SolarWinds backdoor used in nation-state cyber attacks
Nation-state hackers conducted a supply chain attack on SolarWinds and planted a backdoor in software updates issued to customers such as FireEye and various government agencies.
U.S. government agencies and security experts are urging organizations to immediately review their networks after a backdoor was discovered in a widely used IT management product from SolarWinds.
In a blog post Sunday, FireEye disclosed that the nation-state attack it suffered recently was the result of a massive supply chain attack on SolarWinds, an Austin, Texas-based software maker that specializes in both centralized and remote IT management and monitoring. FireEye said the backdoor campaign, which it called "UNC2452," allowed the threat actors to gain access to numerous government and enterprise networks across the globe.
"They gained access to victims via Trojanized updates to SolarWind's Orion IT monitoring and management software," the blog post read. "This campaign may have begun as early as spring 2020 and is currently ongoing. Post-compromise activity following this supply chain compromise has included lateral movement and data theft."
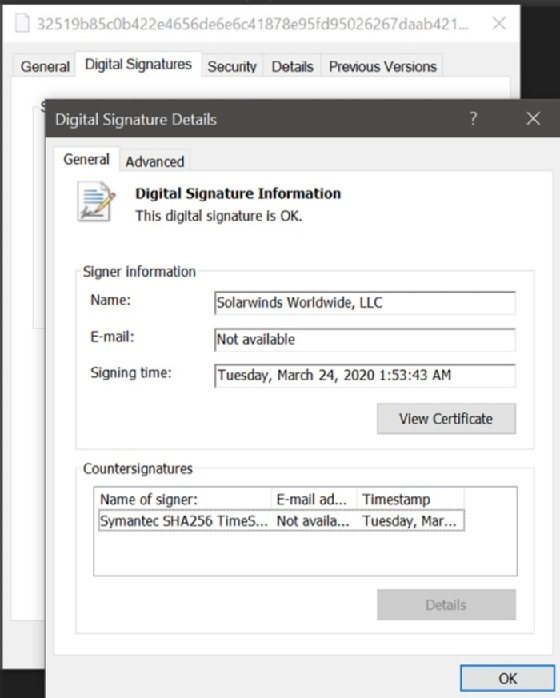
The backdoor, which FireEye identified as "Sunburst," uses a dynamic link library (DLL) component in the Orion software framework to communicate with third-party command-and-control servers outside the victim's network. The component, SolarWinds.Orion.Core.BusinessLayer.dll, is digitally signed by SolarWinds and therefore looks like a legitimate piece of the vendor's proprietary software code.
Microsoft, which also investigated the FireEye breach along with the vendor's internal security team, published security advisories Sunday regarding the SolarWinds backdoor. In one advisory, the Microsoft Security Response Center wrote that nation-state threat actors gained administrative access to several victim networks by stealing existing privileged account credentials or by forging their own credentials with compromised SAML token signing certificates.
In a separate blog post, John Lambert, an engineer at the Microsoft Threat Intelligence Center, explained the forged SAML tokens "can be used against any on-premises resources (regardless of identity system or vendor), as well as against any cloud environment (regardless of vendor) because they have been configured to trust the certificate."
In addition, Lambert said that because the forged SAML tokens are signed with a victim organization's own trusted certificates, the organization's security team might not detect the credentials as malicious.
SolarWinds issued a security advisory Sunday about the backdoor, which the vendor said affected Orion Platform versions 2019.4 HF 5 through 2020.2.1, which were released between March 2020 and June 2020. "We have been advised this attack was likely conducted by an outside nation-state and intended to be a narrow, extremely targeted and manually executed attack, as opposed to a broad, system-wide attack," the company said.
SolarWinds urged all customers to immediately upgrade to Orion Platform version 2020.2.1 HF 1. The software maker also said it expects an additional hotfix, 2020.2.1 HF 2, to be released Tuesday.
The Cybersecurity and Infrastructure Security Agency (CISA) on Sunday issued an emergency directive requiring all civilian federal agencies to "review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately."
Acting CISA Director Brandon Wales urged all the agency's partners in the public and private sectors to assess their exposure to the SolarWinds backdoor and take the necessary steps to prevent any exploitation. "The compromise of SolarWinds' Orion Network Management Products poses unacceptable risks to the security of federal networks," Wales said in a security advisory.
It's unclear how many organizations have been breached by the SolarWinds backdoor campaign. FireEye said UNC2452 activity has been detected in "multiple entities" across the globe, including government, technology and telecom organizations in North America, Europe, Asia and the Middle East.
Reuters first reported Sunday that the nation-state hackers behind the FireEye breach had also breached several U.S. government agencies, including the Treasury and Commerce departments and the National Telecommunications and Information Administration.
In a filing with the U.S. Securities and Exchange Commission (SEC), the vendor said the malicious Orion updates containing the backdoor were installed by fewer than 18,000 customers out of more than 300,000 total customers. "SolarWinds is still investigating whether, and to what extent, a vulnerability in the Orion products was successfully exploited in any of the reported attacks," the company said, referring to media reports about the attacks on FireEye and U.S. government agencies.
Both FireEye and Microsoft released indicators of compromise for UNC2452, which have already been incorporated in their respective threat detection products, to block any malicious activity.
FireEye also recommended organizations isolate and contain all SolarWinds servers while they review their networks and conduct investigations. If organizations cannot fully isolate their SolarWinds systems, FireEye encouraged customers to reduce the scope of connectivity and access so that threat actors cannot reach sensitive data. At a minimum, the vendor said, organizations should change passwords for all accounts that have access to SolarWinds systems.
In addition, Microsoft advised organizations to review and secure their SAML token signing keys and consider hardware security modules to protect their token certificates.






