What is infrastructure (IT infrastructure)?
Infrastructure is the foundation or framework that supports a system or organization. In computing, IT infrastructure is composed of physical and virtual resources that support the flow, storage, processing and analysis of data. Infrastructure might be centralized within a data center, or it might be decentralized and spread across several data centers that are either controlled by the organization or by a third party, such as a colocation facility or cloud provider.
Infrastructure components
On-premises
Data center infrastructure often includes the power, cooling and building elements necessary to support data center hardware. The data center hardware infrastructure usually involves servers; storage subsystems; networking devices, like switches, routers and physical cabling; and dedicated network appliances, such as network firewalls.
A data center infrastructure also requires careful consideration of IT infrastructure security. This can include physical security for the building, such as electronic key entry, constant video and human surveillance of the premises and carefully controlled access to the server and storage spaces. This ensures only authorized personnel can access the data center hardware infrastructure and reduces the potential for malicious damage or data theft.
Internet
Outside of the data center is an internet infrastructure, which includes transmission media, such as fiber optic cables, satellites, microwave -- line of sight -- antennas, routers, aggregators, repeaters, load balancers and other network components that control transmission paths. Internet infrastructures are designed, built and operated by internet service providers (ISPs), such as Verizon and AT&T. When a business engages an ISP for internet access, the ISP typically ties into the data center infrastructure within a dedicated and secured building space.
Cloud computing
The role of cloud computing is changing the way infrastructures are designed and implemented. Where traditional, business-owned data centers are private, capital-intensive resources, cloud computing enables organizations to access a cloud provider's data center infrastructure and services for a fee.
This infrastructure-as-a-service (IaaS) model allows flexible computing on demand. Users can invoke a cloud provider's compute, storage and services without the need to deploy those resources locally -- and adjust cloud infrastructure usage as workload needs change.
The software-as-a-service (SaaS) model offers similar benefits for specific workloads. A third-party provider hosts hardware, software, servers, storage and other infrastructure components, and enables users to access the provider's hosted workloads instead of deploying and maintaining them locally. For example, users can employ SaaS workloads for databases, human resources applications, analytical applications and office productivity suites.
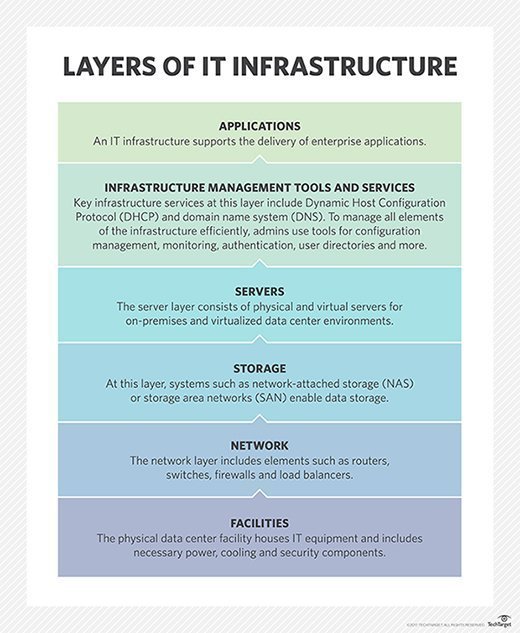
How infrastructures are created
To create a traditional data center infrastructure, organizations typically follow a formalized process. The process starts by analyzing and accessing business goals, making architectural and design decisions, building and implementing the design, and then optimizing and maintaining the infrastructure. The process usually involves detailed expertise, including data center building design, subsystem and component selection, and quality construction techniques.
IT infrastructure design is continually changing. Traditional heterogeneous infrastructure development is a highly manual process that requires enormous integration, optimization and systems management efforts -- especially when integrating servers, storage, network and other components from diverse vendors.
Some vendors provide pre-integrated and pre-optimized collections of compute, storage and network equipment that optimize the IT hardware and virtualization platform into a single system that can be easily deployed, expanded and managed. This modular approach is called converged infrastructure (CI). This notion has advanced into single-vendor systems that offer tighter integration and management over compute, storage, network and virtualization. This advanced approach is called hyperconverged infrastructure (HCI).
Infrastructure management
Regardless of how it is created, an IT infrastructure must provide a suitable platform for all the necessary IT applications and functions an organization or individual requires. This means the design and implementation of any IT infrastructure must support efficient infrastructure management.
Software tools
Software tools must enable IT administrators to view the infrastructure as a single entity, as well as access and configure granular operating details of any device in the infrastructure. This single-pane-of-glass objective results in more effective and efficient infrastructure management. Solid management also enables admins to optimize resources for different workloads, and to more readily understand and handle the impact of any changes on interrelated resources.
Infrastructure management is often divided into multiple categories. For example, a building management system (BMS) provides the tools that report on data center facilities parameters, including power usage and efficiency, temperature and cooling operations and physical security activities.
System management
Systems management includes the wide range of tool sets an IT team uses to configure and manage servers, storage and network devices. System management tools support remote data centers, along with private and public cloud resources. Management tools are also making extensive use of automation and orchestration to improve efficiency, reduce errors and comply with established best practices or business objectives.
Types of infrastructures
As business needs and available technologies advance, organizations can use a more diverse assortment of IT infrastructure types to meet business goals.
AI infrastructure
Organizations use AI infrastructure to support data and AI algorithms. This infrastructure uses AI and machine learning (ML) software to gather and deploy information and applications within the data center more efficiently. There are four sections to AI infrastructure: compute resources, data storage and processing, ML and MLOps platforms.
Cloud infrastructure
A cloud infrastructure includes an abstraction layer that virtualizes resources and logically presents them to users over the internet. This could be done through application program interfaces and API-enabled command-lines or graphical interfaces. Additional capabilities include user self-service, automated billing or chargeback, and user-side reporting. This enables users to see the resources and services they deploy, as well as corresponding costs.
Similarly, a cloud storage infrastructure is a framework composed of hardware and software that supports the computing requirements of a private or public cloud storage service.
Composable infrastructure
A composable infrastructure is a framework that treats physical compute, storage and network fabric resources as services. Resources are logically pooled, so administrators don't have to physically configure hardware to support a specific software application. Admins can organize and manage the resources through software tools using a high level of automation and orchestration, enabling software-defined infrastructure capabilities for the data center.
Contact center infrastructure
A contact center infrastructure is a framework composed of the physical and virtual resources that a call center facility needs to operate effectively. Infrastructure components include automatic call distributors, integrated voice response units, computer-telephony integration and queue management.
Critical infrastructure
A critical infrastructure is a framework for which assets are so essential that their continued operation is required to ensure the security of a given nation, its economy and the public's health and safety. The concepts surrounding high availability (HA) and resilience are essential, often including remote data centers and cloud resources to support workload redundancy.
Dark infrastructure
A dark infrastructure is the part of a framework that is composed of undocumented, but active, software or services whose existence and function are unknown to system administrators -- despite the fact it might be integral to the continued operation of documented infrastructure. This is often referred to as shadow IT, and it can become a serious security or compliance vulnerability for the organization.
Dynamic infrastructure
A dynamic infrastructure is a framework that can automatically provision and adjust itself as workload demands change. This minimizes the time and effort needed to manage the infrastructure and vastly reduces errors, while ensuring resources are used as efficiently as possible. IT administrators can also choose to manage these resources manually.
Immutable infrastructure
An immutable infrastructure is an approach to managing services and software deployments on IT resources wherein components are replaced, rather than changed. An application or service is effectively redeployed each time any change occurs.
For example, a patch or hotfix might update a conventional app, but an immutable infrastructure does not support this. Instead, IT deploys the newer app, redirects traffic to it and retires the old app.





