
Getty Images/iStockphoto
How to approach data loss prevention in virtual servers
As security risks evolve, organizations are turning to data loss prevention tools and methods to combat external and internal risks. Learn how to get started with DLP.
Though IT security issues started with viruses and malware, the rise of cryptocurrency changed everything. Ransomware exploded as it became easier for hackers to profit from exploiting security vulnerabilities.
While ransomware continues to run rampant, the latest evolution in the security race is data theft for profit. And unlike with ransomware, once the data is stolen, backup systems won't help; your data is in someone else's hands.
Security needs are ever changing, driven by balancing risk with what's feasible in terms of costs and resources. As a result, security tools must continue to evolve.
This is where data loss prevention (DLP) comes into play to protect virtual servers.
What is data loss prevention?
DLP is part of a layered security approach that works in concert with other technologies to keep data safe.
DLP isn't another firewall or antivirus system; it involves both software and integrations that detect and stop data breaches and theft, protecting sensitive data from external and internal risks.
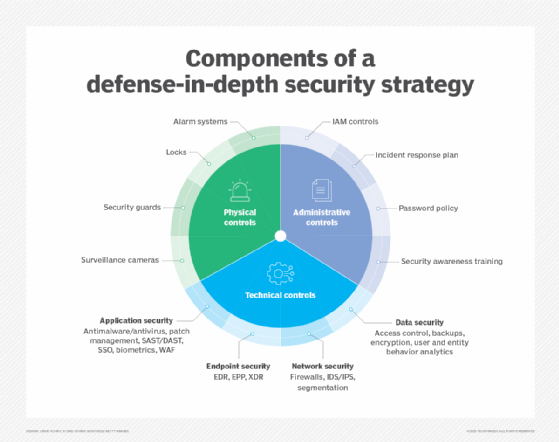
DLP in virtual environments
One of the benefits of virtualization is the ease of rapid workload deployments. IT teams often feel more comfortable using a known virtual template that they can be confident is hardened against security risk.
But as virtual footprints grow, security risks increase, driven by the shift in modern application architecture from vertical silos to horizontal structures. As workloads spread out, organizations' environments include more endpoints as well as more widely distributed data in flight and data at rest.
In a virtual environment, security approaches must be layered, with an intrusion detection system (IDS) working in concert with antivirus software and firewalls to identify and stop undesirable traffic that might result in data theft. Each piece of a security system has a part to play.
But data theft isn't a normal security vulnerability, especially if it comes from an internal threat. Because such traffic can appear normal, monitoring where and when data is moving in the IT environment is essential. Data access from new locations, at odd times after hours and other nonstandard behavior are DLP red flags. However, traditional security tools might not flag such activity as an issue.
Working with DLP tools
Obtaining a complete DLP picture requires combining multiple products -- and price tags, which is where IT teams might see pushback.
Some companies have antivirus software and firewalls but lack an IDS, believing they don't need one. Other organizations have had bad experiences with IDSes, as these applications can sometimes be a choke point on overall traffic. However, IDSes have evolved as the distributed approach has grown.
DLP is essential for all businesses, not just large enterprises
Products such as NSX Intelligence now use a distributed architecture to conduct IDS functions by spreading the load across all hosts, rather than continually trying to scale up. These tools aren't exactly lightweight; NSX Intelligence might be like pounding in a nail with a sledgehammer for any customer but an enterprise company.
But while large enterprises make the news for ransomware and data theft issues, SMBs can be the ideal target for hackers. These groups often don't have the staff or technology resources that an enterprise might. Sure, the payout is much smaller -- but then again, so is the effort, because many SMBs might be unaware of DLP.
Because customers of all sizes are running enterprise-grade virtualization software these days, their applications often have a distributed architecture. Thus, the same problems exist from SMBs to the enterprise: The threat and target systems are the same, even if the use scale is different.
Data protection requires a comprehensive security strategy
The challenge isn't just adding an IDS to an existing system; it's understanding how all the systems interact to ensure data access from both internal and external sources is valid. This takes resources in terms of both people and customizations.
Some vendors offer suites of products that integrate into a central dashboard. However, most are still working on achieving that single pane of glass -- a goal that has always been a challenge with most areas in IT.
With its acquisition of Carbon Black and the introduction of NSX Intelligence, VMware is moving in that direction, but a complete DLP tool will be a bit down the road. This isn't because of a lack of effort on the part of VMware or any other vendor. The fact is, it's difficult for vendors to bring all the security layers under one umbrella. Security tooling still typically involves an ecosystem of needed partners, rather than a single-vendor offering.
The risk is real, and addressing virtual server security concerns with DLP won't be cheap. But embracing more virtual workloads wasn't a mistake. It just took everyone, from SMBs to enterprises, onto the same platform.
This means that flying under the radar isn't a valid business case for security anymore. It's time for all organizations to treat security tools the same way an enterprise does, because now everyone is facing the same security concerns.







