
kras99 - stock.adobe.com
The top secure software development frameworks
Keeping security top of mind when developing software is paramount. Learn how to incorporate security into the SDLC with the top secure software development frameworks.
Advances in computer technology have prompted the development of frameworks that address security and user requirements in the software development lifecycle.
This article examines several established SDLC frameworks, as well as two frameworks that specifically incorporate risk and security elements. With growing cybersecurity threats, organizations must design and upgrade software applications with security in mind, while still providing users the high performance levels they expect.
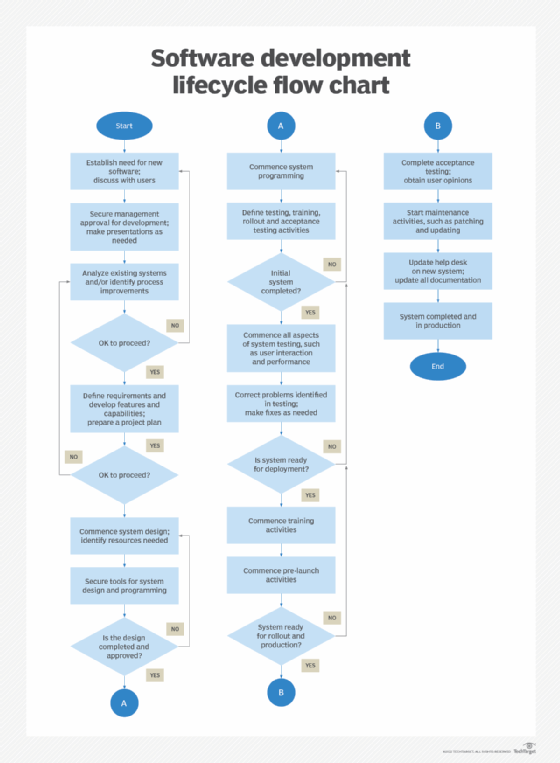
Steps in the SDLC
Due to the unique nature of software development, the SDLC process is far from straightforward and, as shown in the flow chart below, includes many loops. These loops help ensure issues are thoroughly checked and verified before software is deployed. Document each step and supporting activities carefully, as those documents will be used throughout the development, testing, training and deployment phases and may be used as evidence for audits.
The seven steps of the SDLC are the following:
- Analysis. In this step, the current system or process is analyzed, deficiencies are identified, and desired operating parameters and results are defined. Interviews should be conducted with primary users of the new app, as well as senior leaders whose approval is needed. During this step, developers should prepare a presentation for senior IT and company leadership to ensure they support the project.
Note: Secure management approval and funding before proceeding with the SDLC process. - Plans and requirements. Once the project is approved, define the new system's features and capabilities. A project plan should be created at this stage, and developers should clearly state how previous deficiencies will be addressed in the new system. If a spreadsheet or project management software is used, build out the project plan, including subactivities within each major step.
- Design. Begin developing the system design, including elements such as hardware, OSes, specialized utilities, I/O, software development tools, communications, security, programming, testing and deployment. Additional activities include project kickoff, operating procedures and related documents, system specifications and potential end-of-project life planning.
- Development. During this phase, program designs using internal software teams, external teams as needed, software development tools and other aids. Issues, such as initial testing, user training, deployment, acceptance testing and management approval, should be defined and documented.
- Testing. Once the initial system is completed, it should undergo a variety of tests to validate its performance, user ease of interaction, communications capabilities and security attributes. Correct any issues that arise from testing. Tests should also be conducted on the corrections. Involve QA teams in this stage as well.
- Deployment. Earlier in the design phase, develop a deployment schedule. Depending on the complexity, the system may need a phased rollout, as opposed to a single launch. This provides users the opportunity to get comfortable with the system in a "safe" environment. The existing system might have to be run in parallel with the new one to facilitate the transition.
During this step, training programs and documentation should be developed for primary and alternate users. It may be useful to set up a training with several workstations connected to both systems. This enables users to see the differences between the old and new system. - Post-deployment maintenance. Once the system enters this stage, it shifts into maintenance mode. Regularly monitor the new system's performance. Necessary updates should be made during this stage without causing serious production disruptions. Establish a patching schedule, along with schedules for system shutdowns for maintenance, updates to hardware, and cybersecurity and disaster recovery activities.
The following flow chart demonstrates how the SDLC process helps ensure performance issues are addressed before a system is put into production.
Software development frameworks
Many software development frameworks have been created over the years; the following is a partial list. Each approach can be adapted to incorporate security issues in the development process:
- The Waterfall model, originally developed in 1970, espouses a linear, logical progression of activities, similar to the original SDLC model.
- Rapid application development, designed for speed, uses more iterative and adaptive techniques and prototyping for software development.
- Joint application development engages users more proactively at most phases of the development process, with the intent of improving their satisfaction with the result.
- The Fountain model is used to develop object-oriented software and uses iterative and incremental development processes.
- The spiral model is favored for development of large, complex and costly projects. It builds risk management and iterative processes into the framework.
- Agile, one of the most popular frameworks in use today, focuses on developing smaller pieces of the final software product rather than building the entire system.
- Lean software development, a variant of Agile, is noted for its flexibility and lack of strict rules. It actively engages users at all stages of the development process and gathers team members into small working groups for greater interaction.
- Scrum, another Agile variant, is typically used by project managers to administer iterative and incremental activities.
Open source development tools
In addition to manually developing software systems, open source applications can help facilitate the development process. The following is a partial list of open source frameworks for development:
- Spring Boot is designed for Java programming. It simplifies the coding process by providing easy-to-use, pre-written code.
- Django is similar to Spring Boot in terms of functionality but is used for programming in Python.
- Angular uses a template approach to web application design.
- Vue is another JavaScript application development tool.
- Apache Cordova facilitates the development process by creating multiple deployment environments, each of which uses a single codebase.
- React Native is used for mobile application development.
Purpose-built secure software development frameworks
The aforementioned software development frameworks and models can be adapted to incorporate security provisions, but they're not inherently designed for security.
The following two SDLC frameworks take the current approach to software design to a higher level by incorporating risk and security elements.
BSA Framework for Secure Software
Developed by BSA | The Software Alliance and released in 2019, the BSA Framework for Secure Software is a risk-based and security-focused tool software developers, vendors and users can use to examine and analyze how software will perform in specific security situations. Software products and services are the primary focus of the framework, as opposed to traditional SDLC-type models and frameworks. What makes the framework unique is how it helps users ensure that security is factored into the development process and that the software, as written, produces the desired security capabilities and outcomes.
The framework's risk-based approach helps users and stakeholders identify specific security parameters required by their organization. BSA's framework is composed of a detailed matrix of the following:
- Functions are the highest-level activities in the framework. They include the following:
- Secure development addresses all aspects and phases of the software development and deployment process.
- Secure capabilities define key security characteristics and capabilities for a software product.
- Secure lifecycle ensures security is maintained from the initial development of a product through to its end of life.
- Categories define the major activities and capabilities of a function.
- Subcategories divide categories into additional areas of consideration.
- Diagnostic statements provide descriptive outcomes of categories and subcategories and are to be incorporated into the software design process.
- Implementation notes provide additional guidance on how to achieve the outcomes defined in diagnostic statements and may also be incorporated into the software design process.
NIST SP 800-218 (2022), SSDF Version 1.1
NIST introduced its secure SDLC framework in 2021. The Secure Software Development Framework (SSDF) introduces and recommends specific security-focused activities for each phase of the SDLC.
By integrating the recommended activities specified in the framework into the proper lifecycle phase, software developers can reduce security vulnerabilities in newly developed or updated software, lower the effect of security breaches, and identify possible causes of vulnerabilities to better prepare and prevent future breaches or attacks. SSDF includes a vocabulary of terms to facilitate communication among vendors and users.
A key message in the framework is the importance of introducing security issues and requirements as early as possible into the SDLC. Security can no longer be an afterthought. Rather, security should be a central component of any software development project.
SSDF is a matrix based on the following elements:
- Practices are activities recommended to be performed during the development cycle. The four practice groups are defined as follows:
- Prepare the organization activities specify how organizations prepare employees, technologies and relevant processes for secure software development activities.
- Protect the software practices specify how organizations protect software from unauthorized access and malicious actors.
- Produce well-secured software practices define how to produce secure software with few or no vulnerabilities.
- Respond to vulnerabilities activities ensure any remaining vulnerabilities or software risks are addressed and corrected to prevent future vulnerabilities.
- Practice elements are included within each practice matrix. They are defined as follows:
- Practice specifies the practice and includes an identifier for ease of reference, plus an explanation of the practice and why it's needed.
- Tasks are the activities performed in a practice.
- Notional implementation examples are types of tools, processes and methods that help implement a task.
- References are links to specific software development documents that may be relevant to a task.
While traditional SDLC models can be adapted to accommodate security practices, the two secure software development frameworks provide detailed guidance on the security attributes organizations should consider when building secure software products.







