Getty Images
Attention CISOs: Quantum computing security risks are here
The promise of quantum processors solving complex problems at extraordinary speeds offers numerous business opportunities. But what risks does this new technology present?
Quantum computing represents one of the most transformative -- and potentially disruptive -- technological shifts for organizations. However, organizations must also understand the major security threat quantum computing presents.
For CISOs and security administrators, quantum technology isn't a distant issue to monitor casually. It's a key challenge that requires planning and proactive investment to stay competitive and secure. Quantum computing's ability to break popular encryption methods poses several critical security threats:
- Decryption of sensitive data protected by cryptographic algorithms.
- Risks to cryptocurrencies, such as Ethereum and bitcoin.
- Operational disruption as quantum computing renders secure encryption algorithms obsolete.
According to Cisco, quantum computing could threaten modern cryptographic algorithms within the next five to 15 years. It's important to know how quantum computing will revolutionize cybersecurity and how to develop a framework to defend against the cyberattacks of the quantum age.
What is quantum computing?
While computers use bits to process data that are either 0 or 1, quantum computing systems use quantum bits – or qubits -- that can be 0, 1 or both. Quantum computers can process multiple possibilities through quantum superposition and entanglement.
Superposition enables a qubit to be either 0 or 1 simultaneously, while entanglement links multiple qubits together. A set of two qubits could represent four values, letting a computer explore more options and break current cryptographic algorithms in years rather than decades. Because of this risk, the U.S. government's NIST guidelines establish requirements to ensure a mandatory transition to quantum-resistant systems by 2035.
Quantum computing in cybersecurity
Quantum computing isn't purely a threat. It also provides defensive opportunities.
Enterprise adoption of quantum-safe measures is limited. According to the ISACA, as of 2025, fewer than 10% of organizations have begun transitioning to formal quantum-safe programs. However, this is changing. Amazon, Google, Microsoft and other tech vendors have announced plans for post-quantum cryptography. The financial and healthcare sectors lead in adoption due to regulatory pressure and data retention needs. Government agencies must comply with NIST's mandates, which puts pressure on vendors to comply with these standards. Most organizations are assessing their situations, but many CISOs lack the budget or technical resources to start transitions.
Quantum computing fundamentals for security leaders
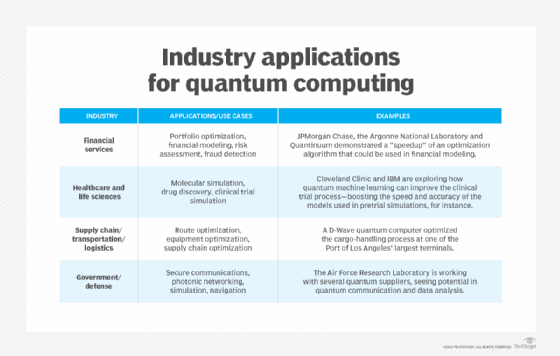
From a security perspective, quantum computing is a dual-edged sword. It can solve complex problems, especially in optimizations and simulations, that conventional computers can't handle. It can also simulate molecular interactions to discover new materials and drugs with unparalleled speed.
Despite these benefits, quantum poses an enormous security risk. A powerful quantum computer could run Shor's algorithm to break the public key cryptography protecting nearly all of today's digital communication. Or it could decrypt Rivest-Shamir-Adleman (RSA)-encrypted data, making the HTTPS protocols obsolete.
CISOs must understand the following two quantum algorithms:
- Shor's algorithm. Unlike today's popular encryption systems, Shor's algorithm can factor large integers exponentially faster than classical methods. RSA, Diffie-Hellman and elliptical curve cryptography (ECC) rely on the difficulty of factoring large numbers. A quantum computer that runs Shor's algorithm could break these encryption methods.
- Grover's algorithm. While Shor's algorithm can break specific encryption systems, Grover's algorithm can accelerate unstructured search problems. It reduces the security strength of encryption schemes by half. This means that AES-256, considered secure against conventional computing threats, would only provide AES-128-level protection against a quantum attacker.
Shor's and Grover's algorithms show the importance of quantum computing in cryptography. However, practical quantum attacks on modern encryption are beyond our capabilities. Today's quantum computers are still in the noisy intermediate-scale quantum era, marked by unstable qubits and high error rates that restrict what they can achieve.
Quantum computing cyberthreats
The development of quantum computing technology will introduce risks to organizations in various areas. The following represent some of the most prominent threats:
Cryptographic attacks
Shor's algorithm could break RSA-2048 encryption in a few hours. Classical computers would require thousands of years to complete the same task. This breakthrough could compromise the security of online banking, e-commerce communications and any RSA-dependent systems.
Consider an individual online banking session. When logging into a bank's online portal, the web browser and the bank's server use RSA-2048 encryption to exchange a secure session key. If a quantum computer running Shor's algorithm could break RSA-2048 in hours, it could intercept and decrypt the initial key exchange, enabling the attacker to access any subsequent data.
Effect on communications
The Secure Sockets Layer and Transport Layer Security protocols secure websites with HTTPS, and VPNs protect remote access. These rely on public-key cryptography to create secure connections. However, a quantum computer running Shor's algorithm could break this encryption and expose all transmitted data.
A secure website or corporate VPN performs a "handshake" using public key cryptography, typically RSA or ECC. During this handshake, they agree on a session key. That key encrypts all further communication using symmetric encryption. A quantum computer could break the public-key encryption used in that initial handshake, intercept the session key being exchanged and decrypt it.
"Harvest now, decrypt later" attacks
Security experts recognize that advanced threat actors, including nation states, organized crime groups and wealthy competitors, are currently gathering encrypted data. They believe quantum computers will arrive, and when they do, all that stored data will be valuable.
Consider these scenarios. An intelligence agency intercepts and stores encrypted diplomatic cables. A competitor steals encrypted trade secrets. A criminal organization records encrypted banking sessions from thousands of customers. None of these attackers can decrypt this data today. However, in five to 10 years, when quantum computing becomes available, they'll be able to decrypt everything.
Blockchain and digital currency vulnerabilities
Bitcoin's security model relies on the Elliptic Curve Digital Signature Algorithm, a type of ECC that verifies ownership of funds and approves transactions. However, a powerful quantum computer using Shor's algorithm could calculate private keys from their corresponding public keys. This would enable an attacker to create fake digital signatures, steal money from wallets, impersonate real users or alter blockchain consensus methods.
Authentication infrastructure breakdown
Modern computing relies on trust. When a device gets a software update, users can trust that it's from the actual vendor. OSes such as Windows and macOS, mobile platforms like iOS and Android and millions of IoT devices, including smart thermostats, routers, cameras and industrial sensors, all use digital signatures to confirm that updates are genuine before installation.
Each software update has a digital signature made using ECC. Devices check this signature before installing the update. If the signature is valid, the device accepts the update as real. A quantum computer could create valid-looking signatures without having the vendor's private key. This could lead to fake updates that pass authentication checks.
Quantum defense strategies and countermeasures
Understanding the quantum threat is only part of the challenge. Organizations need clear defense strategies to protect themselves. Security leaders must put the following countermeasures in place today:
Post-quantum cryptography implementation
The post-quantum cryptography aims to develop cryptographic systems that are secure against both quantum and classical computers, and can interoperate with existing communications protocols and networks.
In response to quantum computing's threat, NIST developed a set of post-quantum cryptography standards that safeguard a variety of electronic data, including private emails and e-commerce transactions. NIST encourages system administrators to switch to these quantum-resistant encryption standards.
Quantum-safe architecture design
With this mitigation strategy, systems are designed from the ground up with quantum threats in mind. A healthcare provider might currently encrypt patient records with AES-256, which is strong according to today's encryption standards. However, Grover's algorithm would reduce its effective strength to that of AES-128. If this organization doesn't increase key lengths or switch to quantum-resistant symmetric algorithms, encrypted patient data could be vulnerable to quantum decryption.
Key architectural changes should include the following:
- Cryptographic agility. Build systems that abstract the cryptographic layer from the system. This enables algorithm swapping without changing business logic.
- Key management modernization. Quantum-resistant cryptography requires managing large encryption keys and complex key exchange mechanisms. Organizations should update their key management practices to handle post-quantum key sizes and rotation requirements.
- Increased key lengths. Organizations should use cryptographic encryption with a large key size. If a company uses AES-128, then it should transition to using AES-256 for better protection against Grover's algorithm.
Risk management framework
Not all data and systems require the same level of quantum protection. A hospital's medical imaging system, which stores RSA-encrypted patient scans, carries different risks than a time-clock system that records employee work hours.
To help develop a quantum risk framework, organizations should consider the following elements:
- Data classification. Identify what data must remain confidential, like medical records, trade secrets and classified information. Session tokens or temporary logs might not require similar protection.
- System criticality assessment. Identify the systems that, if compromised, would cause the most damage. A compromised VPN gateway could expose an entire internal network. This would be a priority for quantum protection.
- Vendor dependency. Identify which third-party vendors provide security services to your organization. If your single sign-on provider gets compromised, how will your systems be affected? Ensure external vendors' critical systems are resistant to quantum attacks.
- Quantum-safe program. CISOs should create a cross-functional, interdepartmental team to guide the efforts for quantum-safe transition.
Nihad A. Hassan is an independent cybersecurity consultant, digital forensics and cyber open source intelligence expert, online blogger and author with more than 15 years of experience in information security research. He has authored six books and numerous articles on information security. Nihad is highly involved in security training, education and motivation.