cloud-native application protection platform (CNAPP)
What is cloud-native application protection platform (CNAPP)?
Cloud-native application protection platform, or CNAPP, is a software product that bundles multiple cloud security tools into one package, thereby delivering a holistic approach for securing an organization's cloud infrastructure, its cloud-native applications and its cloud workloads.
This platform brings together various security functions that -- before the arrival of CNAPP -- had been performed piecemeal via individual software products.
The various CNAPP components deliver a range of security capabilities, from monitoring, detecting and responding to vulnerabilities and threats to analyzing, automating, enabling and optimizing the organization's security policies and procedures.
CNAPP also supports IT and security working together as DevSecOps teams to incorporate security at the earliest stages of application development -- a move known as shift left. This approach arises from the belief that shifting security considerations, as well as testing, quality and performance evaluations, to earlier stages of the software development cycle creates a product that is more secure and less costly.
CNAPP's biggest benefit, according to technology and software market analysts, is that it delivers these multiple capabilities in an integrated fashion.
Because of this, CNAPP can be used in place of multiple other cloud security software products. This reduces security complexity, analysts say, while still providing the critical functions and services that security teams need to defend their organization's cloud environment and the software running in it.
Demand for consolidated cloud security tools is significant. Gartner estimated in its 2023 "Market Guide for Cloud-Native Application Protection Platforms" report that 60% of enterprises will have consolidated cloud workload protection platform (CWPP) and cloud security posture management (CSPM) capabilities to a single vendor, up from 25% in 2022.
Meanwhile, the 2023 "Cloud Native Application Protection Platform Survey Report," commissioned by Microsoft and conducted by the Cloud Security Alliance (CSA), found that 75% of organizations use CNAPPs or plan to do so.
Why you should be using CNAPP
Findings from the CSA report show that many organizations struggle with securing their cloud environments. Specifically, the report noted the following:
- Thirty-two percent of organizations have trouble prioritizing security improvements due to the overwhelming and often incorrect information they receive from alerts.
- Only 35% have integrated security into their DevOps practices -- although 51% of organizations are in the process of doing so.
- Also, 22% cite a lack of personnel as a significant challenge.
CNAPP is certainly not a panacea -- no security tool is -- but analysts believe CNAPP can deliver numerous benefits. First, it can reduce the complexity and volume of work facing security teams by giving them a single tool, instead of many, to handle a range of security requirements. Second, that simplification of security tools can save time and money, which security teams can reinvest to meet other security needs.
Analysts also say CNAPP delivers simplification of the security program without sacrificing capabilities. CNAPP offers a suite of capabilities, including automating entitlements management, risk detection and compliance. It also identifies misconfigurations, threats and bugs in code while software is in the continuous integration/continuous delivery pipeline phase.
Additionally, because it consolidates security features and functions that had been delivered by multiple software products, CNAPP provides the security team with a single view, or single pane of glass, of security risks and requirements across an organization's cloud environment -- including IaaS, PaaS and serverless workloads. This single view reduces the blind spots that develop when security teams use different tools. Furthermore, that increased visibility can help speed detection and response of security issues.
Taken together, CNAPP can help security teams boost their overall security posture.
CNAPP components and capabilities
Although functions and features vary from one vendor to the next, CNAPPs typically bring together components that deliver a range of capabilities, such as the following:
- CSPM, which is used to identify misconfigurations and compliance risks in the cloud and which monitors cloud infrastructure for gaps in security policy enforcement. CSPMs also provide automated threat detection and remediation across the various cloud resources, including an organization's IaaS, PaaS and SaaS systems. CSPMs also automate enforcement of an organization's security policies and compliance frameworks.
- CWPP, which supports security in a multi-cloud environment and supports a cloud environment that has public, private and hybrid cloud platforms. CWPPs discover workloads in the enterprise and scan them for security problems. They also offer additional functions, such as runtime protection and network segmentation.
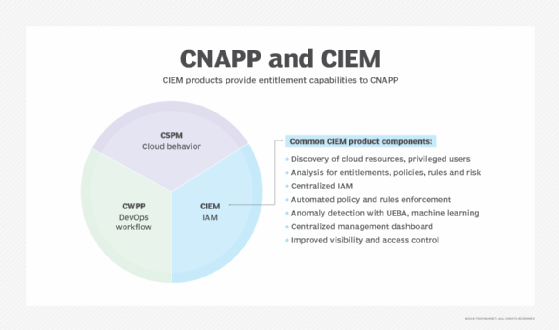
- Cloud infrastructure entitlement management (CIEM) software, which supports and automates an organization's entitlement management program. CIEM identifies and reports which users have permission to access which parts of the organization's cloud infrastructure. CIEM ensures that users, whether human or machine, can access only the cloud infrastructure that they need to perform their tasks -- an approach known as the principle of least privilege. As such, CIEM is a component of an organization's identity and access management (IAM) program and enables a zero-trust security approach.
- Cloud service network security is delivered via web application firewalls, web application and API protection, distributed denial-of-service attack protection, load balancing and transport layer security examination, among other capabilities. These all help detect threats and defend against them in the dynamic network perimeters that exist in enterprise cloud environments.
- Additional capabilities that can come from CNAPP include segmentation, infrastructure-as-code scanning, AI-powered automation of rules application and enforcement, and Kubernetes security posture management.
Alternatives to CNAPP for cloud security
Security analysts and researchers as well as enterprise security leaders and advisors generally agree on the need for a comprehensive, integrated approach to security, whether for on-premises IT or cloud resources. They also advocate for applying automation and intelligence as much as possible, to reduce human error and mistakes as well as to increase compliance, speed and response. Many promote the use of CNAPP over the use of disparate security tools.
Even so, organizations should recognize the potential challenges of CNAPP implementation. CNAPP products offer varying capabilities, and some have strengths that others do not. The CNAPP market is still maturing.
Some organizations may determine that the cloud security tools already in place provide adequate protection or that they do not have a large enough or complex enough environment to justify shifting from existing cloud security products to a new platform. Still, many security experts point to CNAPP as the stronger choice for defending and protecting enterprise cloud environments.
Mary K. Pratt is an award-winning freelance journalist with a focus on covering enterprise IT and cybersecurity management.








