pairings in a database and alerts administrators to changes.
When using arpwtch, consider deploying and running it in daemon mode. In this configuration, it runs continuously in the background to monitor network connections for unexpected or suspicious changes.
For example, suppose a malicious actor deployed a Raspberry Pi device on your network -- this is relatively easy to do based on the device's small size. The Pi might contain a rogue website requesting security information from users as part of a credential-harvesting attack. Arpwatch should notice the unauthorized device and alert administrators. It can also protect wireless networks from similar attacks and rogue devices.
How to install arpwatch
As with most Linux applications, install arpwatch using your distribution's preferred package manager. The commands are usually apt or dnf, but they could vary. Security-oriented distributions, including Kali Linux, Parrot Linux and others, typically include arpwatch.
On Debian, Ubuntu and similar distributions, type:
apt install arpwatch
On Red Hat Enterprise Linux, Fedora, Rocky and AlmaLinux, type:
dnf install arpwatch
Arch Linux users can type:
pacman -S arpwatch
Install MacPorts to add arpwatch to your macOS system. Direct options for Windows systems are not available, so consider tools such as ARP Monitor or NetCut.
How to use arpwatch
Plan to use arpwatch as a set-it-and-forget-it kind of service. As such, your main tasks are configuring the service and setting it to run when the system is online.
The arpwatch configuration file on Fedora is /etc/sysconfig/arpwatch, though the location could vary by distribution. Use your favorite Linux text editor to modify the file's settings.
Common file settings include the following:
- DEVICE=eth0 substitutes your system's device name.
- [email protected] substitutes the email address to receive alerts.
- RUN_DAEMON=yes enables daemon mode.
- ARP_FILE=/var/lib/arpwatch/arp.dat defines the database location.
- resolve specifies DNS reverse name resolution to resolve hostnames from IP addresses.
- dhcp-snooping enables correlation of MAC and IP addresses using the Dynamic Host Configuration Protocol.
Start and enable arpwatch using the systemctl command:
systemctl enable arpwatch
systemctl start arpwatch
You will need an SMTP client on the system to forward email to an SMTP server. Most distributions include this. Don't forget to configure firewall rules to permit SMTP traffic -- usually 25/tcp -- and set up name resolution.

How to display arpwatch results
You'll usually deploy arpwatch as a long-term option to monitor MAC and IP addresses. It generates a database of these mappings. You can find the database at /var/lib/arpwatch/arp.dat on most Linux distributions. Arpwatch reports actual changes to the system log.
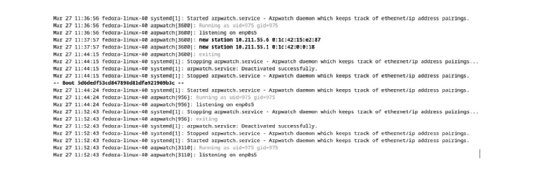
Use the journalctl command to display the arpwatch results. The command is:
sudo journalctl -u arpwatch
The log results show whether the MAC-IP mapping is new or changed.
Advanced features
The arpwatch utility is pretty straightforward, so there aren't a lot of additional or advanced features. Some specific options, however, might make it more effective for your monitoring needs.
To run arpwatch manually on a single interface, type:
arpwatch -i eth1
MAC addresses consist of two parts. The first half is a vendor identifier, and the second half is a unique interface identifier. That means you can determine the NIC's manufacturer from the MAC address. The arpwatch tool can accomplish this with a little extra configuration.
First, install the IEEE organizationally unique identifier database of vendor and MAC address mappings. Some distributions provide an automated script:
/usr/local/arpwatch/update-ethercodes
On other systems, use this command to download the database:
wget https://standards-oui.ieee.org/oui/oui.csv -O /usr/local/arpwatch/ethercodes.dat
Next, add the following line to the /etc/sysconfig/arpwatch configuration file:
ARPWATCH_LOCAL_DIR=/usr/local/arpwatch
Restart the arpwatch service to implement the changes:
systemctl restart arpwatch
Log entries should now include the NIC vendor.
Related MAC address and ARP tools help with similar queries and tracking. You can read more about them on the Kali Linux website.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to Informa TechTarget, The New Stack and CompTIA Blogs.






