
Getty Images
Why business leaders must explore post-quantum pre-quantum
With the continual advance of quantum technology comes threats to traditional cryptographic standards. Discover how to prepare for PQC pre-quantum.
For businesses, post-quantum cryptography (PQC) is more than a technical upgrade -- it's necessary to protect digital interactions. Organizations are under heavy pressure to begin migrating to quantum-resistant algorithms to protect their business, customer data and the transactions they facilitate online.
PQC refers to cryptographic algorithms that can resist attacks from classical and quantum computers. Current public-key cryptography systems rely on mathematical problems, like integer factorization and discrete logarithms. PQC algorithms use mathematical foundations that experts believe are quantum-resistant.
The NIST's official timeline states that legacy public key encryption systems will be deprecated by 2030 and should be disallowed by 2035. NIST also published three finalized post-quantum encryption standards that organizations can use as guidance to withstand quantum attacks. To prepare for this new era in computing, business leaders must understand quantum's effect on the following:
- Public key encryption.
- Digital signatures.
- Symmetrical encryption.
- Data exposure.
Discover the importance of organizational quantum readiness and understand the steps your organization can take to develop a successful PQC strategy. These steps include identifying cryptographic assets, evaluating any quantum risks, adopting crypto-agility, gaining leadership investment and training teams at every level of the organization.
Why PQC matters
Quantum computers pose several threats that span timelines, each requiring a different organizational response. Within the next three years, businesses could experience costly harvest now, decrypt later (HNDL) attacks. Threat actors are already collecting encrypted data; all they need are quantum computers capable of decrypting it. For organizations operating in specific industries such as defense, healthcare and research, data confidentiality is vital and sometimes requires maintaining records for years.
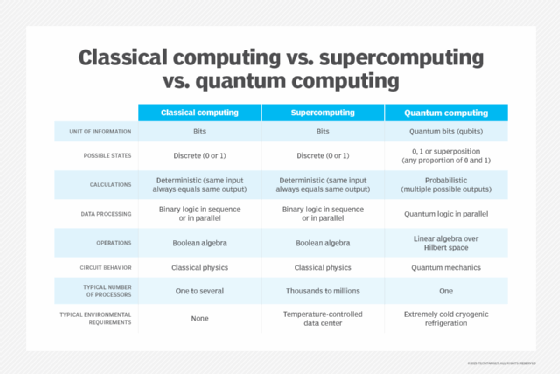
Over the next decade, specific quantum computers, powered by 1,000–10,000 logical qubits, could break cryptographic systems. This is especially true of systems that rely on outdated security protocols or short key sizes, such as the Rivest-Shamir-Adleman (RSA) algorithm and elliptical curve cryptography (ECC).
The biggest threat exists in the long term. Fully capable quantum computers will be ready to break public key cryptography systems. At this stage, all unprepared organizations will become vulnerable to quantum threats, and their data protected using old encryption systems will become compromised. Consider the following data security threats that quantum computing could pose across sectors:
- Healthcare. Organizations operating in the healthcare industry follow regulations to maintain patient records for extended time periods. Compromising such data could lead to privacy violations, such as blackmail, fraud or sale to outside parties.
- Finance. Companies use traditional encryption to protect customer data, transaction records, trading algorithms and confidential communications. Quantum computers could expose trade deals worth billions of dollars and customer accounts. A study by Hudson Institute found that a quantum-enabled cyberattack on a critical U.S. financial infrastructure (Fedwire) could produce indirect GDP losses between $2 and $3 trillion.
- Government and defense. Governments protect military secrets, intelligence sources and methods, diplomatic communications, personnel records and weapon system designs using traditional encryption algorithms. Threat actors and organized criminal groups are collecting this data now for their HNDL efforts.
- Technology and intellectual property. Software companies, pharmaceutical researchers and other research firms use encryption to protect their data, product designs, proprietary algorithms and trade secrets. The introduction of quantum computers could expose proprietary code, models and patent-pending innovations. This represents billions of dollars in R&D loss and catastrophic consequences for the affected firms.
The emerging PQC compliance and regulatory landscape
International regulations are pushing toward PQC transition. NIST finalized its first set of PQC standards in 2024, aiming to replace quantum-vulnerable public-key algorithms by providing cryptographic mechanisms that are secure against both classical and quantum adversaries. Specifically, these standards address the following:
- Protecting secure communications.
- Developing quantum-resistant digital signatures for authentication and code signing.
- Preventing data exposure.
- Encouraging gradual migration from traditional to quantum cryptography.
- Establishing a global standard for quantum-safe cryptographic implementations.
The EU, with support from the European Commission, adopted a joint roadmap in June 2025. This initiative outlines the following key recommendations and concrete milestones for migration:
With a better understanding of current milestones and planned progression toward PQC, businesses can develop a framework to prepare for PQC.
Steps to prepare for PQC
Transitioning into the quantum-safe era is a multi-year journey that requires a structured approach. Here are the main phases involved in executing a successful PQC transition.
Phase 1: Discovery
For businesses to protect their data, they must know where it is and how it is protected.
- Classify data based on its severity and criticality to business operations. Data that must remain secure for 10 years or more (e.g., trade secrets or patient data) is a higher priority due to HNDL attacks.
- Identify all cryptographic assets within the organization, such as hardware, software and network protocols.
- Identify all third-party dependencies within the IT environment. These include cloud providers, SaaS vendors and supply chain partners. Their quantum readiness is essential to organizational security.
Phase 2: Risk assessment
Assess the impact of a successful quantum breach against existing systems. Prioritize these systems based on the following risk types:
- High risk. This includes long-term sensitive data (e.g., trade secrets, weapon systems design and patient records) and critical infrastructure (e.g., control systems, design and encryption methods).
- Medium risk. Any operational data with a three- to five-year sensitivity.
- Low risk. Such as short-lived session data.
Phase 3: Invest in infrastructure
Begin to consider infrastructure requirements for implementing PQC. Audit and test existing hardware to ensure it can support PQC adoption. Then, implement one of the following approaches:
- Crypto-agile approach. Design or upgrade systems to become crypto-agile. This requires the ability to shift encryption algorithms using simple configuration steps without changing the hardcoded logic of the cryptographic system.
- Hybrid cryptographic approach. This combines both classical encryption algorithms, such as RSA and ECC, and PQC algorithms in a single unit. This ensures your system can withstand current and post-quantum decryption threats.
Phase 4: Collaboration and leadership
PQC migration is a strategic decision that requires buy-in and support from upper management and executive leadership. Collaboration is vital to achieve the following:
- Secure a budget for PQC transition.
- Create a cross-functional PQC task force.
- Collaborate with third-party vendors.
Phase 5: Employee education
Employee education about PQC should be comprehensive and target the following organizational groups:
- Technical staff. These groups should know how PQC differs from traditional cryptographic algorithms in terms of key size, signature size and mathematical foundations.
- Leadership. The risk of HNDL should be communicated effectively to help leaders understand the current risks against sensitive data. Leaders must also understand regulatory timelines, budget requirements, competitive implications and their governance responsibilities.
- Compliance, legal and procurement teams. These groups require awareness of emerging global PQC regulations, contractual obligations and vendor assessment criteria so they can integrate quantum readiness into their organizational processes.
Challenges to implementing PQC
PQC migration involves several technical, operational and organizational obstacles. The major challenges include performance impacts on current operations, integration with legacy systems and cultural shifts.
Technical challenges
The properties of PQC algorithms differ from those of traditional algorithms. These differences could create challenges, including quantum's larger key size for algorithms, and bandwidth and storage issues when supporting these larger keys. Traditional network infrastructure could also fragment data from PQC packets as they require more resources.
Operational challenges
Operational challenges include supply chain risks and talent shortages. Consider organizational vendor and supply chain dependencies. While a business organization might be ready to migrate to PQC, its partners might not.
Further, implementing a PQC system requires expertise in both quantum-resistant mathematics and modern encryption engineering. Such expertise is still rare.
Organizational challenges
The two main organizational challenges are complexity and cost. Implementing PQC requires dedicated hardware and numerous tests to ensure everything is operational. This costs millions of dollars for large enterprises.
Many organizations are also unaware of which systems in their environment use cryptography. Undocumented legacy systems and IT systems without major upgrades can make it difficult to perform the necessary inventory before migration can even begin.
Adopting PQC too quickly could also be risky for organizations, as current standards evolve within the coming years and more businesses implement quantum technology. This could force early adopters to undergo another expensive and difficult migration, costing them more money and effort.
Nihad A. Hassan is an independent cybersecurity consultant, digital forensics and cyber OSINT expert, online blogger and author with more than 15 years of experience in information security research. He has authored six books and numerous articles on information security. Nihad is highly involved in security training, education and motivation.







