What is SD-WAN (software-defined WAN)? Ultimate guide
SD-WAN explained
Software-defined WAN is a technology that uses software-defined networking concepts to distribute network traffic across a wide area network, or WAN.
Enterprises and organizations have adopted SD-WAN as a cost-effective way to connect branch offices to their own data centers and to SaaS- and cloud-based applications. SD-WAN provides automation, centralization and flexibility, which creates a more agile WAN environment for midsize and large businesses.
This comprehensive guide explores the benefits and challenges of SD-WAN, use cases, deployment strategies and how to buy the technology.
How does SD-WAN work?
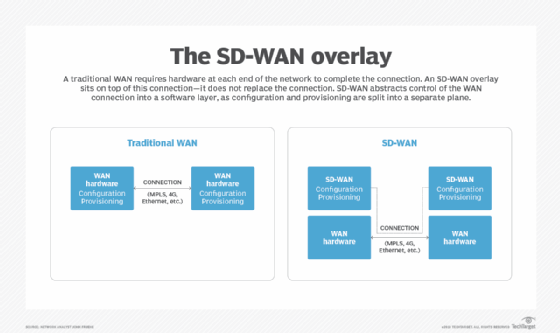
SD-WAN architecture creates a virtual overlay that abstracts underlying private or public WAN connections, such as Multiprotocol Label Switching (MPLS), internet broadband, fiber, wireless or 5G. This overlay enables enterprises to keep their existing WAN connectivity while the SD-WAN centralizes network control and enables real-time application traffic management over the links.
A centralized controller manages the SD-WAN. The controller is typically a software client that directs data flows between two points and distributes network and security policies to all connected devices. The controller enables IT staff to program network edge devices with low- or zero-touch provisioning (ZTP). It also minimizes the need for network engineers to manually configure routers in branch locations.
Providers typically offer SD-WAN in two models: overlay SD-WAN, or as a managed service.
With an overlay SD-WAN, a vendor provides the customer with a network edge device that contains the software necessary to run the SD-WAN technology. To deploy the SD-WAN, customers plug their WAN links into the device, which automatically configures with the network. Managed SD-WAN enables customers to access the provider's network without owning or managing it themselves.
Despite the differences among SD-WAN offerings, most deployments have the following capabilities in common:
- Virtualization of the WAN connection.
- Centralized policy oversight.
- Orchestration.
- The ability to manage traffic dynamically.
What are SD-WAN use cases?
SD-WAN use cases extend across many industries, including the following:
- Retail.
- Government.
- Financial services.
- Manufacturing.
- Healthcare.
Large enterprises with multiple sites worldwide have a compelling use case because SD-WAN can help manage branch offices more easily. Smaller enterprises can capitalize on SD-WAN's ability to work with multiple WAN types, such as broadband or 5G. Enterprises can also benefit from managed SD-WAN services, in which a provider implements, manages and troubleshoots the service.
As SD-WAN matures, vendors and IT teams are discovering more ways to integrate SD-WAN with other technologies.
Secure remote access
Most enterprises must now support a mix of remote and in-office employees. SD-WAN integrates well with secure remote access strategies, as it helps connect distributed users securely to business resources. Some options include SD-WAN for the home and secure access service edge (SASE). SASE is a cloud-based architecture that delivers networking capabilities, like SD-WAN, and security functions as a single service.
AI and automation
Organizations can expect SD-WAN and AI integration to increase as both technologies evolve. Vendors have started to incorporate AI capabilities in their SD-WAN offerings, aiming to improve performance, monitoring and troubleshooting. For example, AI integrations can use network insights to detect false positives for intrusion prevention.
Another emerging use case is automation with SD-WAN. APIs are essential for this integration because they enable end-to-end automation across the SD-WAN and the rest of the environment, including cloud platforms. But vendors and cloud providers often use their own proprietary APIs, which complicates integration. Some SD-WAN automation capabilities include error correction and network path selection.
Wireless WAN
Wireless and cellular options have matured to the point where they can now support business initiatives. For example, SD-WAN can use 4G or 5G links as primary or backup links. In a wireless WAN, enterprises use wireless options as their primary WAN links instead of physical cables.
What are the benefits of SD-WAN?
When SD-WAN was first developed, organizations looked to the technology to reduce WAN costs. As the technology matured, however, many other compelling advantages emerged. SD-WAN offers a range of benefits to enterprises, including the following:
- Improved application performance. SD-WAN uses a combination of WAN optimization techniques and dynamically shifts traffic to accommodate each application's requirements.
- Automatic failover and redundancy. SD-WAN offers redundancy among WAN connections, automatically failing over to a second path if the primary one fails or is congested. This automatic redirection of traffic boosts application and network performance and also reduces latency.
- Reduced reliance on MPLS. SD-WAN enables organizations to depend less on expensive, leased MPLS circuits. It can send low-priority data over cheaper public internet connections and reserve private links for mission-critical or latency-sensitive application traffic, such as voice over IP.
- Automated site deployments, configurations and operations. SD-WAN uses various capabilities to enable automated processes, such as centralized controllers, ZTP and machine learning.
- Increased traffic visibility. SD-WAN enables end-to-end visibility across the network, including the local area network (LAN), WAN and cloud environments. This helps network administrators assess and troubleshoot network issues more quickly. It also provides an extra layer of security within the SD-WAN system.
What are the challenges of SD-WAN?
While the advantages of SD-WAN are plentiful, teams must also take its disadvantages into account. For instance, while SD-WAN helps decrease connectivity costs in the long term, the short-term cost of licensing SD-WAN software might be a deterrent.
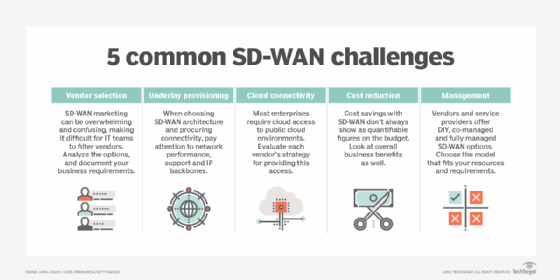
The following are some common SD-WAN challenges:
- Vendor selection.
- Underlay provisioning.
- Differing cloud connectivity strategies.
- Cost reduction complexity.
- Management.
- Training and technical skills.
Adding a layer to the WAN could introduce an opportunity for new vulnerabilities that teams must closely monitor and mitigate. Because of geographic requirements, SD-WAN often requires companies to procure connectivity from multiple providers, which could add to IT's portfolio of service contracts they must manage.
Organizations should also consider the expertise it takes to deploy and manage SD-WAN technology properly. While vendors have tried to simplify most processes surrounding SD-WAN, IT teams must still evaluate the requirements for each feature they want to roll out, as well as plans for overall security.
SD-WAN vs. traditional WAN
A traditional WAN is a geographically distributed network that interconnects multiple LANs. For decades, WANs used capabilities such as load balancing, WAN optimization, disaster recovery features and virtual private networks (VPNs) to enable connectivity and adequate network performance across multiple locations and users. Adding on these WAN capabilities, however, can be time-consuming and complex.
SD-WAN is a logical progression from the traditional WAN and its related technologies. SD-WAN architecture relies on virtual overlays that help teams change and replicate policies among distributed edge devices. As an organization grows, for example, it can use a location's existing WAN connections with an SD-WAN device, and IT can remotely manage the site policies by using the centralized controller.
SD-WAN enables real-time, automated and standardized configuration changes. This reduces the opportunity for human error that often occurs through the manual programming required by traditional WANs.
As for SD-WAN vs. VPNs, the two technologies have similarities and differences. Like VPN technology, SD-WAN securely connects remote sites to data center resources. But SD-WAN enhances this method by applying intelligent traffic routing and security policies. While VPNs typically work well for businesses with a single IP backbone, that architecture isn't reliable when introducing voice and video or when congestion impedes the network.
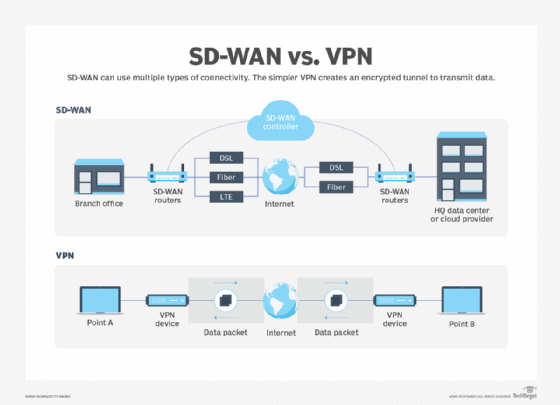
SD-WAN's granular level of support makes it far more advanced when it comes to quality of service (QoS) compared with basic internet VPNs. Also, VPNs can't always provide the internet connectivity with optimization and advanced security that cloud-based services require.
SD-WAN also takes WAN optimization one step further. WAN optimization was designed for private WAN links and focused on optimizing them for traditional traffic patterns. SD-WAN goes beyond that by applying methods such as dynamic path selection, traffic steering and application prioritization.
SD-WAN vs. MPLS
MPLS has been a trusted connectivity option for decades, providing guaranteed network performance with QoS policies that govern throughput, delay and jitter. It has the advantage of being a private connection, and MPLS providers can deliver more comprehensive service-level agreements than providers that offer connectivity over public links.
But MPLS is also expensive and somewhat inflexible. It can often take months to provision an MPLS connection and put it into operation.
Enterprise teams that opt to move from MPLS to SD-WAN should follow certain migration best practices. One step is to ask their providers for a copy of their MPLS contracts. Teams should consider items such as termination charges and minimum commitment clauses as they analyze costs and benefits. They should also order internet connections immediately due to install delays.
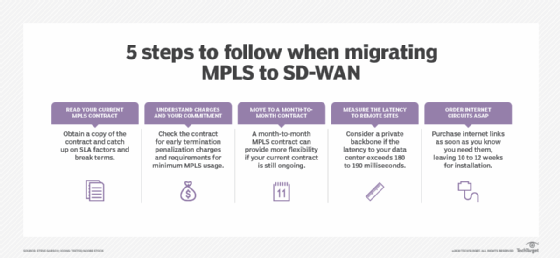
But SD-WAN architecture also enables organizations to continue using MPLS circuits along with alternate, less costly links, such as broadband or wireless. Many organizations combine multiple links to provide enough network bandwidth to transmit their applications and services. This option enables IT teams to assign business-critical traffic to a more reliable MPLS link and other traffic to a less expensive broadband link.
SDN vs. SD-WAN
SDN, or software-defined networking, is a type of architecture that uses software-based controllers and APIs to communicate with underlying hardware infrastructure and network traffic to improve network performance and monitoring. An SDN environment usually consists of three layers:
- Application layer.
- Control layer.
- Infrastructure layer.
SDN architecture is typically used in data center environments, while SD-WAN expanded the concept to WAN infrastructure. SDN adoption is prevalent among hyperscale companies and cloud providers, while small and medium-sized businesses use SDN for increased visibility and efficiency.
SD-WAN security
While security is not touted as a main reason to adopt SD-WAN, vendors and providers have addressed some security concerns by supporting IPsec standards that authenticate network traffic. Many SD-WAN providers have also partnered with security vendors to integrate protection into their products. Organizations should find out the specifics of the SD-WAN provider's security strategy and ensure it aligns with business needs.
Microsegmentation is an essential component of SD-WAN security. This method enables enterprises to isolate, prioritize and assign network traffic. If traffic from an unknown device requests access to the network, IT can assign network policies to automatically route that traffic through security tools first. Also, IT staff can organize high-priority traffic so it always travels on a specific link.
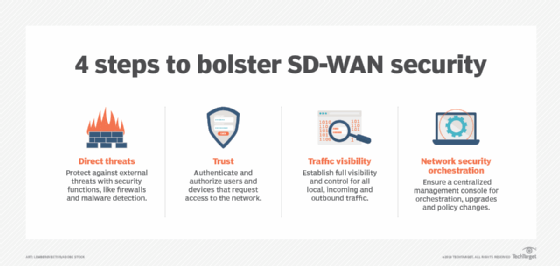
Organizations also want processes with which they can safely integrate new devices into the SD-WAN to prevent rogue devices from gaining access to their WAN traffic. Other security capabilities within SD-WAN infrastructure include data plane encryption and control plane encryption.
Increasingly, enterprises seek to integrate SD-WAN with zero-trust security, ensuring that only authorized users and devices can access specific applications. Many SD-WAN vendors partner with security vendors for this integration. SASE architecture also includes SD-WAN and zero-trust capabilities -- along with other networking and security features -- for a more comprehensive security approach.
How to buy SD-WAN
Buying SD-WAN requires a significant amount of research and preparation. Before committing to an SD-WAN vendor, teams should conduct some prepurchase steps.

Experts recommend that teams work with a proof of concept and encourage staff to experiment with the new technology, whether through SD-WAN labs or testing. In this process, teams should recognize how what they need compares with what the vendor wants to sell. An SD-WAN request for proposal (RFP) can provide crucial information about required features, vendor specialties and deployment considerations.
Another predeployment step is aligning organizational business goals with SD-WAN's capabilities. Technology teams should be ready to explain to their executives why SD-WAN is a good investment if the network is already performing well.
Overall, organizations should have a comprehensive understanding of the following factors before conducting a more in-depth vendor evaluation:
- Supported applications.
- Available connectivity options.
- Bandwidth consumption.
- Security and compliance policies.
- QoS and quality of experience needs.
- Site requirements.
SD-WAN market and providers
After an organization has compiled its prepurchase research, it can then evaluate SD-WAN vendors. The SD-WAN market is rife with vendors and providers offering variations of the technology.
Many incumbent networking vendors acquired SD-WAN startups and have integrated the technology into their broader portfolios. As the market has evolved, many SD-WAN vendors have positioned themselves as SASE vendors because SD-WAN is an important component of SASE architecture. Likewise, security vendors have started integrating SD-WAN capabilities into their offerings.
With so many vendor options, it can be complicated for network teams to evaluate each vendor's offering. This SD-WAN vendor comparison chart helps organizations of all sizes determine which services fit their RFP requirements.
SD-WAN vendors include the following, listed alphabetically:
- Cato Networks.
- Cisco.
- Cradlepoint.
- Fortinet.
- HPE Aruba.
- Juniper Networks.
- Palo Alto Networks.
- Versa Networks.
- VMware.
Most SD-WAN vendors also have an extensive list of managed service provider (MSP) partners that offer their services as managed SD-WAN. Organizations considering managed SD-WAN should ask their prospective vendors about these partnerships or reach out to their preferred MSPs.
How to deploy SD-WAN
Once enterprises have evaluated their network and business requirements, they must decide which deployment model they want to implement.
Enterprises can choose from the following SD-WAN deployment models:
- DIY. An organization buys the SD-WAN directly from a vendor, and the organization's IT team deploys and manages the system on its own.
- Fully managed. An organization outsources all facets of SD-WAN deployment and management to an MSP.
- Co-managed or hybrid. An organization is responsible for some areas of SD-WAN management and outsources other aspects to an MSP.
Much of managed SD-WAN's allure lies in an organization's ability to make an MSP responsible for acquiring internet links and technical support. But the choice of SD-WAN deployment is largely dependent on the size of an organization and the skill set of its IT team.
Once an organization has settled on a deployment model and vendor, it's time to prepare the network infrastructure for implementation. One step is to examine the existing network and determine if the hardware can support SD-WAN or if it requires upgrades or new equipment. Some companies might need to buy hardware-based appliances or virtual server software.
Most vendors support ZTP, which automatically recognizes and configures an SD-WAN device once the IT team has connected the device to a WAN connection. In some cases, however, vendors might have low-touch provisioning, which requires more hands-on interaction from the IT team.
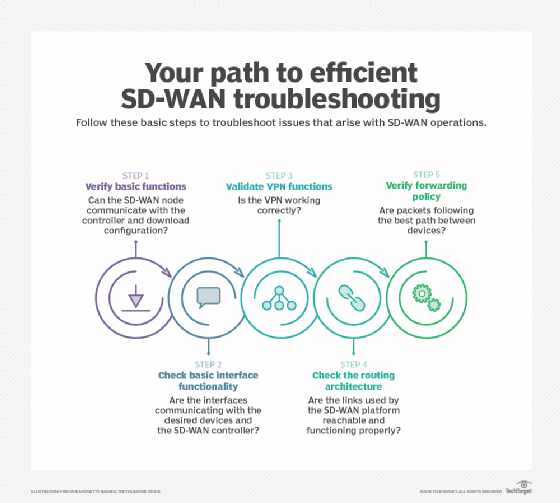
For post-deployment processes, it's important for network teams to develop a troubleshooting and monitoring strategy. Networking teams need to account for event handling, active path testing, physical status and topology, all of which are essential for troubleshooting.
The future of SD-WAN
SD-WAN presents compelling benefits for organizations looking for improved application performance and WAN redundancy. IT professionals should evaluate whether SD-WAN makes sense in their corporate network setting.
SD-WAN technology pairs well with the internet of things (IoT). It can intelligently streamline communications from distributed IoT edge devices to a centralized data center. It also helps provide the real-time visibility network teams need to manage IoT devices.
SD-WAN and 5G also perform well together. With lower latency than 4G wireless, 5G helps create faster and better connections and can reach areas that currently don't have wireless access. SD-WAN can use 5G as a primary or secondary link, replacing or augmenting wired connections.
SD-WAN technology continues to evolve and merge with SASE architecture. Some organizations might stick with SD-WAN alone while they prepare for a more comprehensive cloud-based security strategy with SASE. Others might choose to use SD-WAN as a launchpad to SASE implementation.
Meanwhile, enterprises more focused on security might consider security service edge (SSE), which is a subset of SASE. SSE focuses less on network access and more on security capabilities, such as zero-trust network access, secure web gateway, cloud access security broker and firewall as a service.
SD-WAN FAQs
- Why is SD-WAN important? SD-WAN is an evolution from traditional WAN operations. It offers enterprises flexibility in choosing network connections and boosts application performance based on intelligent routing and business requirements. Its centralized management also improves WAN management and visibility.
- Will SD-WAN replace MPLS? SD-WAN can use MPLS as a primary or backup connection, along with other options such as fiber optics, 5G and Wi-Fi. But enterprises can also opt to replace more expensive MPLS circuits with cheaper connections, as SD-WAN supports routing policies that optimize traffic based on a path's availability and efficiency.
- Is SD-WAN secure? SD-WAN prioritizes network efficiency and bandwidth optimization rather than comprehensive security. SD-WAN architecture uses microsegmentation and encryption to protect the network and its traffic, but many SD-WAN vendors partner with security vendors for additional firewall and zero trust capabilities.
- Can SD-WAN save money? Different deployment and licensing models affect the overall cost of SD-WAN. For example, enterprises might have high upfront expenses for SD-WAN appliances or require advanced features on higher licensing tiers. But SD-WAN can help create cost efficiencies in the long run, because it optimizes network reliability and performance, which improves bandwidth consumption and reduces Opex. It can also use cheaper connectivity options than traditional MPLS links.
Editor's note: This definition was updated to improve the reader experience and to reflect industry changes. Alissa Irei and Sandra Gittlen contributed to this definition.
Jennifer English is executive editor for TechTarget's Networking and Cloud sites. She joined TechTarget as a writer and editor after graduating from the University of New Hampshire in 2016.