Perimeter security vs. zero trust: It's time to make the move
Perimeter security requires a border to protect enterprise data. With more and more users working outside that border, zero trust promises a better security option for the future.
The growing popularity of cloud and edge computing, combined with an increase in remote workforces, is causing security architects to look for a new approach to identity-based cybersecurity.
The traditional approach of defined security perimeters distinguishing "trusted" from "untrusted" communications is no longer viable. Employees are working outside the traditional castle and moat of the office and firewall, and cloud services equate to large amounts of business traffic never crossing the corporate LAN.
To remedy the situation, organizations can use a zero-trust model for authentication and authorization to better protect business-critical data. Zero-trust philosophies and tools have gained momentum because they are more capable of operating in borderless enterprise environments.
Let's look at perimeter-based security vs. zero trust and explore why organizations may want to migrate to a zero-trust philosophy in the near future.
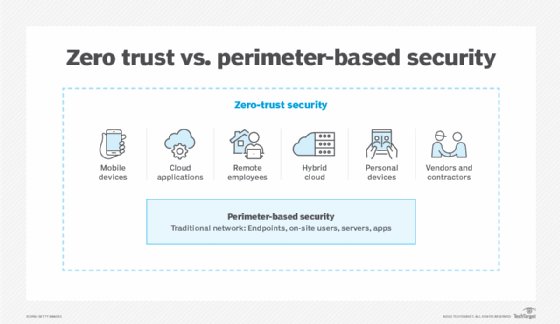
What is perimeter-based security?
Classic network designs were built around the concept of an enterprise LAN consisting of switches, routers and Wi-Fi connectivity. The LAN contained one or more data centers, which housed applications and data. This LAN formed the security network perimeter.
Accessing apps and services via the internet, VPNs and remote sites across WAN connections is considered external to the organization with perimeter-based security. Everything connected to the LAN is considered "trusted," and devices coming from outside the perimeter are "untrusted." This means external users must prove who they are through various security and identification tools.
What is zero trust?
Zero trust is a philosophy and approach to enterprise trust where all users, devices and inter-communications are explicitly untrusted until verified -- and then continuously reverified over time. The security model uses the principle of least privilege to limit what a user or device can communicate with. Zero trust significantly reduces the risk of lateral movement within an organization if a user account or device is compromised.
Microsegmentation plays a role in zero-trust security, as the network itself gets logically segmented into various secure zones, down to the workload level. This is largely useful in data centers, where distributed services are isolated onto secure network segments but outside communications are strictly enforced using security policies.
Why move from perimeter-based security to zero trust?
The biggest problem with perimeter-based security is that it is static in nature. Over the years, apps, devices and users have migrated outside the traditional LAN boundary and, thus, are untrusted from an architectural standpoint.
Perimeter security also suffers from the fundamental flaw that anyone accessing resources from inside the secure perimeter can be trusted. This is a bad assumption, as there are as many internal threats as external ones, as evidenced by the different types of malicious and negligent insider threats.
It makes more sense for an identity-based security strategy to trust no one until they are authenticated and continuously reauthenticated. The zero-trust methodology places all users, devices, apps and communications on the same security playing field. Doing so also enables streamlined policy creation, improved visibility and centralized access control.







