What is quantum key distribution (QKD)?
Quantum key distribution (QKD) is a secure communication method for exchanging encryption keys only known between shared parties. It uses properties found in quantum physics to exchange cryptographic keys in a provable and secure way.
QKD enables two parties to produce and share a key that is used to encrypt and decrypt messages. Specifically, QKD is the method of distributing the key between parties.
Key distribution on a conventional scale relies on public key ciphers, which use complicated mathematical calculations and require a prohibitive amount of processing power to break. The viability of public key ciphers, however, faces several issues, such as the constant implementation of new strategies to attack these systems, weak random number generators and general advances in computing power. In addition, quantum computing will render most of today's public key encryption strategies unsafe.
QKD is different from conventional key distribution because it uses a quantum system that relies on basic and fundamental laws of nature to protect the data, rather than relying on mathematics. For example, the no-cloning theorem states that it is impossible to create identical copies of an unknown quantum state, which prevents attackers from simply copying the data in the same manner that they can copy network traffic today.
Additionally, if an attacker disturbs or looks at the system, the system changes in such a way that the intended parties involved know. This is a process that is not vulnerable to increased processing power.
How does quantum key distribution work?
QKD works by transmitting many light particles, or photons, over fiber optic cables between parties. Each photon has a random quantum state, and collectively, the photons sent make up a stream of ones and zeros. This stream of ones and zeros are called qubits -- the equivalent of bits in a binary system.
When a photon reaches its receiving end, it travels through a beam splitter, which forces the photon to randomly take one path or another into a photon collector. The receiver then responds to the original sender with data regarding the sequence of the photons sent, and the sender then compares that with the emitter that sent each photon.
Photons in the wrong beam collector are discarded; what's left is a specific sequence of bits. This bit sequence can then be used as a key to encrypt data. Any errors and data leakage are removed during a phase of error correction and other postprocessing steps. Delayed privacy amplification is another postprocessing step that removes any information an eavesdropper might have gained about the final secret key.
Types of quantum key distribution
There are many different types of QKD, but the two main categories are prepare-and-measure protocols and entanglement-based protocols:
- Prepare-and-measure protocols focus on measuring unknown quantum states. They can be used to detect eavesdropping and determine the amount of data that was potentially intercepted.
- Entanglement-based protocols focus on quantum states in which two objects are linked together, forming a combined quantum state. The concept of entanglement means that the measurement of one object thereby affects the other. If an eavesdropper accesses a previously trusted node and changes something, the other involved parties know.
By implementing quantum entanglement or quantum superpositions, the process of trying to observe the photons changes the system, making an intrusion detectable.
Other more specific types of QKD include discrete variable QKD (DV-QKD) and continuous variable QKD (CV-QKD):
- DV-QKD encodes quantum information in variables using a photon detector to measure quantum states. An example of a DV-QKD protocol is the BB84 protocol.
- CV-QKD encodes quantum information on the amplitude and phase quadrants of a laser, sending the light to a receiver. The Silberhorn protocol uses this method.
The following are examples of QKD protocols:
- BB84.
- Silberhorn.
- Decoy state.
- KMB09.
- E91.
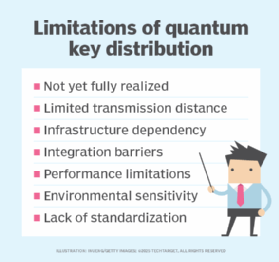
Challenges of quantum key distribution
QKD has the following three primary challenges:
- The integration of QKD systems into current infrastructure.
- The distance in which photons can travel.
- The use of QKD in the first place.
It is difficult to implement an ideal infrastructure for QKD. Although it is perfectly secure in theory, imperfections in tools such as single-photon detectors create security vulnerabilities. Therefore, it is important to consider security analysis.
Modern fiber optic cables are typically limited in how far they can carry a photon. The range is often upward of 100 kilometers (km). Some groups and organizations have managed to increase this range for the implementation of QKD. The University of Geneva and Corning Inc. worked together, for example, to construct a system capable of carrying a photon 307 km under ideal conditions. Quantum Xchange launched Phio, a QKD network in the U.S. capable of delivering quantum keys an apparent unlimited distance using a patent-pending, out-of-band delivery system called Phio Trusted Xchange.
Another challenge of QKD is that it relies on establishing a classically authenticated channel of communication. This means that one of the participating users already exchanged a symmetric key in the first place, creating a sufficient level of security.
A system can already be made sufficiently secure without QKD by using another advanced encryption standard. As the use of quantum computers becomes more frequent, however, the possibility that an attacker could use quantum computing to crack into current encryption methods rises -- making QKD more relevant.
One of the most important challenges to QKD is that it is not yet fully operational. Currently, QKD is still largely experimental and has not yet been widely adopted beyond select research and government applications. Like much of quantum computing, its current operational state is limited in terms of functionality. Existing cybersecurity solutions are not readily compatible with QKD systems, which can complicate deployment. Similarly, global standards for QKD protocols and interoperability remain under development.
Implementation examples
QKD has been worked on and implemented for a relatively long period of time. The following are some examples:
- In 2007, Los Alamos National Laboratory and the National Institute of Standards and Technology used the BB84 protocol over a 148.7 km optical fiber.
- In 2005, the University of Geneva and Corning Inc. used a fiber optic wire of 307 km.
- The University of Cambridge and Toshiba collaborated in making a high-bit-rate QKD system using the BB84 protocol.
- Peking University and Beijing University of Posts and Telecommunications collaborated on creating a QKD system.
- In 2017, the University of Science and Technology of China measured entangled photons over 1,203 km.
- China and the Institute for Quantum Optics and Quantum Information in Vienna collaborated to create a quantum channel between the two locations.
- Launched in 2004 and operated until 2007, the Defense Advanced Research Projects Agency Quantum Network was a 10-node QKD network developed by a collaboration of multiple entities, such as Boston University, Harvard University and IBM Research.
- In 2018, Quantum Xchange launched the first quantum network in the U.S., offering 1,000 km of fiber optic cable and 19 colocation centers along the Boston-to-Washington, D.C., corridor and metro hubs.
- In February 2019, the European Telecommunications Standards Institute released a standard interface for devices and applications to receive quantum keys to make QKD systems easier to deploy.
Commercial companies, such as ID Quantique, Toshiba, QuintessenceLabs and MagiQ Technologies, have also started offering commercial QKD systems. In addition, Tokyo is testing its own QKD network.
QKD attack methods
Even though QKD is secure in theory and its quantum networking framework makes hacking difficult, imperfect implementations of QKD have the potential to compromise security. Techniques for breaching QKD systems have been discovered in real-life applications. For example, even though the BB84 protocol should be secure, there is currently no way to perfectly implement it.
The phase remapping attack was devised to create a backdoor for eavesdroppers. The attack takes advantage of the fact that one party member must allow signals to enter and exit their device. This process takes advantage of methods used widely in many commercial QKD systems.
Another attack method is the photon number splitting attack. In an ideal setting, one user should be able to send one photon at a time to the other user. Most of the time, however, additional similar photons are sent. These photons could be intercepted without either party knowing. The photon number splitting attack takes advantage of this.
To combat this type of attack, an improvement to the BB84 protocol was implemented -- called decoy state QKD -- which uses a set of decoy signals mixed in with the intended BB84 signal, while enabling both parties to detect if an eavesdropper is listening.
History of quantum key distribution
QKD got its start with the first proposal of quantum cryptography in the 1970s when Stephen Wiesner at Columbia University came up with the idea of quantum conjugate coding. Wiesner's paper was published in 1983. Charles H. Bennett later introduced a concept of secure communication, basing his ideas on Wiesner's work. Bennett also came up with BB84 -- the first quantum cryptography protocol -- which worked using nonorthogonal states. In 1990, Artur Ekert discovered another method to QKD, basing his idea around quantum entanglement.
Future of quantum key distribution
Quantum key distribution is expected to play a critical role in next-generation secure communications as both quantum computing advances and cyberthreats evolve with it. Currently, satellite-based QKD is gaining attention as a viable way to overcome distance limitations, enabling global key exchange networks. Paired with post-quantum cryptography and other evolving cybersecurity solutions, QKD may become a foundational component of quantum secure infrastructure in the coming years.
The Quantum-Safe Security Working Group was formed by the Cloud Security Alliance to promote the adoption of new technologies that help quantum computing be adopted at a steady pace. New technology is being worked on to improve high data rates and increase the overall effective distance of QKD. QKD is beginning to be used more widely in a commercial setting, with new networks and companies offering commercial QKD systems.
Quantum key distribution is a technology based on quantum computing. Learn how quantum computing impacts encryption.






