
stock.adobe.com
How zero-trust SDP can work with a VPN for remote work
Implementing software-defined perimeter and zero-trust security models with a corporate VPN adds significant layers of user and device verification and authentication.
Businesses have used VPNs for decades to establish secure, encrypted remote communications services. As cyberthreats increase in frequency and sophistication, however, VPNs don't necessarily provide the most secure environment to remotely access an internal network and its associated systems.
Establishing a truly secure and nonporous perimeter is a top priority for network engineers and managers today and for the foreseeable future. Existing technologies, such as firewalls and intrusion prevention systems, provide good protection from malware and cybercriminals. However, their design still allows skilled intruders to bypass the existing perimeter protection and access internal networks.
What is needed is something that establishes an impenetrable barrier around internal networks and makes it virtually impossible for threat actors to breach the perimeter. One of these technologies is a software-defined perimeter (SDP), and the other is a zero-trust environment to prevent unauthorized access and enhance authentication measures.
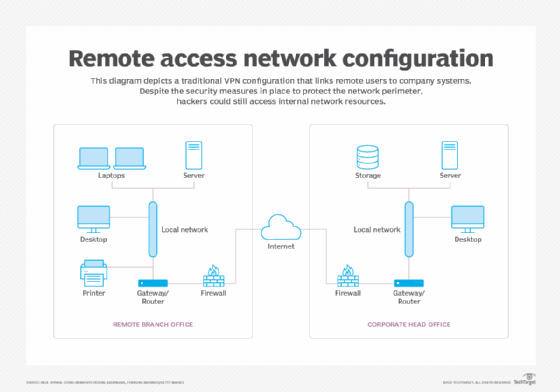
Figure 1 depicts a traditional network where a VPN is configured to link remote users into a headquarters' systems and resources. Despite the measures in place to protect the perimeter, it's still possible to get past existing security and access internal networks and resources.
By contrast, an SDP establishes a virtual boundary or wall around IT resources at the network layer, as opposed to the application layer. The SDP authenticates the requesting user and verifies the status of the device being used before it permits access to an internal network.
The process begins by the SDP authenticating both the user and device. It then establishes a single network connection between the user's device and the resources it's trying to access, such as a server. The network connection is unique and cannot be used by anyone else. The user is granted access only to services for which they have been approved.
One way to visualize the SDP process is getting access to a car that's in a garage. First, the garage door must be opened, typically with a key. If the garage is a large, multivehicle facility, it may be necessary to use a proximity card or enter a code into a keypad to gain access.
Next, once the car has been reached, a process for accessing the car must be performed. Today's cars usually have a remote access feature that uses a fob that connects to the car using radio transmission to unlock the doors with a unique code. In this example, accessing the car requires multiple layers of verification and authentication.
Figure 2 depicts a network that uses an SDP with zero trust to protect internal networks and resources. Zero trust is an approach to security that presumes no user, device or network is trustworthy. It is a rigorous approach to security, and SDPs are effective options for ensuring zero trust.
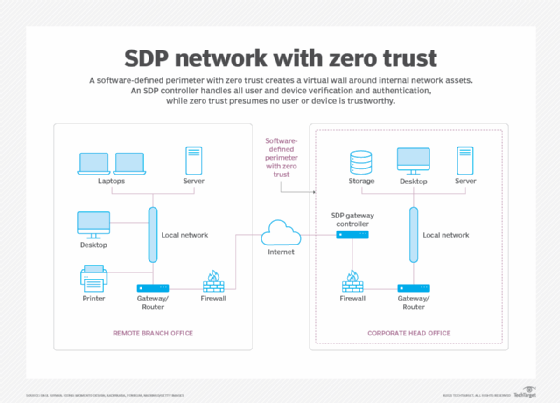
In this example, an SDP controller manages all user and device verification and authentication activities before permitting a connection to be established with the internal network and IT resources. The SDP, in effect, provides a wall around the internal network assets, preventing all access attempts except those that have been fully authenticated.
Benefits of SDP with zero trust
The principal benefit of an SDP with a zero-trust policy is it blocks any attempts to access internal network resources without proper authentication. Aside from that, SDPs can supplement VPNs by adding an additional layer of protection to the VPNs. Adding zero trust to that model ensures the SDP is providing a completely secure and impenetrable barrier to any unauthorized access attempts.
How does an SDP work?
In the course of its work, an SDP performs several activities. The following lists the key SDP activities:
- Verification of user identities. This can be done with traditional user ID and password authentication. But multifactor authentication may also be implemented to provide additional challenges to access attempts.
- Device inspection and verification. SDP also examines the requesting device to see if its software is at the correct level, no malware is present and other examinations. A list of unauthorized devices may be developed to further restrict access.
- SDP controller and gateway. An SDP controller handles all authentication activities as established by the organization. Once a request has been approved, the user is routed to an internal SDP gateway that establishes the actual connection.
- Secure network connection. Once the above steps have been completed, the SDP gateway establishes a unique, secure network link to the requesting user and then to the services that the user is authorized to use.
- User access to an encrypted connection. Once the SDP gateway establishes the encrypted link between the user and requested resources, the user accesses approved services.
Integrating SDPs and VPNs
Depending on the existing network perimeter configuration, SDPs can add value to VPNs by providing additional security and protection from unauthorized access. SDPs can work in standalone mode in lieu of VPNs or augment them, depending on the network and its security posture.
Adding zero trust to the overall security methodology ensures that anyone wishing to use the company's resources -- whether internal or external users -- is deemed untrustworthy. A zero-trust mindset will result in greater security and prevention of cyberthreats and other malware.








