
The risks and effects of spyware
Spyware can steal mundane information, track a user's every move and everything in between. Read up on the types of spyware and how to best fix infected devices.
Spyware is a type of malware that steals sensitive information from unknowing users. The effects of spyware range from gathering usage habits for marketing purposes to targeted attacks by nation-states against political activists. More advanced spyware will be silently installed on a system, but spyware is often disguised as a legitimate piece of software or browser extension -- a Trojan -- in order to infect a device.
Spyware uses a device's resources to continually track activities and record data and then sends this data to remote servers. The complexity of spyware depends on the aims of the attack:
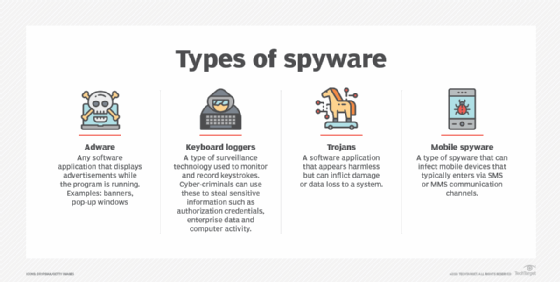
- Adware and tracking cookies track browser activities, including searches, history and downloads. This data may be used to inject malicious ads or be sold to a third party. While this category applies to malicious software, it can also pertain to legitimate software or browser extensions that gather information without user consent.
- Keyloggers record keystrokes to gather sensitive information, as well as mundane data. They can be used by employers to track employee activities, by law enforcement investigating criminal activity or by threat actors to steal credentials, credit card numbers or other personally identifiable information (PII).
- Information stealers are a type of spyware that retrieves more targeted data. For example, information stealers will track which applications or websites are being used and will extract PII or login credentials directly, rather than capturing that information as it is typed. Information stealers can also pilfer documents and media files.
- Banking trojans, like Kronos or Emotet, are an even more targeted variety of spyware used to attack banking institutions and steal sensitive information processed by those systems.
- System monitors are the most advanced form of spyware and are sometimes used by law enforcement or nation-states. This software tracks browsing habits, app usage and keystrokes like other forms of spyware but can also capture audio and video from a device's microphone and camera, as well as GPS location data. The most advanced system monitor spyware -- such as NSO Group's Pegasus -- can even record conversations from end-to-end encrypted messaging systems, like iMessage, WhatsApp or Signal.
How spyware affects your device
While spyware has historically been known for slowing down computers, the slowdown effect is harder to notice as computers and mobile devices get more powerful.
Other signs that could indicate a device has been infected by spyware include the following:
- It is running unusually slow or lags while performing specific activities.
- The browser's homepage has been changed, or new browser extensions have been installed without user action.
- Antispyware and antimalware programsaren't working correctly.
- A device is making connections to known malicious servers.
- The camera or microphone on a device is turned on without user action.
It is important to note that spyware is not necessarily designed to be efficient. Errors in the malicious software can cause system or program crashes -- another telltale sign of spyware.
How to remove spyware
Fortunately, many of today's security tools can detect anomalous network connections and uncover spyware. If a PC has been infected, installing an antispyware or antimalware program from vendors such as Citrix, Bitdefender, Kaspersky, Sophos, Trend Micro or Malwarebytes can detect and remove known spyware and protect it against other potentially unwanted software. Note, more advanced spyware may attempt to disable security tools to avoid detection, so it is wise to occasionally check to ensure security tools are working properly.
Removing spyware from a mobile device can be more difficult depending on how deeply embedded into the system the spyware is. Often, the only option is to perform a factory reset and reinstall the mobile OS from a clean system image.






