
Getty Images
How network perimeters secure enterprise networks
Network perimeters serve as essential network security to block unwanted traffic. Find out how they differ from the network edge and how they help secure enterprise networks.
Similar to how castle moats and stone walls protected royalty and staff from outside attacks, network perimeters help fortify business LANs from external digital threats.
A network perimeter, which functions as the boundary of an enterprise network, differs from the network edge and secures enterprise networks with various security tools. However, network perimeters are still subject to malicious activity, and network professionals should be aware of the security risks as they manage their networks.
What is a network perimeter?
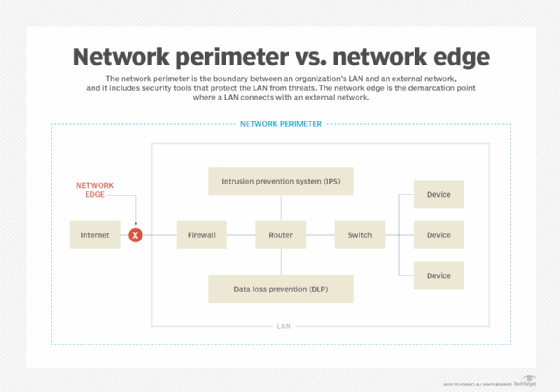
A network perimeter uses various network components to create a secure dividing line between an internal LAN and all external communications. In most cases, external communications refers to data that comes to and from the internet. However, network perimeters can also segment other types of external communications, such as WANs, VPN headends, extranets to third-party partners and Session Initiation Protocol trunks to voice carriers.
The types of equipment used to protect corporate LANs from external threats include routers, network-based firewalls, intrusion prevention systems, data loss prevention, network detection and response, and secure web gateways. Each network security tool identifies and blocks malicious attacks from the outside and permits legitimate traffic to proceed with little to no network performance loss.
Network perimeter vs. network edge
From a corporate LAN perspective, a network edge is the precise demarcation point between the internal and external network. In most cases, the network edge consists of a firewall, secure router or secure software-defined WAN appliance.
A network perimeter refers to network hardware and software architected and deployed to prevent malicious activity from entering the network. In this case, perimeters include all the network routing, switching, security hardware and security software used to fortify and keep network operations safe.
Benefits and drawbacks of the network perimeter
Regardless of an organization's security approach and philosophy, network perimeter security is considered the first line of defense. The main benefit of a network perimeter is that network and security architects have a well-defined location of where to monitor security tools for threat identification and elimination.
The boundary creates a security chokepoint where security tools closely inspect and monitor all traffic. For most businesses, when network professionals focus on a portion of the overall corporate network, they can better track identified threats and manually stop threats at a well-defined area.
However, some drawbacks can occur due to a heavy reliance on a secure network perimeter, such as when threats either find a way through network security tools or originate from inside the network.
In the past, traditional security models commonly assumed that, once data reaches the internal corporate network, the network should trust it. This strategy gives malicious activity the opportunity to move laterally within a network with little prevention. This can lead to situations where a single data breach infects and penetrates an entire network within minutes or even seconds.
To counter the risk of threats within a LAN once the network perimeter has been penetrated, network professionals typically integrate other security tools and methodologies into most modern networks. Other types of tools include client-based security software, zero-trust network access, microsegmentation and more.






