
Prostock-studio - stock.adobe.co
How CIOs can build cybersecurity teamwork across leadership
Cross-departmental relationships are key to long-term business success. Discover why CIOs must focus on teamwork with these three C-suite roles for highly effective cybersecurity.
Protecting the company against cyber attacks is a cross-organizational endeavor. And while employees are often called the first line of defense, it's critical not to overlook senior leaders and the C-suite.
IT has a lot of work to do in defending the organization against hackers, which includes ensuring endpoint protection, backing up data, installing firewalls and keeping software up to date. What is often overlooked is the human part of the security equation.
Importance of cross-department cybersecurity teamwork
Having worked in IT for over three decades, I'm certain of one thing: Most business success relies on the quality of cross-departmental relationships with other people, especially regarding information security.
If a CIO doesn't have allies to support and help execute security initiatives, those initiatives are much more likely to fail. Successful enterprise security depends on cybersecurity teamwork among IT admins, security managers and anyone else involved with making things happen in the realm of security.
Without credibility and the necessary political and financial backing, company leaders can push aside critical security projects or nix them altogether. Some will likely fail after a few months, while other projects might be withdrawn a year or two after implementation. A security project rarely fails due to a lack of technical abilities by the CIO and IT staff. And a lack of success often has little to do with budget.
The critical factor CIOs must understand is knowing how to discuss security and build relationships during short-term projects that will follow them throughout their career.
Because senior leaders are so important to cybersecurity success, CIOs need to pay particular attention to the strategic buy-in of C-suite leaders. And while there are a range of stakeholders that matter, there are some C-suite roles, in particular, that are important to cybersecurity success.
C-suite roles critical to cybersecurity
Security success depends in part on knowing who to seek out for help. Some of those relationships are obvious. The CIO might already have a good relationship with the CISO. Hopefully, that's the case because both the CIO and CISO roles are essential for building an effective security program.
The CTO and the chief risk officer (CRO) already play critical roles for security success, due to their technical, legal and compliance expertise. All the CIOs that I have worked with have strong relationships with both the CTO and CRO. But there's more.
3 overlooked C-suite roles the cybersecurity team needs
Looking beyond the relationships that help lower risk, a CIO might wonder who else to partner with to help strengthen the business's security. I found three specific overlooked roles that could help a CIO's security plan, after studying relationship dynamics and reviewing well-run security programs.
The three overlooked roles are the CEO, the chief HR officer (CHRO) and the CFO. Ongoing relations with these executives can transform an organization's security program.
1. The CEO, to be the chief cybersecurity partner
Partnering with the CEO is essential if a CIO wants to use technology to strengthen security and drive the business forward. As part of that relationship, the CIO needs to work with the CEO to answer the following questions:
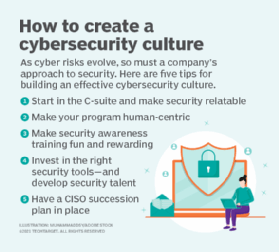
- How can the CEO and CIO enhance business security together?
- How will the CIO use security as a competitive advantage through new or improved products and services?
- What specific messaging does the CEO envision could get the most security buy-in from employees?
- What's the best way for the CEO and CIO to promote the company's goals?
People listen when the CEO speaks. The key to fostering a security culture that involves everyone is to fully engage the CEO. A CEO is pivotal in communicating and encouraging worthwhile security measures throughout the organization. They can also help with avoiding any potential roadblocks.
Unless the CEO has the CIO's back, the IT leader will likely hit barriers in improving organizational security.
2. The CHRO, to build the security culture
The CHRO is pivotal to preventing cyber attacks and in shaping security culture. And yet, the CIO-CHRO relationship is another potentially overlooked relationship critical to improving security.
As the chief people officer, the head of HR focuses on the best ways to manage, oversee and train people. These are all critical elements of a effective security program. The hybrid balance of in-office and remote work requires consideration of the human aspects of cybersecurity.
HR professionals are the best at sharing ideas on communicating and educating employees. They often do so in ways that IT professionals wouldn't think of. Some questions to help foster better communication could include the following:
- How can the CIO work with the CHRO to correctly communicate critical corporate IT and security policies to everyone beyond the employee handbook?
- What information does the CHRO need from the CIO -- and likely the CISO -- to properly set expectations for employees using corporate systems and information assets?
- What suggestions might the CHRO have for continuous employee education programs related to IT and security?
CIOs should work with CHROs to improve cybersecurity communications and messaging to employees. They can help determine the key communication methods and frequency to ensure employee compliance with secure practices.
3. The CFO, to help with financial backing
Money isn't everything, but it's crucial for achieving organizational goals. A good CFO can initiate positive changes when they understand the CIO's security needs. Some questions to help foster that understanding include the following:
- How can the CIO work with the CFO in terms of risk mitigation from a financial perspective?
- Can the CFO provide examples of successful security budget allocations?
- What budget allocations will help every department get what they need from IT and security efforts?
- Does the CIO or CFO have any changes in mind for future budget allocations?
In my experience, CFOs can -- and often do -- help push security initiatives forward more than any other executive.
Use executive relationships to build a security committee
Many organizations still need a security committee that involves people outside of IT and those in executive roles who can help ensure that things get done. The CIO can foster a security committee if there isn't one by capitalizing on the relationships. This group can meet periodically to discuss known risks and the organization's overall cultural direction of security, including analyzing what's working well and what isn't.
One key thing to remember is having an open mind. Many IT professionals fear involving people outside of IT will taint the security program, but I've seen the opposite. Nontechnical business professionals can offer vastly different perspectives to improve security because they don't have to navigate the CIO's day-to-day technical complexities. Letting the big security decisions come from a committee provides the benefit of not having that burden lie largely on the CIO's shoulders. Instead, it's coming from diverse perspectives to help ensure everyone is working toward the business's best interests.
Cybersecurity relies on communication
Practically everything in the business relates to security. Everything that the CIO does -- or doesn't do -- with security counts. Security success requires strong partnerships with people outside of IT.
The CIO should feel comfortable with being open and honest, starting with being a good communicator. Collaborate and get outside advice. The CIO should carry out favors from other departments whenever possible. These actions will all come back to help the organization's overall security efforts.
In a world where many people still work to justify cybersecurity funding and planning, this is a solid partnership strategy that will pay great dividends over the long haul.








