
tampatra - stock.adobe.com
Protect data with these Azure Key Vault best practices
Enterprises must secure, manage and monitor Azure key vaults correctly to ensure protection. Follow these best practices to effectively protect your data.
Microsoft's Azure Key Vault is a cloud service to store and access secrets such as passwords, API keys, certificates or cryptographic keys. Without the proper security controls, these values might be available to unauthorized users.
Azure Key Vault provides multiple benefits to the organization, including the following:
- centrally controlled secrets distribution;
- secure access to the stored secrets and keys;
- Azure service integration;
- highly available online service;
- scalable platform; and
- simple administration and management.
Organizations must secure their key vaults correctly and monitor them for any unusual behavior. With the Azure service's out-of-the-box tooling, organizations can control access, ensure backups execute, separate secrets, enable logging and ensure recovery options are available. Follow these best practices to secure key vaults.
Use separate key vaults
When you deploy Azure Key Vault, you must choose between single or multiple vaults. Microsoft recommends users keep one vault per application, per environment. For example, use one key vault each for development, pre-production and production within specific regions. This approach will reduce risk and limit sharing of keys and secrets across environments and regions.
The most common approach is to use separate key vaults for each specific application. However, you could group them by services for larger applications as seen in Figure 1.
Control access to the key vaults
One option for security protection is network security. This helps organizations limit vault access by IP address or range. Any user that tries to connect outside the assigned IP address or range gets a denied access message.
The restrictions go even further with firewall rules. The Azure Key Vault firewall has the following four options:
- trusted services only;
- IP addresses and ranges;
- virtual networks using dynamic IP addresses; and
- private link.
You can control access using options within the key vault or directly on the keys, secrets or certificates. For data access at the key, secret or certificate level, use Azure Key Vault access policies.
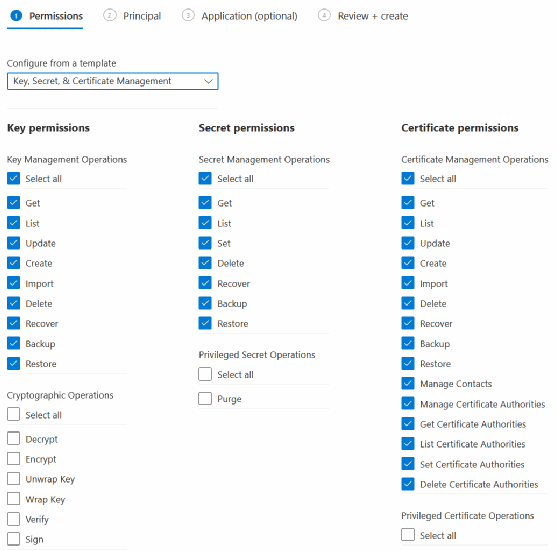
Next, assign the principal for the access policy.
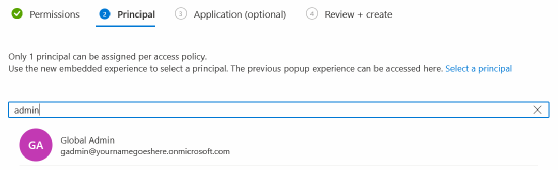
Then, select the Azure Active Directory Role-based Access option for the permission model.
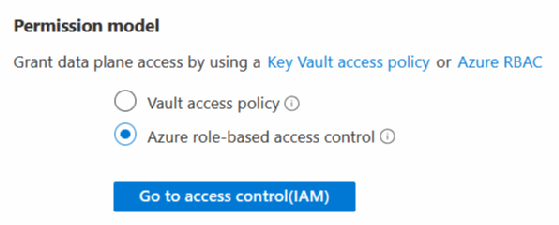
Key Vault also supports Azure Active Directory Conditional Access policies. With Conditional Access policies, you apply access controls to a key vault to keep the organization secure, as seen in Figure 5.
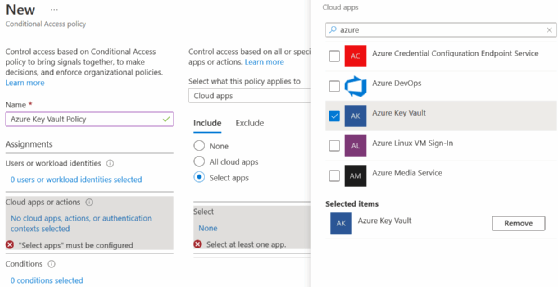
Azure Key Vault supports privileged access control through Azure role-based access control (RBAC). Applications access the endpoint through one of the endpoint groups called planes. Depending on the required plane, the allowed operations differ.
Management plane. Management operations include creating, reading, updating and deleting key vaults. It also includes setting access policies and tags.
Data plane. Data operations include the management of keys, certificates and secrets. Specifically, this provides encryption, decryption, signing, verification, retrieval, creation, updating, deleting, core backup and recovery.
Organizations must manage access using Azure Active Directory (Azure AD). They can scope access with Azure Roles. You must assign the roles to the specific scope, such as the subscription, resource group or a particular resource.
Azure Key Vault example
A practical example of using an Azure Key Vault is storing credentials, usernames, passwords, keys or tokens to access web services within custom application code or even PowerShell. All information stored within the key vault is accessible using the REST API, which is available within multiple programming and scripting languages.
You can easily retrieve stored values within the key vault using PowerShell with the following query:
$secret = Get-AzKeyVaultSecret ' -VaultName "MyKeyVault" ' -Name "MySecret" ' -AsPlainText
When you create a key vault within the Azure Portal, you must determine whether to use the standard or premium tier. Choose the premium service if you require hardware security module support or compliance with Federal Information Processing Standards.
Backup the key vaults
Organizations can recover deleted vaults and vault objects. The backup operation downloads the object as an encrypted blob, such as a secret, key or certificate. You cannot decrypt these downloaded blobs outside of Azure.
At the time of publication, Azure Key Vault doesn't provide the ability to back up an entire vault simultaneously. Organizations must carefully consider the backup of keys, secrets or certificates based on expiration, permissions and rotations. Users must manually back up a key, secret or certificate within the selected object in the key vault.
PowerShell and the Azure CLI also provide backup commands, as shown in the following two sections.
PowerShell backup commands
Set-AzContext -Subscription '9c4c4a01-b9f5-47f4-4b2b-dd034efcc7e7' Backup-AzKeyVaultKey ` -VaultName 'DemoKeyVaultApp' ` -Name 'DemoKey' Backup-AzKeyVaultSecret ` -VaultName 'DemoKeyVaultApp' ` -Name 'DemoSecret' Backup-AzKeyVaultCertificate ` -VaultName 'DemoKeyVaultApp' ` -Name 'DemoKey'
Azure CLI backup commands
az keyvault certificate backup --file 'DemoCert.certbackup' --name 'DemoCert' --vault-name 'DemoKeyVaultApp' --subscription '9c4c4a01-b9f5-47f4-4b2b-dd034efcc7e7' az keyvault key backup --file 'DemoKey.keybackup' --name 'DemoKey' --vault-name 'DemoKeyVaultApp' --subscription '9c4c4a01-b9f5-47f4-4b2b-dd034efcc7e7' az keyvault secret backup --file 'DemoSecret.secretbackup' --name 'DemoSecret' --vault-name 'DemoKeyVaultApp' --subscription '9c4c4a01-b9f5-47f4-4b2b-dd034efcc7e7'
Keep in mind, you can only restore the objects into a vault within the same Azure subscription. However, when you download the objects, you can view them as plain text and import them into any key vault, not just the same Azure subscription.
Purge protection -- via Azure Portal, CLI or PowerShell -- helps prevent a malicious insider's deletion of key vaults, keys, secrets and certificates. At any point, you can recover items during the configurable retention period. Organizational users cannot permanently delete or purge a key vault until the retention period elapses.
Use active logging
Once configured, log entries appear within the Azure Log Analytics workspace service, allowing you to perform a deeper inspection. All log entries are stored as text and formatted as JSON. Azure Monitor provides the core capabilities to monitor and capture core metrics for all key vaults.
Kusto queries provide a more detailed option to query the log entries. The following query returns who accesses the key vault:
AzureDiagnostics | where ResourceProvider =="MICROSOFT.KEYVAULT" | summarize count() by CallerIPAddress








