
Getty Images
Comparing network segmentation vs. microsegmentation
Network segmentation and microsegmentation both control access but vary in how they do it, as well as how granular their approach is. Learn the differences here.
It's not uncommon for security and networking professionals to be confused when comparing network segmentation vs. microsegmentation. While both architecture strategies control access between systems and devices on a corporate network, the methods each technique uses to restrict that access differ significantly.
What is network segmentation?
Network segmentation, the older of the two strategies, can be physical, virtual or both. It relies on both hardware- and software-based methods to divide a network into multiple segments known as subnetworks or subnets. Once created, access controls restrict intersubnetwork communication and determine which users, services and devices can interconnect.
Security policies, allowlists, access control lists, firewalls and virtual LANs (VLANs) provide network segmentation functionality.
Traditional network segmentation limits north-south network traffic at the network level. In general, network segmentation is used over larger network segments and has broad policies.
What is microsegmentation?
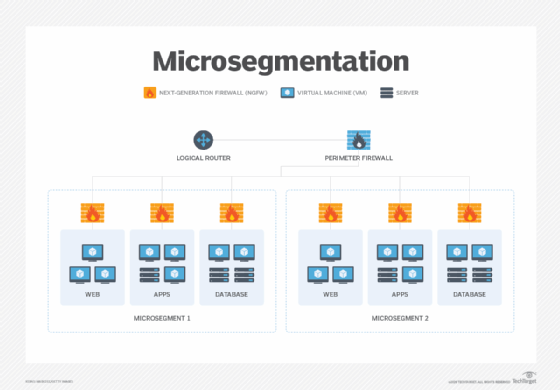
Microsegmentation, which descends from network segmentation, takes a modern and far more granular approach to access and security controls and attack surface reduction. Unlike network segmentation, which depends on a single constraint to govern access, microsegmentation restricts access to any and all devices, endpoints and applications, regardless of the VLAN they are on.
Microsegmentation uses software-defined network security tools, such as Layer 7 firewalls and intrusion protection and intrusion detection systems, as well as network detection and response sensors placed through agent software installed on each server or directly onto each individual hypervisor in a data center.
By disaggregating these network tools and putting them as close as possible to the application or service in question, enterprises can put into place the precise level of access control and cybersecurity protection each application or service requires.
Microsegmentation, which uses granular policies, limits east-west traffic at the workload level.
Network segmentation vs. microsegmentation
To fully understand the scope and differences of network segmentation vs. microsegmentation, let's take a look at them in action.
In network segmentation, a network administrator creates a separate VLAN on a switch that hosts business-critical applications. Devices that need to communicate with these applications are placed onto a separate VLAN -- or subnetwork. Because inter-VLAN communication requires devices be routed through their respective Layer 3 gateways, a firewall can be positioned between the subnetworks to act as both the gateway between VLANs and a way to permit or deny specific access between the different subnetworks.
While network segmentation can restrict access between VLANs, it has no ability to restrict server-to-server access within a VLAN. That's because all application servers are located on the same subnetwork. Add in microsegmentation and administrators can restrict north-south traffic, as well as east-west traffic. This is a benefit for businesses working toward a zero-trust security strategy because microsegmentation prohibits lateral movement by attackers if a data breach occurs.








