
Jag_cz - stock.adobe.com
How to avoid internet black holes for the network
Black holes in the network disrupt connectivity and compromise data integrity. Network monitoring, team collaboration and routing optimization help minimize the negative effects.
A black hole is a region in space that has a strong gravitational force such that matter, including light, cannot escape its pull. Once something enters a black hole, return is impossible. An internet black hole is a similar concept in networking -- a cyber void silently captures incoming or outgoing data packets. The lost data packets do not reach the target recipient or return to the sender with a rejection response, becoming untraceable.
Unwanted internet black holes degrade network performance and result in loss of information. In contrast, enterprises might create intentional black holes in the network to perform emergency maintenance, control traffic, improve efficiency or offer high-level security.
Causes of internet black holes
The result of an internet black hole is similar to that of a dropped data packet. Here are some common examples and causes of black holes in networking.
Routing anomalies
Data packet loss in an internet black hole occurs on a routing level. A routing black hole could be caused by the following:
- Misconfigured routers.
- Routing table errors.
- Dead IP addresses.
- Fake paths created by hackers.
The routing path that leads to an internet black hole is called a null route or black hole route. After nondelivery and packet loss, routing paths might become unstable and asymmetric and start to flap.
Invalid or dead IP addresses
Invalid or dead IP addresses are IP addresses that are no longer in use, do not exist or have a false combination of characters. Routing tables and DNS records in network configuration can sometimes contain dead IP addresses. When packets are undelivered to dead IP addresses, ICMP rejection responses aren't sent to the sender. Thus, the lost packets degrade into an internet black hole.
Firewall functionality

The choice of firewalls can create internet black holes in a secured user network. It is common practice for firewalls to block certain connections. Some firewalls decline packets from other networks and websites without responding to ICMP requests. These firewalls are said to be on stealth ports. The packets get lost in the void with no acknowledgment to the user.
Malicious attacks
An internet black hole is not always a limitation of a networking component. Hackers can intentionally create internet black holes by faking routing routes to drive traffic toward an untraceable location of their choice. A black hole attack is a procedure in which a fake node pretends to offer the shortest path from source to destination. Hackers send a false acknowledgment to the sender before the actual destination node sends the reply.
Hardware failure
The unintentional failure of firmware or network devices, such as switches, routers and client devices, triggers an internet black hole in the network. For example, routers sometimes automatically delete messages before sending them to the destination host. The hardware failure is either temporary or permanent, depending upon the functioning of electronic components. Replacing, upgrading or updating the faulty network device to the latest version eliminates the black hole in the network.
Environmental interference
Data packets are susceptible to interference and weather conditions. If either the source or destination host is present in extreme weather, packet loss will likely occur. In some cases, weather conditions create black holes in which a packet clears the environmental interference at the sender's location but never reaches the intended destination.
Remote areas
Areas with difficult topography, such as water bodies, deserts, mountains and snowy grounds, frequently deal with internet black holes. These areas also include underdeveloped or rural places with fewer internet-connected devices due to lack of internet availability. The choice of operator can also create black holes because low-speed networks are prone to failed packet delivery.
Effects of internet black holes
While some enterprises might create intentional black holes in their network to defend against malicious attacks, unintentional black holes can have negative consequences.
Data integrity
Internet black holes reduce the data integrity of an enterprise. In addition to undelivered packets, the sender is uninformed about nondelivery. Any scheduled tasks based on the information from lost packets do not take place.
Network performance
Internet black holes result in an unreliable internet connection, downtime, service disruption and miscommunication. Dada packet loss causes the packet delivery ratio (PDR) from the original source to the destination to decrease. A low PDR indicates poor network performance and reduced efficiency.
Latency
Internet black holes cause latency in the network, slowing down the internet connection. Once the intended destination verifies that information was never received through an ICMP response, the sender initiates packet retransmission through a different route.
Strategies to deal with internet black holes
Despite the prevalence of black holes in networking, enterprises can implement various steps and processes to decrease the likelihood of experiencing one.
Network monitoring
Continuous network monitoring to detect unusual traffic patterns, PDF, routing tables and loops, and anomalous behaviors is key to mitigating internet black holes. Regular network monitoring, testing and verification require advanced tools that immediately alert administrators in the event of an anomaly. Admins can also prevent the formation of black holes at the hardware level by checking, updating and replacing network devices.
Routing optimization
Routing errors hold dead addresses and are a major source of black holes forming in the network. Identify null routes and misconfiguration to directly detect black holes. Even on a hardware level, a router can fail to accept and forward incoming traffic. Continuous routing table updates, optimization, filtering, monitoring and control are critical to form accurate routing paths between the server source and destination host.
ICMP policies
ICMP showcases communication errors and sends status messages to the sender in the network. An internet black hole won't send a defined ICMP message, and it results in packet loss. For example, imagine a sender issues an ICMP ping request to the destination address. An unresponsive host indicates the presence of a black hole in the network. Enterprise should opt to update policies to implement ICMP requests and responses during packet loss and downtime.
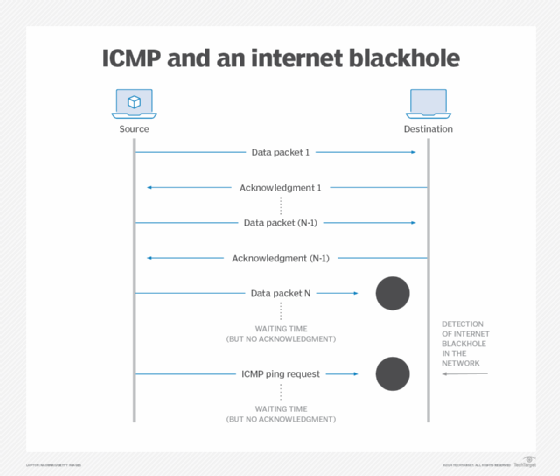
Timeout connections
One-way connections are prone to internet black holes and miscommunication in enterprises. The presence of timeout connections in network infrastructure reduces the effect of internet black holes. A timeout establishes a connection with repeated acknowledgment from the destination host. Implementing timeout connections doesn't mean black holes can't penetrate the enterprise network. However, timeout connections can detect early-stage black holes and help network administrators eliminate them in a timely manner.
Traffic control
Sometimes enterprises mitigate the unwanted effects of internet black holes by using them to control large volumes of traffic. For example, admins might opt to silently drop data packets from unwanted channels while maintaining interorganizational data integrity and reliability. Or they might drop spam messages from external users. Another traffic control use case is to perform emergency maintenance with the help of internet black holes.
Safety from DDoS attacks
Administrators can use the benefits of internet black holes to deal with DDoS attacks. In one case, admins might intentionally redirect traffic to black holes to protect information from the attacker and allow access to only a controlled part of the enterprise network infrastructure. Another option is to discard incoming traffic via a null route before traffic reaches the internal network.
Security
Government offices, special forces, documentation hubs, large organizations and VIP homes might implement proprietary or private firewalls and ultrasecure encryption methods to safeguard classified information. Such high levels of secure communications allow only registered users and devices on record to exchange information. These firewalls maintain security and data encryption by dropping incoming traffic from suspicious sources and unauthorized devices.
Interorganizational efforts
Mitigating black holes in an enterprise requires collaborative input from network and security teams. These teams should share insights to stay informed and regulate network reliability and security. Implement cross-functional team meetings for policy alignment, planning, monitoring and audits. Deploying strong security protocols and ciphers on network devices helps eliminate the chances of misconfiguration and unwanted routing paths.
Venus Kohli is an electronics and telecommunications engineer, having completed her engineering degree from Bharati Vidyapeeth College of Engineering at Mumbai University in 2019. Kohli works as a technical writer for electronics, electrical, networking and various other technological categories.







